In today’s world of online dangers, using the right tools to protect your system is super important. According to the latest updates, the annual cost of cybercrime globally is expected to reach $10.5 trillion by 2025. You can imagine how much danger your system is in. But, need not worry your system is safe! Pentesting tools are there for you.
“Pentesting tools are the software programs or script that cybersecurity professionals use to test the security of computer systems, networks or applications”.
So, it’s time to explore more with the Pentesting Tools. Stay tuned!
Pentesting Tools: Definition
Pentesting(or Penetration Testing) is a security exercise where a cyber-security expert attempts to find and exploit vulnerabilities in a computer system. It helps in identifying weak spots in a system’s defenses that attackers could take advantage of.
This technique uses tools to examine the target website or system for weaknesses, including open services, application security issues, and open source vulnerabilities. These tools are often called “Pentesting Tools”.
Different Pentesting Tools You Must Know About
1. Kali Linux

Kali Linux is a special kind of computer operating system designed specifically for people who work with computer security. It comes pre-installed with the numerous tools used by security professionals and hackers for various tasks( network discovery, vulnerability analysis, malware analysis, and forensics).
Some of these tools are:

Metasploit – penetration testing framework with thousands of exploit modules
Armitage – graphical network attack management tool
Nmap – port scanner
Burp suite – application security testing
Wireshark – packet analyzer
John the Ripper – password cracker
Sqlmap – automated SQL injection and database import
Aircrack-ng – software suite for wireless LAN penetration testing
OWASP ZAP – web application security scanner
2. Burp Suite

Burp Suite is a set of tools that help people find and fix security problems in websites and web applications. With the help of the burp suite, you can check if a website has any vulnerabilities that hackers could exploit, like weak passwords or ways to steal information. It is mainly used by cybersecurity professionals and ethical hackers to make sure that websites are safe from attacks.
3. Wireshark

Wireshark is a network monitoring solution that captures and analyzes networks across a variety of communication channels. It’s like peeking into the conversations between your computer and different devices on your network.
Wireshark enables penetration testers to investigate security issues on a network and identify elements of the network that are malfunctioning (fail to operate normally) and could be exploited in an attack.
4. John the Ripper

John the Ripper is a powerful password-cracking tool (pen-testing tool) designed to uncover weak passcodes by trying different combinations until it finds the correct one. It supports 15 operating systems, including 11 from the Unix family, DOS(the operating system that runs from a disk drive), Win32( A 32-bit Windows version), BeOS(It was designed for multitasking multithreading), and OpenVMS (vendor management system).
The tool has many options for password testing, including:
- Auto-detection of password hash types.
- Ability to crack password encryption based on DES, MD5, Blowfish, and MD4.
- Support for password hashes and passwords stored in databases and directory systems(LDAP(Lightweight Directory Access Protocol) and MySQL).
5. Hashcat

Hashcat is a password recovery tool. It does this by combining multiple highly effective password-cracking methods. The main technique used in Hashcat is manipulating hash keys generated by algorithms like MD5, SHA, WHIRLPOOL, RipeMD, NTMLv1, and NTMLv2.
Like other pentesting tools, it’s important to use Hashcat responsibly and legally, for things like testing the strength of your own passwords or accessing the security of your system.
6. Nmap

Nmap is a free tool used for network security assessment and investigation. It sends out signals to all devices connected to your network and listens to their responses. Meanwhile, it creates a map showing you what devices are there, what services (email or web servers) they are running, and even how secure they are.
Common tasks performed by Nmap are:
- Checking for open ports.
- Observing host uptime.
- Discovering network assets.
- Overseeing network administration tasks.
7. Invicti

Invicti(formerly known as Netsparker) is a friendly hacker that keeps your website safe from real hackers. It runs a Chrome-based crawler to find vulnerabilities in a variety of web assets including dynamic web applications, HTML 5 websites, and single-page applications.
Key features of Invicti include:
- Scheduled vulnerability tests
- Database security auditing
- Creates detailed reports that can form part of a penetration test report.
- Asset discovery and detection
- Identifying vulnerable versions of languages and web frameworks.
Why Pentesing Tools are Important?

