Every 39 seconds, a cyberattack hits somewhere in the world. In the United States, the stakes have never been higher. In this high-risk environment, cybersecurity incident response is no longer just a…
- Cyber
- Cyber Attacks & Defence
In 2026, endpoint security spending is expected to continue rising as attacks become increasingly di…
Did you know that data breaches cost companies $4.88 million on average in 2024? Is this higher than…
Executives face tougher decisions in 2026 as digital demands continue to rise. A recent report point…
Cyber threats hit harder in 2026 than most companies expected. Reports show over 5,000 confirmed dat…
Digital threats explode daily. Ransomware strikes every 11 seconds, AI phishing evades filters, and …
Most Popular
Most Popular
- AI & Machine Learning
- IoT
- Cloud
If data were money, the internet would be the world’s biggest bank. And every bank needs guards who never sleep. That is where cloud security companies step in. They protect app files, servers, and se…
- Cyber Frauds
What is jailbreaking? The question often arises when people hear about unlocking the hidden side of …
Cyberattacks don’t always start with the main target. Sometimes, they begin somewhere smaller, like …
- Social Media
- Latest Updates
NuHarbor WEI partnership has been announced to expand cybersecurity support for organizations that r…
American financial institutions are strengthening cybersecurity monitoring and response systems as t…
Veea Inc has announced the planned launch of the Veea SecureConnect service through Telcel in Mexico…
A series of coordinated cyber operations disrupted digital platforms and online services early yeste…
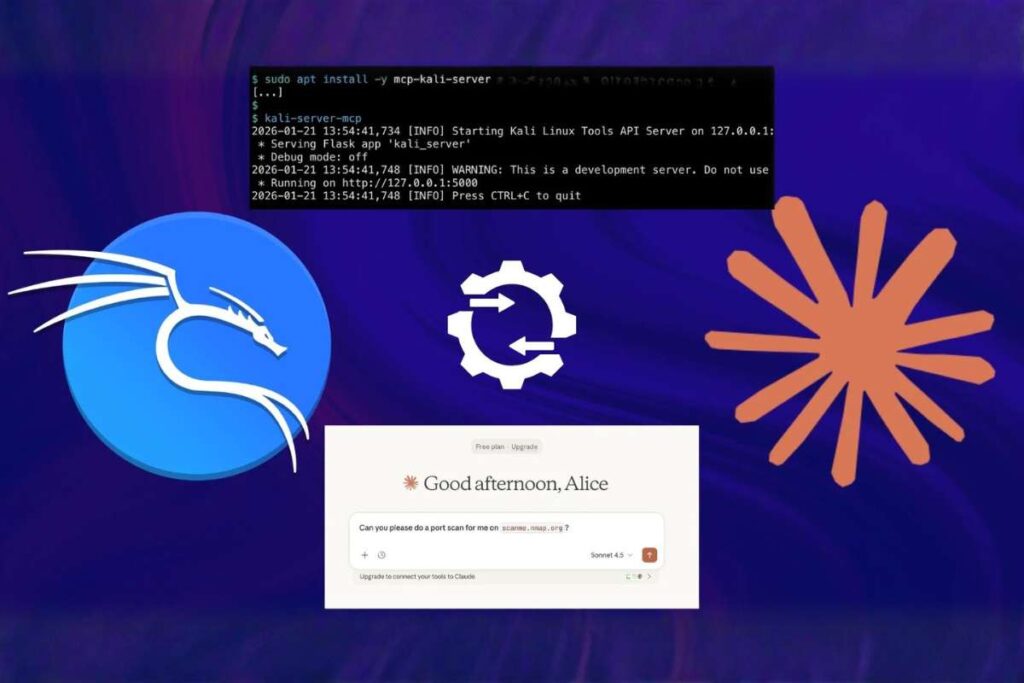
Kali Linux has introduced a native artificial intelligence-assisted penetration testing workflow tha…
The government of the United Kingdom has introduced the UK Vulnerability Monitoring Service along wi…
Cybersecurity firm UpGuard has raised 75 million dollars in a Series C funding round aimed at expand…
Cisco has issued an alert about a critical authentication bypass vulnerability affecting its Catalys…