You create a small digital footprint each time you click, type, or swipe. These traces reveal information about our whereabouts and activities in our high-tech world. What is digital forensics? Finding and storing this data is a clever science that helps solve crimes. Just like a detective looks for fingerprints at a house. These experts look for clues inside computers and phones to find the truth.
Today, cyber threats are growing faster than ever. Digital forensics helps law enforcement capture hackers, keeps businesses safe, and builds global trust. Experts can prevent bad actors and protect our secrets by analyzing the vast amounts of data we produce.
What is Digital Forensics?
Digital forensics is the scientific process of finding and saving data to use as evidence in court. Professionals accurately gather, store, and examine data from gadgets. Such as laptops and phones. To ensure that the facts are “legally admissible.” Or that a judge can rely on the information, they must adhere to strict guidelines.
To simply answer the question, what is digital forensics? Digital forensics encompasses everything from cloud storage to Smartwatches. Whereas “computer forensics” primarily concentrates on PCs. This work is essential for catching hackers in cybersecurity. This helps law enforcement solve crimes and assists businesses in resolving significant legal disputes. Experts protect our digital world by transforming messy data into unambiguous proof.
History and Evolution of Digital Forensics:
To better understand what is digital forensics, it helps to look at its origins. In the 1980s, digital forensics began as “computer forensics” when investigators first realized that PCs held vital clues. Back then, methods were simple and unorganized. However, as technology boomed in the 1990s, the field moved from experimental tricks to formalized procedures. This shift ensured that digital evidence could be trusted in a court of law.
The discipline exploded with the rise of smartphones, cloud computing, and the Internet of Things (IoT). These tools meant that evidence wasn’t just on a desk anymore; it was everywhere. To keep up, global frameworks and professional bodies like the IACIS were created. Today, experts must earn specialized certifications to prove they can handle data across global networks. This evolution clearly shows what is digital forensics today, a high-stakes science that protects our modern, connected world.
Here are Some Intriguing Types of Digital Forensics:
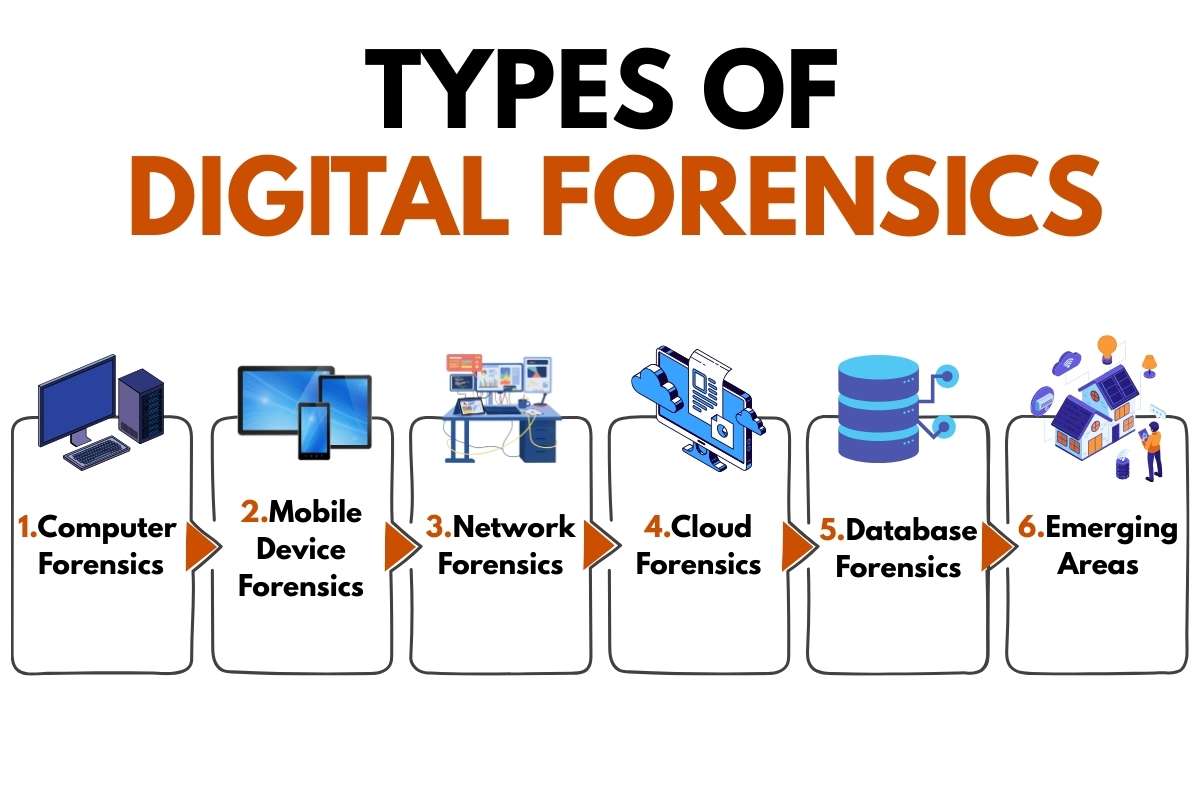
Digital forensics is a broad field with specialized branches for different types of technology. Here is how the discipline is categorized:
1. Computer Forensics
This is the foundation of the field. It focuses on gathering evidence from desktops, laptops, and servers. Investigators look at hard drives and deleted files to reconstruct a user’s past actions.
