We are so surrounded by cyber threats that we need multitudes of network security solutions installed in our laptops. From firewalls and antivirus software to intrusion detection and content filtering, the sheer number of tools required to stay safe is overwhelming. This siloed approach creates complexity and leaves gaps in your defenses. And worst of all, it strains your IT resources. It’s a reactive and fragmented strategy that’s simply no match for today’s sophisticated attackers.
So, how do you protect your data? What if there were a single, all-in-one solution for all your cyber problems? Well, there is one such solution, it is called a Unified Threat Management (UTM) solution. Think of this as a single, consolidated platform that integrates all your essential security functions into one cohesive system. It eliminates the chaos of managing multiple vendors and disparate technologies.
So, what is this threat management, and how does it work? Well, this is exactly what we will answer in this blog.
What is Unified Threat Management? Definition, Features, and Functions
In the simplest terms, UTM is a proactive, all-in-one cybersecurity program. It consolidates various network security functions in a single platform. This approach simplifies network defense and centralizes management. Unified Threat Management provides complete protection against various threats like malware and spam.
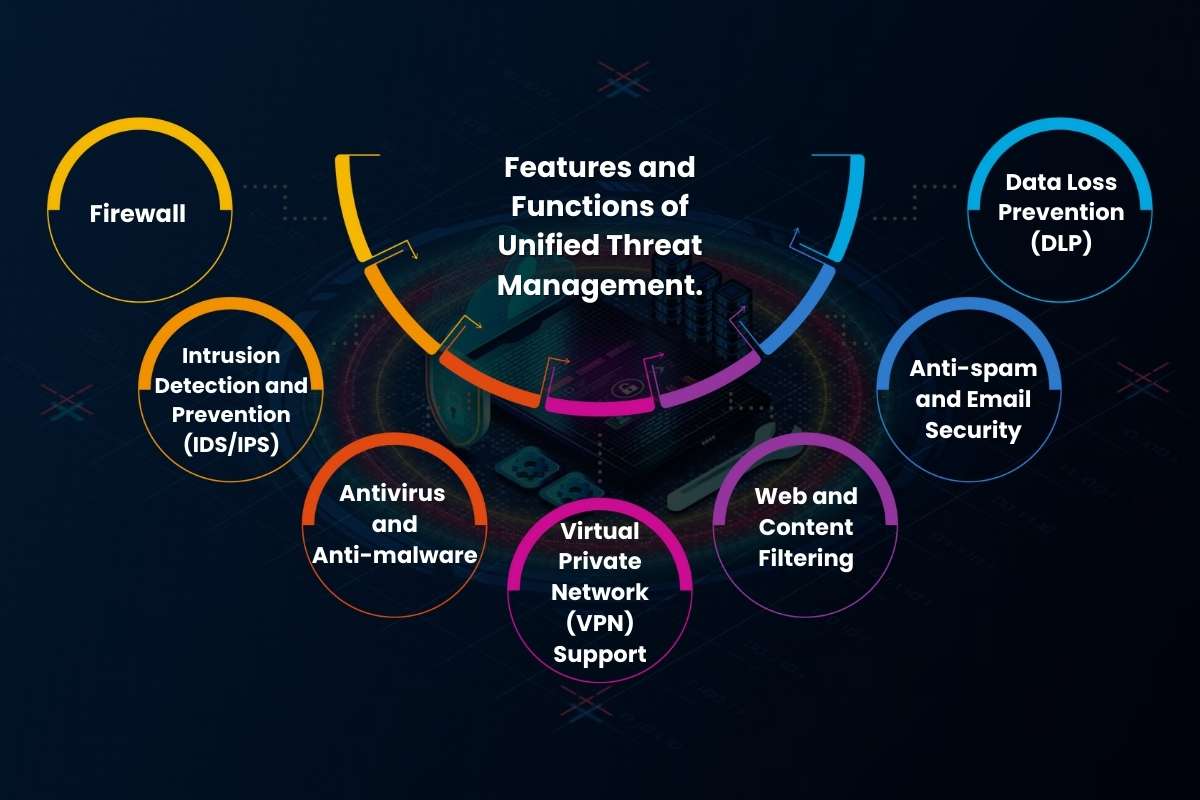
Features and Functions of Unified Threat Management.
As said before, UTM is an all-around cybersecurity program. This means it gives a platform to all network security features.
Let’s take a look at the key features of unified threat management systems.
1. Firewall:
The firewall filters incoming and outgoing network traffic based on a set of rules. It blocks unauthorized access and malicious data. A UTM firewall often includes advanced capabilities like deep packet inspection.
