Recently, Safelife’s Web Application Firewall an innovative open-source solution that is designed to safeguard web applications for small and medium enterprises to reduce cyber threats, faced some challenges. These challenges are related to the increasing Generative AI and automated web traffic. Generally, IT businesses face challenges like disrupted user experiences and operations. Safeline works against such issues by installing advanced anti-bot protection and defenses against HTTP floods and DDoS attacks.
According to the product Director of SafeLine, the company uses semantic analysis engine technology to detect sophisticated attacks such as SQL injection, XSS, and SSRF. Safeline’s product has several key features, such as dynamic traffic rate limiting, anti-bot challenges, HTML and Javascript encryption, and a waiting room to handle traffic-related issues efficiently. They also have created authentication challenges that add another layer of defense against unauthorized access.
In this blog, you will learn about web application firewalls, how they work, their types, and their features.
What are web application firewalls?
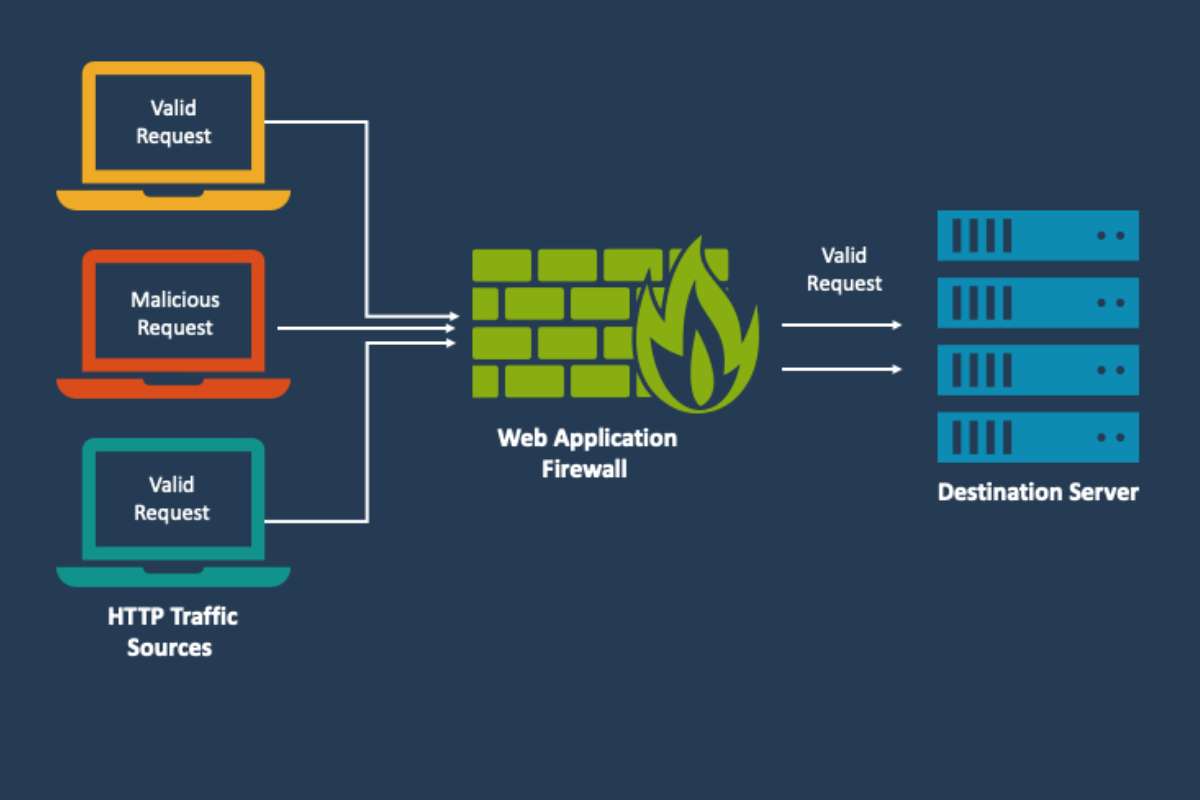
Generally, between the application and the internet, there is HTTP traffic. To monitor and filter the web traffic, there is a web application firewall (WAF). A Web Application Firewall (WAF) is used to protect web applications. It acts as a shield and protects web applications from types of attacks such as SQL injection, cross-site scripting(XSS), file inclusion, and cross-site request forgery (CSRF). These attacks are some of the most damaging threats to web applications.
Here is a small flow diagram that will help you better understand Web Application Firewall.
This image illustrates how a Web Application Firewall (WAF) works. As we can see, there are three traffic sources two are actual users, and one of them represents a malicious entity (it is depicted with a red icon). All the HTTP requests pass through the WAF before they reach the server. The WAF identifies and blocks the harmful traffic, which is indicated by the red “X” symbol. This allows the authentic traffic to proceed to the destination server. The WAF is a barrier that filters and monitors incoming requests. It ensures that only authentic traffic reaches the server so that the risk of cyber threats such as bots and attacks is reduced.
Top 6 Web Application Attacks and How WAF Protects Against Them
1. DDoS Attacks
DDoS (Distributed Denial of Service) attacks on the web application or server with fake traffic. It consumes resources and makes the application inaccessible to authentic users. Some of the DDoS methods are HTTP floods, SYN floods, and DNS amplification. But how does the Web Application Firewall fight against these DDoS methods?
- It identifies and reduces the attacks by monitoring traffic patterns, identifying anomalies, and blocking malicious requests before they reach the server.
- They have implemented several procedures, such as Global Threat Intelligence and Machine Learning, that help to identify threats.
2. SQL injection attacks

It occurs when attackers insert malicious SQL code into input fields like log-in or submission forms to manipulate backend databases. This allows unauthorized data access, deletion, or administrative control. A WAF allows requests of all servers, identifies if any SQL commands are injected, and blocks suspicious queries. It analyzes patterns and attack signatures. It also neutralizes SQL injection attempts that ensure data integrity and application security.
3. Cross-Site Scripting (XSS) Attacks
XSS attacks target users by inserting malicious scripts into web applications. These scripts are executed on the user’s browser, which can lead to identity threats. Other attacks that it might create are session hijacking or data theft. Web application firewalls block XSS payloads before they reach web applications. Using methods like input validation, signatures, and behavioral analysis for unpatched exposures can ensure continuous protection instead of waiting for official fixes.
4. File Inclusion & Remote Code Execution (RCE) Attacks:

Attacks such as LFI/RFI attacks create unauthorized file inclusion, and RCE allows the execution of malicious code remotely. Here comes the role of WAFs they inspect the file paths, sanitize inputs, and use signature-base detection to filter and block unwanted requests.
5. Man-in-the-Middle (MitM) Attacks
MitM attacks occur when attackers disconnect the communication between a user and an application. This attack allows the attackers to steal sensitive data such as credentials or payment information. Methods such as SSL hijacking, DNS spoofing, and ARP spoofing are used. The concept of MitM attacks ensures secure data transmission, identifies communication patterns, and blocks unwanted traffic.
Final Thoughts
A web application firewall is the best security solution for protecting web applications from cyber threats. It helps to monitor and filter unwanted HTTP/HTTP traffic. WAFs recognize attacks such as SQL injection, cross-site scripting (XSS), and DDoS. Several advanced features such as machine learning, fraud communication detection, and signature-based filtering help to identify and block unwanted traffic. Today, the world is fully connected through digital media. Cyber threats are increasing day by day. Thus, enhancing application security and protecting sensitive data ensures business continuity.
Defense is no longer optional, it is a necessity!