2. Mobile Device Forensics
As we move away from PCs. This branch analyzes phones, tablets, and wearables, like Smartwatches. It uncovers GPS locations, text messages, and app data. This reveals where a person has been and who they talked to.
3. Network Forensics
This involves monitoring network traffic and logs. Instead of looking at a device. Experts watch the “data in motion” to see how a hacker entered a system or where stolen information was sent.
4. Cloud Forensics
With so much data stored on the internet. This branch deals with virtual environments like Google Drive or AWS. It is tricky because the physical servers are often located in different countries.
5. Database Forensics
This specialty looks at transaction logs and structured metadata. Experts use it to track down “insider threats.” Such as an employee who might be changing financial records or stealing customer lists.
6. Emerging Areas
New technology brings new challenges, which expand the scope of what is digital forensics:
- IoT Forensics: Pulling data from smart fridges or home security cameras.
- AI/Media Forensics: Detecting deepfakes and verifying if a photo or video is real.
- Vehicle Forensics: Analyzing data from modern cars to see speed and braking history.
An Overview of the Digital Forensics Process:
What is digital forensics process? It is a strict, step-by-step journey. Experts must follow these rules exactly so that the evidence they find is trusted by a court or a boss.
1. Identification
The first step is playing detective. Investigators must figure out where the data is hiding. This could be on a computer, a thumb drive, a phone, or even a digital camera. They identify all the devices that might hold clues.
2. Preservation
This is the most important part. To keep the data “clean,” experts make a perfect digital copy of the device. They use special tools to make sure the original data is never changed. This step also involves starting a “chain of custody,” which is a logbook showing exactly who has touched the evidence.
3. Collection
Once the data is safe, it is officially “collected.” This means moving the digital copies to a secure place where they can be studied. Experts use forensic software to pull out hidden or even deleted files.
4. Analysis
Now, the real digging begins. Experts look for patterns and clues. They might check email history, look at when files were opened, or track where a person logged in. They piece together the digital story to see what actually happened.
5. Documentation & Reporting
Finally, the expert writes a clear report. They explain what they found using simple words so that a judge or a jury can understand it. This report must show exactly how they found the proof so that everyone knows the results are fair and true. By providing this detailed evidence, the expert gives a final answer to the question, “What is digital forensics?”
Also Read: What is Transport Layer Security (TLS), and Why is it Important?
These are Some Effective Tools Used in Digital Forensics:
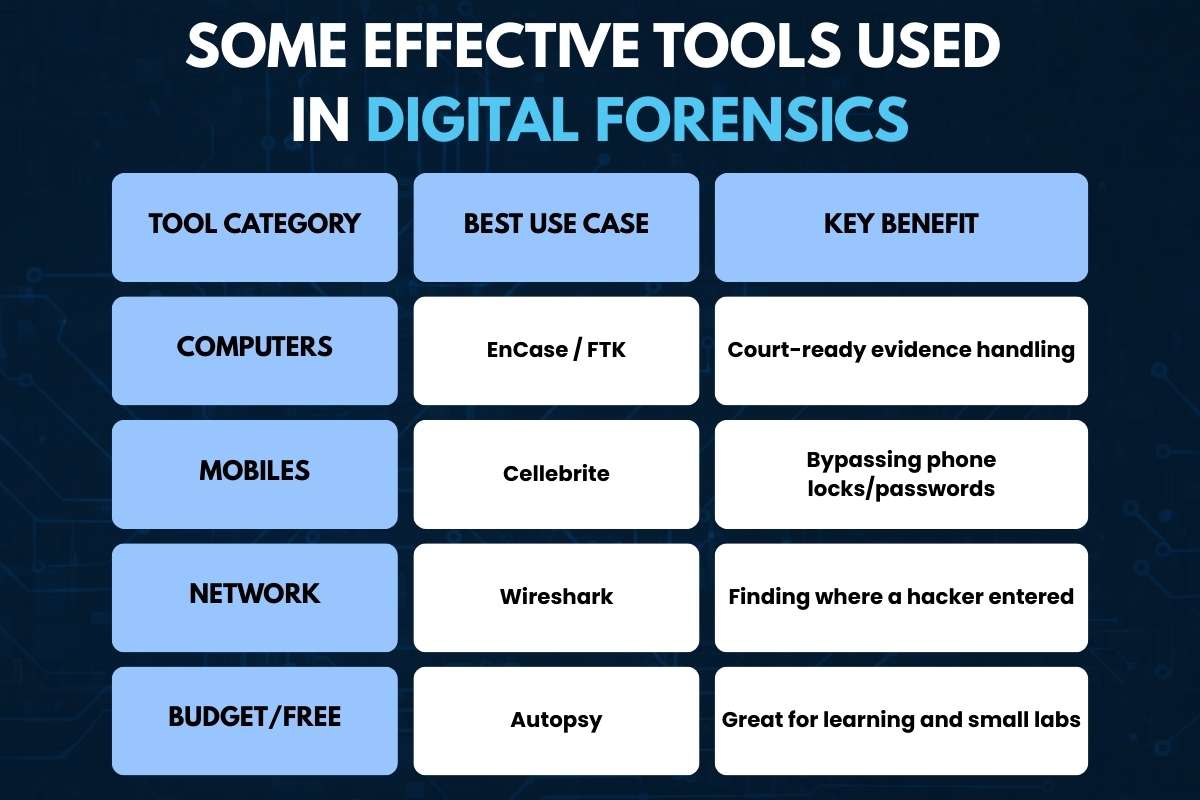
To solve digital crimes, investigators use a variety of specialized tools. Some are classic software used in labs, while others are built for the field
