We have all heard of the Korean DMZ, a 155-mile-long, 2.4-mile-wide strip of land that serves as a buffer zone between North and South Korea. It was created after the Korean War (1950-53). The Korean demilitarized zone is one of the most secure and heavily guarded locations in the world.
But what does a Demilitarized Zone mean in networking and cyberspace? And why does it matter to us and our world? That’s exactly what we will try to learn in this blog.
So, without further ado, let’s try to understand what DMZ is.
What is a Demilitarized Zone (DMZ) in Network Security?
According to the National Institute of Standards and Technology (NIST) in its glossary, a DMZ is “a host or network segment inserted as a ‘neutral zone’ between an organization’s private network and the Internet.”
TechTarget states that a DMZ is “a physical or logical subnet that separates a local area network (LAN) from other untrusted networks—usually, the public internet,” isolating external-facing servers to restrict unexpected access to the internal LAN.
To summarize, a Demilitarized Zone is a network security architecture best practice used to separate and safeguard internal networks from external threats. It does so by placing public-facing services in a controlled and monitored intermediary zone between the internet and the private network.
What are the Key Features that Define DMZ?
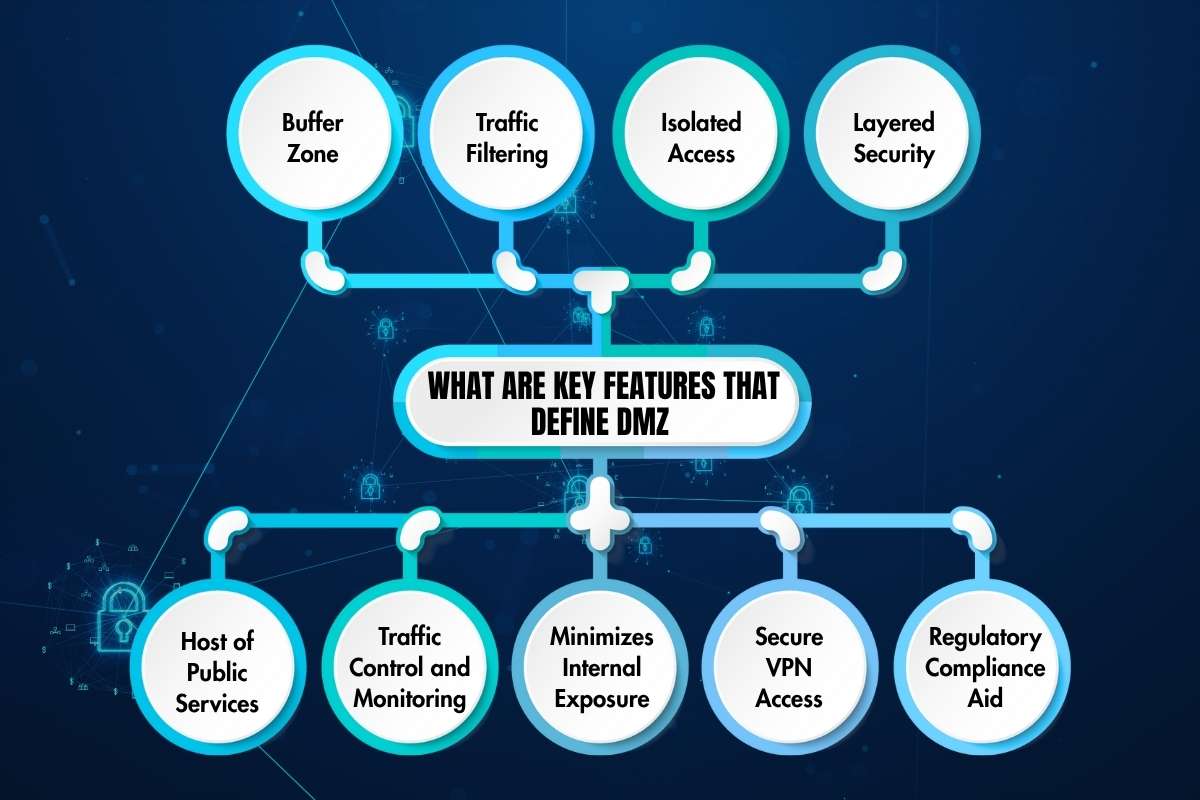
Let’s understand the essential features of every demilitarized zone. Here are the key features of DMZ:
1. Buffer Zone:
A DMZ acts as a buffer between the untrusted external internet and the trusted internal network. It works on isolating public-facing services from sensitive internal systems.
2. Traffic Filtering:
Firewalls control traffic between the Internet, DMZ, and internal network. It allows only authorized access based on predefined security rules.
3. Isolated Access:
External users can access services hosted in the DMZ (e.g., web servers, mail servers, DNS), but cannot directly access the internal corporate network.
4. Layered Security:
Usually involves dual firewalls—one between the internet and DMZ, another between DMZ and internal LAN. This provides layers of protection.
5. Host of Public Services:
The DMZ typically hosts servers that need to be accessible from the internet, like web, email, FTP, and VoIP servers, while protecting internal resources.
6. Traffic Control and Monitoring:
Includes perimeter routers and security gateways to monitor and filter traffic. It often integrates intrusion detection systems (IDS) and load balancers.
7. Minimizes Internal Exposure:
Even if a DMZ server is compromised, the internal network remains protected due to firewall segregation and strict access control.
8. Secure VPN Access:
DMZs sometimes act as a secure landing point for VPN connections. This allows safe remote access without exposing internal systems directly.
9. Regulatory Compliance Aid:
DMZs can simplify compliance requirements by isolating sensitive data systems from public access points. This aids secure monitoring and logging.