2. Intrusion Detection and Prevention (IDS/IPS):
This feature actively monitors network traffic for suspicious activity and known attack patterns. An IDS will detect and alert on a threat, while an IPS can automatically take action on the alert. IDS and IPS block the malicious traffic before it can cause harm.
3. Antivirus and Anti-malware:
The UTM scans data entering the network for viruses, worms, Trojans, and other forms of malicious software. Unified threat management prevents them from infecting devices. It uses regularly updated signature databases to do so. And, in more advanced systems, it can use heuristic analysis to detect new or unknown threats.
4. Virtual Private Network (VPN) Support:
This allows for secure, encrypted connections for remote users or between different office locations. VPN functionality within a UTM is crucial for a modern, distributed workforce.
5. Web and Content Filtering:
This feature allows administrators to control and restrict access to specific websites, URLs, or types of content. It can be used to improve productivity and enforce corporate policies. This feature can protect users from malicious or inappropriate sites.
6. Anti-spam and Email Security:
A UTM can inspect email traffic to identify and block spam, phishing attempts, and emails containing malicious attachments. This feature, essentially, protects users from a common vector of attack.
7. Data Loss Prevention (DLP):
This function monitors and controls the flow of sensitive data to prevent it from leaving the network. It makes sure no important, confidential data is lost or leaked.
By integrating all these features in a single platform, UTM helps you streamline your cybersecurity solution.
Now that we know the features of UTM solutions, let’s try to understand how they work.
How does the Unified Threat Management Solution work?

Unified Threat Management works by acting as a central security gateway for a network. All incoming and outgoing network traffic flows through the UTM appliance, where it is subjected to a series of simultaneous security checks.
Here’s a step-by-step breakdown of how a UTM works:
Step 1. Traffic Interception:
The Unified Threat Management is deployed at the network perimeter, typically between the local network and the Internet. All data packets, web requests, emails, file transfers, etc., must first pass through the UTM device.
Step 2. Packet-Level Inspection:
The UTM uses a process called Deep Packet Inspection (DPI) to examine the contents of each data packet. This inspection goes beyond the content’s header. This allows the appliance to look inside the traffic to identify malicious code, viruses, or policy violations that a traditional firewall might miss.
Step 3. Multi-Module Analysis:
As the traffic is being inspected, it is simultaneously analyzed by several different security modules, including firewall, IPS, web/content filtering, antivirus, anti-spam, etc.
Step 4. Centralized Policy Enforcement:
All of these security checks are managed from a single, unified console. This makes sure that security policies are applied consistently across all functions. This eliminates the risk of security gaps that can occur when managing multiple, disconnected products.
Step 5. Logging and Reporting:
The Unified Threat Management generates logs and reports for all network activity and security events. This centralized reporting gives administrators a single, comprehensive view of their network’s security posture. This enables them to quickly identify threats, analyze attack patterns, and respond more efficiently.
What are the real-world applications of UTM?

While all of this is interesting, you might be wondering what the real-life use of Unified Threat Management solutions is. And that’s exactly what we will answer in this section.
Unified Threat Management (UTM) solutions have become the backbone of cybersecurity for organizations of all sizes. For a medium-sized retail chain, UTMs protect point-of-sale systems from breaches, secure remote employee access with VPN, and give managers the convenience of monitoring every store from one dashboard.
On a university campus, UTMs do double duty, keeping sensitive student data safe while filtering out harmful content, yet still allowing researchers the freedom to access what they need.
Hospitals and clinics lean on the same technology to guard patient records and medical devices. It helps them in meeting HIPAA requirements while fending off ransomware and other cyberthreats that could put lives at risk.
Even businesses spread across multiple locations benefit. A financial services firm, for instance, can lock down its branch networks while ensuring encrypted connections to its central data center.
And in manufacturing, Unified Threat Managements safeguard industrial control systems, segmenting networks to keep malware at bay and ensuring that production lines never skip a beat.
Across industries, the story is the same: UTMs bring enterprise-grade security into reach, combining multiple defenses into one streamlined system that adapts to the unique risks of each environment.
Top UTM Solutions for Complete Protection

1. Check Point UTM
Check Point is popular for its deep-rooted expertise in firewall technology. This UTM is often seen as the market leader in that space. Their solutions offer comprehensive threat prevention and intelligence with a focus on a “3D security” approach. They provide a highly granular and flexible policy management system. This allows for detailed control and reporting across the network.
2. Fortinet FortiGate
Fortinet distinguishes itself with custom-built security processors (ASICs) that accelerate the performance of its Unified Threat Management features. This UTM solution allows for high throughput even with deep packet inspection enabled. FortiGate is also a leader in the secure SD-WAN space. It combines next-generation firewall capabilities with software-defined networking for simplified branch office connectivity.