| Tool Category | Best Use Case | Key Benefit |
| Computers | EnCase / FTK | Court-ready evidence handling |
| Mobiles | Cellebrite | Bypassing phone locks/passwords |
| Network | Wireshark | Finding where a hacker entered |
| Budget/Free | Autopsy | Great for learning and small labs |
➤ Disk Imaging & Extraction
These tools make perfect copies of hard drives so the original data stays safe.
- EnCase: Known as the “gold standard” for law enforcement. It is very powerful and trusted in court, but it can be expensive and hard to learn.
- FTK (Forensic Toolkit): Famous for being incredibly fast. It can scan massive amounts of data quickly, though it requires a very powerful computer to run smoothly.
➤ File and Memory Analysis
Once a copy is made, these tools help experts look through the files.
- Autopsy: A great “all-in-one” tool that is free and easy to use. It’s perfect for beginners or smaller cases.
- The Sleuth Kit: This is the “engine” behind Autopsy. It uses command-line (typing) to dig deep into hidden parts of a computer’s memory.
➤ Mobile & Network Forensics
These tools handle phones and “live” internet data.
- Cellebrite: The top choice for getting into locked iPhones and Androids. It is very reliable but carries a high price tag.
- Oxygen Forensic Detective: Excellent for pulling data from apps like WhatsApp or cloud storage. It is updated often to handle the newest phone software.
- Wireshark: A free tool used to watch data move across a network. It’s best for catching hackers in the act, though it takes practice to understand all the technical details.
Applications of Digital Forensics in the Real World:

When asking what is digital forensics? It is important to realize it is much more than just a tool for the police. It is a vital part of keeping our modern world running smoothly by protecting our information and finding the truth. Here are the four main ways it is used today:
1. Law Enforcement & Criminal Justice
Digital forensics has transformed how crimes are solved, moving far beyond “hacker” cases.
- Reconstructing Timelines: Investigators use GPS data and social media metadata to map a suspect’s movements. This can prove whether someone was actually at a crime scene.
- Recovering Deleted Proof: Specialized “file carving” techniques allow police to find deleted messages or photos that a criminal thought were gone forever.
- Financial Crimes: Forensic accountants and digital experts work together to trace money laundering through “hidden” crypto wallets and encrypted communication logs.
2. Cybersecurity & Incident Response (DFIR)
In the world of IT, forensics is the “CSI” team that arrives after a digital break-in.
- Finding the “Patient Zero”: Experts analyze server logs to find the first computer infected, helping them understand exactly how the hacker got in (the attack vector).
- Memory Forensics: Some hackers use “fileless” malware that only lives in a computer’s active memory (RAM). Forensic tools can capture this data before the computer is turned off, saving evidence that would otherwise vanish.
- Malware Attribution: By studying the code used in an attack, experts can often link it to specific global hacking groups.