Five Central Types of DMZs and their use cases:
There are five central types of demilitarized zones in cyberspace. These types vary in complexity, cost, and security level. Organizations select a Demilitarized Zone architecture based on their specific security needs, resources, and network design.
Here’s what they are:
| DMZ Type | Architecture | Key Features | Security Level | Ideal For |
|---|---|---|---|---|
| Single Firewall DMZ (Three-Legged) | One firewall with three interfaces (Internet, Internal, DMZ) | Cost-effective, easy to manage | Moderate (single point of failure) | Small organizations |
| Dual Firewall DMZ | Two separate firewalls (Internet–DMZ, DMZ–Internal) | Layered protection, redundancy | High | Medium to large enterprises |
| Back-to-Back DMZ | DMZ is placed between two firewalls | Two-stage filtering (inbound & outbound) | Very High | High-security environments |
| Screened Subnet DMZ | Dedicated subnet for DMZ with firewall rules | Granular control and flexibility | High | Complex networks that need fine control |
| Host-Based DMZ | Individual servers act as a DMZ with host firewalls | No separate network, simple setup | Low–Moderate | Small or budget-limited setups |
How Do You Implement a Secure Demilitarized Zone Step by Step?

Now that we know the features, types, and definition of Demilitarized Zone, let’s learn how to implement it. Here’s a step-by-step guide on how to implement it:
Step 1: Plan Your DMZ Architecture
Decide between a single firewall and a dual firewall setup. Establish the services you need in the DMZ, such as web servers, mail servers, or FTP servers. Define clear zones: internal network, DMZ, and external internet.
Step 2: Prepare Network Equipment
Ensure the availability of firewalls, routers, and switches to segment the network. Configure the hardware to support multiple network interfaces for segregating traffic.
Step 3: Create Network Segments
Set up a distinct subnet for the DMZ, separate from the internal network and external internet. Assign IP ranges to the DMZ that are different from the internal network.
Step 4: Configure Firewall Rules (External to DMZ)
Set firewall rules to allow inbound traffic from the internet to the DMZ only for necessary services and ports (e.g., HTTP, HTTPS, SMTP). Block all other inbound traffic.
Step 5: Configure Firewall Rules (DMZ to Internal Network)
Restrict traffic from the DMZ to the internal network to only what is necessary. Typically, deny all unsolicited inbound traffic from the DMZ to internal devices.
Step 6: Deploy Server and Services in DMZ
Install and configure servers (web, email, FTP) within the DMZ subnet. Harden these servers by applying security patches and disabling unnecessary services.
Step 7: Enable Monitoring and Logging
Set up network monitoring and logging on firewalls and DMZ servers. Regularly review logs for suspicious activity.
Step 8: Test DMZ Security
Perform penetration testing to verify firewall and server configurations to block unauthorized access. Test access to public services hosted in the DMZ for proper functionality.
Step 9: Maintain and Update
Regularly update firewall rules, server patches, and monitoring tools. Review DMZ configuration periodically to adapt to new security threats.
Also Read: Data Tokenization Explained: The Smart Security Move Every Business Should Make
Benefits and Disadvantages of Demilitarized Zones

| Benefits of a DMZ | Aspect | Disadvantages of a DMZ |
|---|---|---|
| Isolates public-facing servers from internal networks, reducing the risk of internal breaches. | Security | It can create a single point of failure if not properly configured with redundancies. |
| Allows external users to access necessary services (web, email) without exposing internal systems. | Access Control | Strict access controls may limit legitimate external access or integrations. |
| Filters and monitors incoming traffic, preventing attacks like IP spoofing and reconnaissance. | Attack Protection | The complex setup requires expertise to ensure all protection mechanisms are correctly configured. |
| Limits damage if DMZ servers are compromised—internal network remains shielded behind firewalls. | Internal Network Exposure | Increased maintenance is needed to keep configurations updated and effective. |
| Supports compliance with data protection standards through network segmentation. | Regulatory Compliance | Additional hardware and software increase setup and operational costs. |
| Enables load balancing and secure VPN access, improving performance and remote connectivity. | Performance and Reliability | Adds administrative overhead due to continuous monitoring and testing requirements. |
How Does the Demilitarized Zone Work in Real-Life Cybersecurity?
Demilitarized Zone is quite useful in various forms. It helps you protect, defend, and streamline your cyberspace.
Organizations host web servers, email servers, FTP servers, and other public-facing applications in a DMZ. This allows external users to access these services while protecting the internal network from attacks if the public servers are compromised.
DMZs are used in hybrid cloud architectures to isolate cloud services accessed publicly from internal resources. This helps in securing sensitive data and infrastructure.
Critical systems controlling infrastructure are separated using DMZs to prevent direct external access while allowing monitoring and control traffic.
Also Read: Can Secure Sockets Layer Truly Protect Your Data in 2025?
Conclusion:
The Demilitarized Zone (DMZ) in cyberspace is your organization’s essential security buffer, much like its physical counterpart. It’s the network security best practice that places public services like websites and email behind a controlled zone.
By deploying a demilitarized zone, you create a critical layer of defense, ensuring that even if an external-facing server is compromised, your sensitive internal network remains protected. Ultimately, the DMZ minimizes risk, secures access for users, and helps maintain the integrity and safety of your digital world.
FAQs
1. How does a DMZ differ from a proxy server?
A DMZ segments a network. A proxy acts as an intermediary for requests.
2. Is a DMZ mandatory for home networks?
No, it is generally unnecessary for home networks.
3. What is a common security risk in a DMZ?
Misconfigured firewall rules are a major risk for demilitarized zones.