Have you ever clicked a suspicious link and instantly regretted it? Or wondered if that “update later” button might actually put your data at risk? If so, you’re not alone. Most of us slip up when it comes to online safety. So, we need to be mindful of our actions when we are on the internet.
Just like brushing your teeth keeps you healthy, good cyber hygiene keeps your online life safe and secure. Think of it as your digital self-care routine. It’s all about building smart habits like using strong passwords, updating your devices, and staying alert for scams.
Since almost everyone has some form of digital footprint, anyone can be targeted by cyber hackers and attackers. That is why a few small steps every day can protect your data, privacy, and peace of mind. In this blog, we’ll look at what good cyber practices for digital hygiene are, their importance, and how you can easily practice it to stay safe online.
What is the Importance of Cyber Hygiene?
Cyber hygiene keeps your digital life safe and organized. It builds habits that protect personal and business data from cyber threats. Just like daily routines keep your body healthy, these practices protect your online systems.
Poor cyber practices can lead to stolen passwords, data leaks, and malware infections. A single weak password or old software can open doors for hackers. Regular updates, careful email use, and data backups reduce these risks.
For organizations, strong cyber protection keeps customer trust intact. A single breach can damage reputation, cause financial loss, and break compliance laws. When employees follow cybersecurity rules, the whole system stays secure.
Good digital hygiene also supports smooth operations. Fewer system crashes, faster devices, and less downtime mean more productivity. In short, it protects both people and profits.
Key Cyber Hygiene Practices You must not overlook
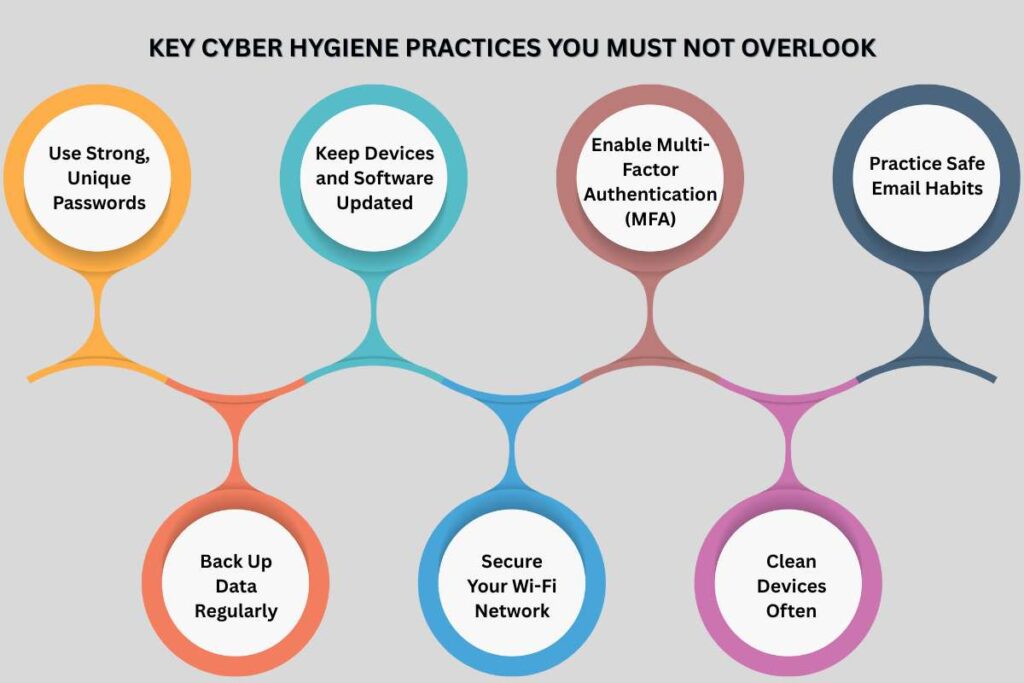
1. Use Strong, Unique Passwords
Create passwords that mix uppercase, lowercase, numbers, and symbols. Avoid personal details like names or dates. Use a password manager to remember complex ones.
Never reuse passwords across accounts. If one leaks, others stay protected. Change passwords every few months, especially for banking or work accounts.
2. Keep Devices and Software Updated
Updates fix security gaps that hackers often exploit. Always turn on automatic updates for your computer, phone, and apps.
Don’t ignore update reminders. They’re not just for new features—they also strengthen your defenses against cyberattacks.
3. Enable Multi-Factor Authentication (MFA)
Also Read :- The Importance of Multi-Factor Authentication: Protecting What Matters Most
MFA adds another barrier to hackers. Even if someone steals your password, they can’t log in without the second code or fingerprint.
Use MFA for email, cloud storage, and online payments. It’s one of the simplest ways to boost security.
4. Practice Safe Email Habits
Email is the most common tool hackers use. Good cyber hygiene starts with checking messages carefully.
Look at the sender’s email address. Fake addresses often look slightly different from real ones. Avoid clicking on unknown links or downloading attachments from strangers. Use spam filters and report suspicious messages. A few seconds of checking can prevent hours of damage control.
5. Back Up Data Regularly
Backups protect you when things go wrong. Store copies of files on external drives or cloud storage. If your system crashes or gets infected, you can restore everything without paying a ransom or losing data. Schedule automatic backups weekly or daily.
6. Secure Your Wi-Fi Network
Change the default password on your router. Use strong encryption like WPA3. Don’t share Wi-Fi passwords openly or display them in public areas. When using public Wi-Fi, use a VPN to hide your data. Avoid logging into sensitive accounts on open networks.
7. Clean Devices Often
Delete unused apps, temporary files, and old downloads. These files take up space and may hide security risks. Keeping your system clean improves speed and lowers the chance of malware spreading. Treat it like tidying your workspace, small actions that prevent big issues.
SOP for Good Cyber Hygiene in Organizations