3. Corporate Investigations & Insider Threats
Businesses use forensics to protect their secrets and handle internal disputes.
- Intellectual Property (IP) Theft: If a departing employee steals a client list or a secret recipe, forensics can track the USB drive they used or the personal email they sent it to.
- Employment Disputes: In cases of wrongful termination or harassment, forensics provides objective proof of what was said in “deleted” chats or company emails.
- Data Exfiltration Tracking: Experts determine exactly what files were moved, how much data was stolen, and who accessed it.
4. Legal & Regulatory Compliance
With strict laws like GDPR (Europe) and CCPA (California), forensics is a shield for companies.
- Audit Trails: When a data breach happens, companies must prove they had security in place. Forensic reports provide a “paper trail” showing the company followed the law.
- Data Minimization: Experts help companies find and delete “unnecessary” personal data to stay compliant with privacy laws, reducing the risk of huge fines.
- Expert Testimony: Forensic specialists often serve as expert witnesses in court, explaining complex technical facts in simple terms to help a jury make a fair decision.
Also Read: Can Secure Sockets Layer Truly Protect Your Data in 2025?
Here Are Some of the Common Challenges in Digital Forensics:

While digital forensics is a powerful tool, experts in 2026 face a “perfect storm” of technical and legal hurdles. As criminals get smarter, the field must constantly adapt to overcome these five major challenges:
1. The “Going Dark” Problem (Encryption)
Encryption is a double-edged sword. While it protects our privacy, it also hides criminal activity.
- The Challenge: Many modern devices use Full-Disk Encryption (FDE), and apps use End-to-End Encryption (E2EE). If an investigator cannot get the passcode, the data remains a scrambled, unreadable mess.
- Example: In many cases, success rates for decrypting seized devices can be as low as 15–20% without the owner’s cooperation.
2. Massive Data Volumes
We are living in the age of “Big Data,” and forensic labs are drowning in it.
- The Challenge: A single smartphone today can hold 1TB of data. Analyzing dozens of devices in one case creates a “bottleneck” that can delay trials for months.
- The Solution: Experts are turning to AI-augmented analysis to quickly sort through millions of files to find the few that actually matter.
3. Cross-Border Legal Issues
The internet has no borders, but laws do.
- The Challenge: A crime might happen in New York, using a server in Germany, with data stored in a cloud managed by a company in Singapore.
- The Conflict: Investigators often face “jurisdictional friction,” where different countries’ privacy laws (like GDPR in Europe) prevent data from being shared quickly across borders.
4. Rapid Tech Advancement
Technology moves faster than the law and forensic training.
- The Challenge: New frontiers like AI deepfakes and quantum computing are emerging. Experts must constantly learn new skills to prove if a video is real or if a hacker used an AI “bot” to break in.
- Expert Insight: The World Economic Forum 2026 report notes that AI is now the top driver of change, helping both the “good guys” defend and the “bad guys” attack.
5. Anti-Forensics & Data Volatility
Some criminals use “anti-forensic” tools specifically designed to frustrate investigators.
- Techniques: This includes steganography (hiding files inside other files) and “wiping” software that overwrites deleted data so it can never be recovered.
- Volatility: Much of today’s evidence lives in a computer’s “volatile” RAM. If the power is cut before the memory is captured, that evidence vanishes forever.
“The growing use of default encryption can hinder law enforcement’s ability to access evidence… leaving a ‘wall’ that traditional tools cannot break.”
European Parliament Briefing, 2025.
Conclusion:
Digital forensics is the best defense in our fast-paced world. It transforms hidden clicks into unmistakable evidence. This science needs to advance even more quickly in order to thwart hackers using new techniques like artificial intelligence. Every byte, from your phone to the vast cloud, tells a tale that can safeguard your privacy and safety.
What is digital forensics, then? In a digital world, it is essential to learn the truth. These professionals will be there to follow the trail as long as we leave footprints.
FAQ:
1. What is digital forensics in simple terms?
Digital forensics is the process of finding, preserving, and analyzing data from digital devices. Such as computers, smartphones, and servers, to uncover facts or evidence. It helps investigators understand what happened, when it happened, and who was involved, using data in a legally acceptable way.
2. Why is digital forensics important today?
Digital forensics is critical because most activities, whether they are personal, business, or criminal. They can leave digital traces. It plays a key role in cybercrime investigations, data breach analysis, fraud detection, and legal disputes, helping organizations and authorities make evidence-based decisions.
3. How is digital forensics different from cybersecurity?
Cybersecurity focuses on preventing attacks, while digital forensics focuses on investigating incidents after they occur. Digital forensics often works alongside cybersecurity to identify attack methods, assess damage, and support legal action.