3. Sophos SG UTM
Sophos is well-regarded for its user-friendly interface and simplicity. It is particularly appealing for small to medium-sized businesses (SMBs) and organizations with limited IT staff. The Sophos Unified Threat Management integrates tightly with its endpoint protection. They create a unique “Synchronized Security” system where the firewall and endpoints can share threat data and automatically respond to incidents.
4. Cisco UTM
Cisco’s strength lies in its extensive network infrastructure and global threat intelligence. Their UTM offerings leverage the vast resources of Cisco Talos, one of the world’s largest commercial threat intelligence teams. The Cisco UTM model often emphasizes its integration with other Cisco security products. You have access to programs like Cisco Umbrella for DNS-layer security and Cisco Secure Endpoint for endpoint protection.
5. SonicWall UTM
SonicWall is a pioneer in the Unified Threat Management space. It is known for its patented Deep Packet Inspection (DPI) technology that examines the full data payload to find threats hidden within legitimate traffic.
Pros and Cons of UTM Solutions
| Pros of UTM | Cons of UTM |
|---|---|
| All-in-One Security: Centralized tools, easy management. | Slower Performance: Heavy load can reduce speed. |
| Lower Costs: Saves on hardware and licensing. | Single Failure Risk: One device down = all security down. |
| Faster Response: Quick detection and action. | Less Flexible: Limited fine-tuning options. |
| Better Visibility: Data correlation enhances protection against diverse attacks. | Vendor Lock-in: Proprietary systems can make switching or integration harder. |
| Simpler Compliance: Easier audits and reporting. | Scaling Issues: May struggle in large enterprises. |
Unified Threat Management Market Reports: What does the Future hold?
The UTM market is experiencing significant growth globally. According to Data Insights Market, the UTM solutions market is estimated to reach approximately $18.5 billion by 2025. The research shows a CAGR of 12.5%, driven by rising cyber threats, SME adoption, cloud-based UTM, and AI/machine learning integration.
The future of Unified Threat Management lies in smarter, cloud-based, and integrated security platforms. Cyber threats are growing more advanced, and the old “all-in-one box” model is giving way to scalable, flexible designs like hybrid and cloud-native solutions. UTMs still simplify security, but now they can adapt to businesses of all sizes.
This shift is driven by the complexity of modern networks. Remote work, cloud adoption, and the explosion of IoT devices have expanded the attack surface beyond what a single on-premise appliance can handle. Security must now follow data and users, whether on servers, SaaS apps, or public clouds.
To meet these demands, vendors are adding advanced tools. AI and machine learning help detect unknown threats in real time. UTMs are also moving toward synchronized security and Extended Detection and Response (XDR), working together with endpoints, email, and other systems to share intelligence and automate defenses.
Is Unified Threat Management and Next-Generation Firewall the same?
No, UTM and NGFW are not the same. NGFW is a more advanced evolution of firewalls that includes UTM’s bundled security functions. But alongside that, it also adds application and user identification and control. NGFW offers a deeper visibility and control than traditional UTM devices.
While UTMs provide a one-stop shop for basic network security, NGFWs are designed for higher performance. They offer more granular, customizable security policies, making them suitable for more complex network environments.
Conclusion:
Unified Threat Management moves beyond the fragmented, reactive approach of managing multiple security tools. Instead, it offers a single, consolidated platform. This unified strategy simplifies your security infrastructure, lowers costs, and eliminates the gaps that attackers often exploit.
By integrating a powerful firewall, intrusion prevention, antivirus, and more into one system, UTM provides a robust, proactive defense. It gives you a single pane of glass to monitor and manage your entire network’s security. This cohesive approach not only protects your business but also frees up valuable IT resources, allowing you to focus on growth without sacrificing your security posture.
FAQs
What is the difference between UTM and a firewall?
Think of a traditional firewall as a security gatekeeper. It basically filters network traffic based on basic rules like IP addresses and ports. A UTM, or Unified Threat Management, is a comprehensive security solution that bundles a firewall with many other features. It includes network security features, such as antivirus, web filtering, and intrusion prevention. Therefore, a UTM is essentially an all-in-one security appliance, while a firewall is just one of its core components.
What is a UTM full scan?
There is no standardized industry term for a “UTM full scan.” A UTM operates continuously in real-time to inspect network traffic as it passes through the device. Unlike a personal computer’s antivirus, which can perform a scheduled full disk scan, a UTM’s primary function is to prevent threats from entering the network in the first place, rather than scanning for existing ones.
Can a proxy server replace a UTM system?
No, a proxy server cannot replace a UTM system. A proxy server’s primary function is to act as an intermediary for web requests. It is primarily used to control or cache internet access. A UTM system, by contrast, is a comprehensive security appliance that bundles multiple security functions.