According to IBM, the global average cost of a data breach in 2025 is USD 4.44 million. As these threats rise, protecting your digital space has become a necessity. Hence, we have provided a guideline on how you can improve digital hygiene.
An SOP (Standard Operating Procedure) helps organizations maintain consistent digital hygiene. It outlines the steps everyone must follow to keep systems secure.
Step 1: Set Clear Policies
Define password rules, device use, and data handling standards. Make sure all employees read and acknowledge these policies. Keep them short and easy to follow. Complex rules often lead to mistakes.
Step 2: Conduct Regular Training
Hold short sessions every quarter to refresh knowledge. Use real-life examples like phishing tests or fake scam emails. Show employees how to report suspicious activity. Awareness prevents panic and builds confidence during threats.
Step 3: Implement Access Controls
Give employees access only to what they need. Remove permissions for those who change roles or leave the company. This “least privilege” rule reduces the risk of data leaks or accidental exposure.
Step 4: Monitor and Respond Quickly
Use security tools to track unusual activity. If a login happens from an unknown location or time, check immediately. Create a clear reporting line for cyber incidents. Every minute counts when stopping an attack.
Step 5: Keep Systems Updated
All company devices must have automatic updates turned on. IT teams should verify updates weekly and report completion. Unsupported software should be removed or replaced. Old systems are favorite targets for hackers.
Step 6: Email Security SOP
Emails are the easiest entry point for attackers. Include these steps in daily practice:
- Always verify sender details before replying or downloading attachments.
- Report suspicious messages to IT immediately.
- Never send passwords or personal data through email.
- Avoid clicking “unsubscribe” links in strange messages—they can be traps.
Also Read : What You Don’t Know about Email Security Protocols Could Cost You Millions?
Step 7: Back Up and Encrypt Data
Schedule automated backups for critical systems. Store copies on both local and cloud storage.
Use encryption for sensitive data, so even if stolen, it remains unreadable.
Step 8: Promote Continuous Learning
Encourage staff to take short cybersecurity courses. Reward those who follow good practices.
A positive culture helps employees see cyber hygiene as teamwork, not just another task.
Step 9: Audit and Improve
Perform system checks every six months. Review access logs, password strength, and security software. After each audit, update the SOP with lessons learned. Cyber threats change fast, so your plan should too.
This step-by-step SOP ensures everyone in the organization understands their role in protecting data.
How to Prevent Attacks before they Start?
Good cyber hygiene is about prevention. When passwords, updates, and email habits are strong, attackers have fewer entry points. Preventive habits save money and protect both data and reputation. They also reduce downtime caused by cyber incidents.

Email Hygiene and Email Bombing Prevention
Email bombing happens when someone floods an inbox with thousands of messages. The goal is to crash email systems or hide real malicious emails among the spam.
Practicing email hygiene can stop or reduce these attacks. Here’s how:
1. Use Spam Filters and Firewalls:
Advanced filters detect and block mass email bursts before they reach inboxes.
2. Limit Form Submissions and Public Email Display:
Don’t post contact emails openly on websites. Use contact forms with CAPTCHA to stop bots.
3. Set Rate Limits:
Configure your email server to limit how many messages one sender can deliver per minute. This reduces the impact of bombing attempts.
4. Train Employees to Identify Bombing Signs:
A sudden flood of emails isn’t normal. Teach staff to report unusual volume right away.
5. Separate Work and Personal Accounts:
Using separate accounts helps isolate important emails from spam. It also makes it easier to clean up after an attack.
6.Avoid Subscribing to Unknown Lists:
Many email bombs come from signing up for fake newsletters. Always check the source before subscribing to anything online.
With strong cyber hygiene, email bombing attempts fail to overwhelm systems. Employees know what to do, filters block fake messages, and response times stay quick.
7. Data Backup and System Recovery
When an attack happens, regular backups make recovery easy. Instead of paying ransom or losing work, teams can restore systems quickly. This is why backups and cyber hygiene always go together, as both aim to prevent chaos.
8. Role of Monitoring Tools
Monitoring tools detect sudden changes like a surge in email traffic or failed login attempts.
By acting early, IT teams can block IPs, isolate accounts, and stop damage before it spreads.
Also Read :- What Are the Top Cloud Security Tools for 2025? | CyberPro Magazine
Case Study: Qantas Data Breach 2025

Incident:
In July 2025, Qantas Airways experienced a significant cyberattack that compromised sensitive customer data, including phone numbers, birth dates, and home addresses. The breach was traced back to vulnerabilities in a third-party platform used by the airline.
Also Read case Study : – Qantas Confirms Customer Data Leaked Following July Cyber Breach
Lessons Learned:
This incident underscores the importance of Cyber Hygiene and maintaining robust digital hygiene practices, such as ensuring the security of third-party services and regularly updating and patching systems to prevent unauthorized access.
Conclusion:
Strong cyber hygiene is key to staying safe from cyber threats. By taking simple, consistent steps, you can protect your data, devices, and privacy while navigating the digital space with confidence. Good cyber practices can help you prevent breaches, identity theft, and online scams, keeping both your personal and professional life secure.
FAQ
1. Is cyber hygiene only for tech experts?
A. No, anyone who uses digital devices can practice Cyber Hygiene. Simple habits can make a big difference in safety.
2. What role do strong passwords play in cyber hygiene?
A. Strong, unique passwords reduce the risk of unauthorized access and are a foundational part of digital safety.
3. Can cyber hygiene protect against phishing attacks?
A. Yes, being cautious with emails, links, and attachments is a core part of cyber hygiene and helps prevent phishing.1.