Security threats are constantly evolving, and new vulnerabilities emerge every day. Penetration tools help identify these potential vulnerabilities by simulating real attacks on the target environments.
Ethical hackers assess the security controls in place and identify gaps that could lead to cyber-attacks. By finding and fixing these weaknesses before hackers can find them, penetration testing helps keep data safe and makes sure the system stays safe. It’s like a regular health checkup for the computer system.
Challenges of Pentesting tools:
- Pentesting tools focus on specific types of problems and might miss others. They might not understand unusual steps.
- Systems change all the time, but pen-testing tools might not upgrade accordingly.
- Some pentesting tools cost a lot of money.
- Modern attackers use sophisticated methods. Simulated attacks in pen tests must keep pace.
- While tools like vulnerability scanners are essential, overreliance can lead to missed vulnerabilities.
Limitations of Pentesting tools:
- Pentesting tools require time, expertise, and often considerable budgets.
- Sometimes pentesting tools indicate vulnerabilities that don’t pose a genuine risk.
- Pentesting tools might not cover entire networks or all forms of testing that might miss potential threats.
- Pentesting tools require skilled professionals with expertise in cybersecurity and ethical hacking.
- In a constantly changing IT environment, vulnerabilities find today might become irrelevant tomorrow.
Are Ethical Hacking and Penetration Testing the Same Thing?
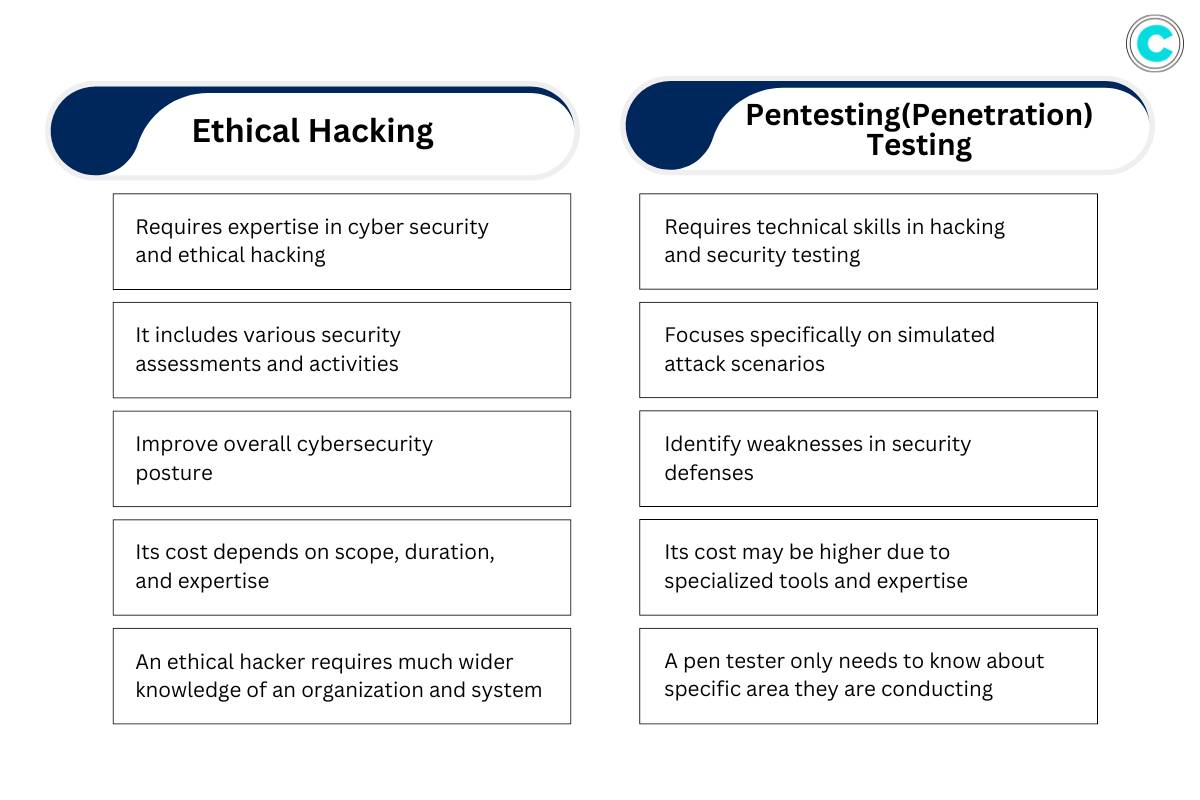
While ethical hacking and pentesting are interconnected and often overlap but they are not exactly. Differences are:
| Ethical Hacking | Pentesting(Penetration)Testing |
| Requires expertise in cyber security and ethical hacking | Requires technical skills in hacking and security testing |
| It includes various security assessments and activities | Focuses specifically on simulated attack scenarios |
| Improve overall cybersecurity posture | Identify weaknesses in security defenses |
| Its cost depends on scope, duration, and expertise | Its cost may be higher due to specialized tools and expertise |
| An ethical hacker requires much wider knowledge of an organization and system | A pen tester only needs to know about specific area they are conducting |
Conclusion:
Understanding the importance of pentesting tools is crucial for organizations aiming to fortify their cyber defenses. By integrating pentesting tools with other security measures, organizations can achieve a robust, multi-layered defense against potential cyber threats.






