If you log into your computer and suddenly it crashes, for no known reason. The computer screen freezes or odd pop-ups appear on your screen, you might feel confused about what is happening. The chances are that you are attacked by a Trojan virus, also known as a Trojan horse virus. The virus got its name from the infamous Trojan horse used by the Greeks to fool and attack the Trojans in Homer’s Odyssey.
And that’s pretty much what the virus does. It disguises itself, enters your computer, and attacks it. It can cause real harm to your data if not taken care of. So, how do you recognize a Trojan virus, and most importantly, how do you get rid of it?
In this blog, we shall go through everything we need to know about this dangerous virus and try to prevent it from destroying your data.
What is the Trojan Virus and How Does it Work?
The Trojan horse virus is a malware that fools you into downloading it onto your devices by disguising itself as a real, operational program. The best way to understand how this virus works is by understanding the story of the Trojan horse.
During the Trojan War, the Greeks gifted Troy a wooden horse as a peace offering. But inside the horse, hid Greek soldiers, ready to attack the city once inside. And this is exactly what this virus does.
It pretends to be a program in your device, enters, and starts attacking your data.
There are 12 types of Trojan Viruses:
| Type of Trojan | Main Purpose |
|---|---|
| Backdoor Trojans | Create hidden entry points for remote control, botnets, or traffic monitoring. |
| Exploit Trojans | Exploit software vulnerabilities to run malicious code silently. |
| Rootkit Trojans | Hide themselves and other malware to evade detection and maintain control. |
| Dropper/Downloader Trojans | Deliver other malware by carrying it or downloading it online. |
| Banking Trojans | Steal banking credentials and financial data. |
| DDoS Trojans | Use infected devices to launch distributed denial-of-service attacks. |
| Fake Antivirus Trojans | Mimic antivirus tools to trick users into paying for fake virus removal. |
| Remote Access Trojans (RATs) | Give attackers full remote control over the device. |
| Infostealer Trojans | Steal sensitive data such as passwords and personal details. |
| SMS Trojans | Send premium SMS messages from infected mobiles, charging the victim. |
| Mail-finder Trojans | Collect email addresses for spamming campaigns. |
| Trojan-GameThief | Steal credentials from online games. |
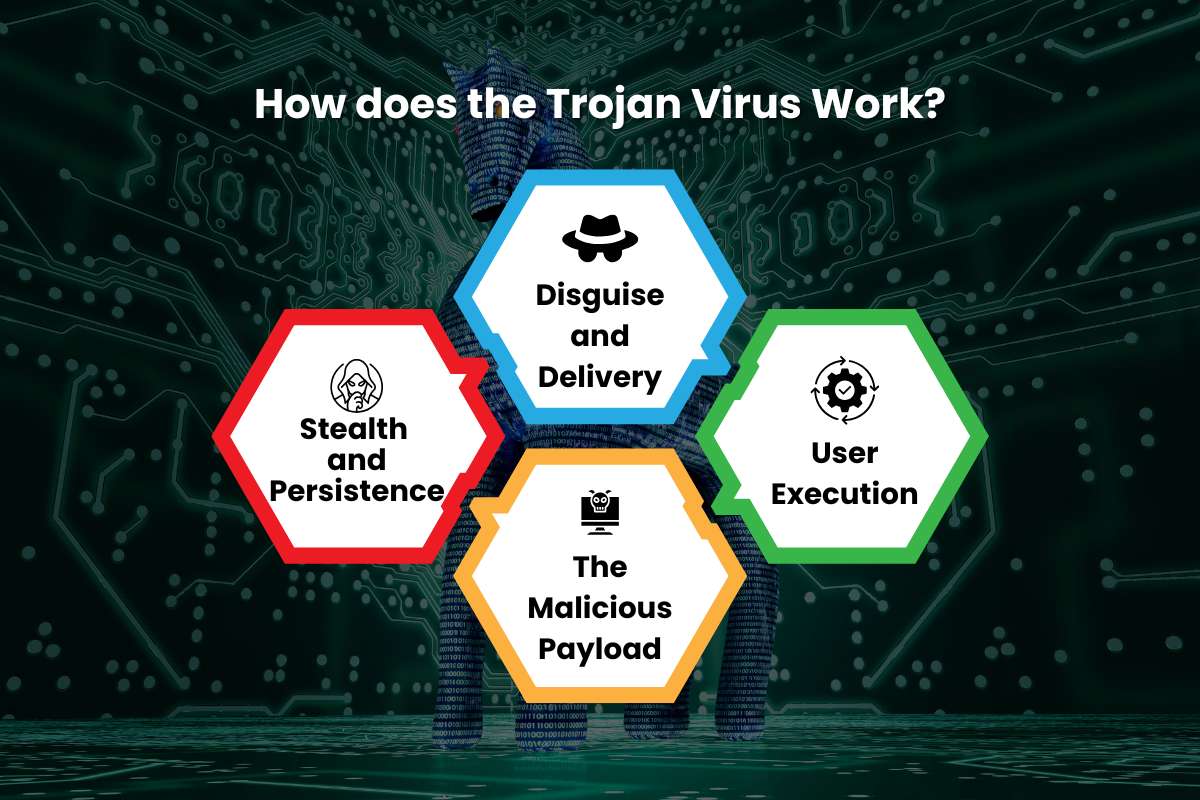
How does the Trojan Virus Work?
Unlike a virus or a worm, a Trojan doesn’t replicate itself. Its effectiveness relies on social engineering rather than technology. Basically, it depends on manipulating human psychology to bypass security measures.
Here’s a breakdown of how a Trojan operates:
1. Disguise and Delivery:
The first step is to camouflage the malicious code within a seemingly legitimate file. This could be a free software download, a game, a movie file, a browser extension, or a seemingly harmless email attachment. The attacker uses various methods to deliver this file. Trojan can come as phishing emails, pop-up ads, or compromised websites. The user, believing the file is harmless, downloads and runs it.
2. User Execution:
The crucial step is the user’s action. A Trojan virus requires the user to click on the infected file, install the program, or open the attachment. Once executed, the Trojan’s malicious code is deployed onto the system.
3. The Malicious Payload:
After it’s inside, the Trojan Virus can perform a variety of harmful actions, depending on its specific purpose. This is called the “payload.”
4. Stealth and Persistence:
Once the payload is delivered, a Trojan Virus often works to remain hidden. It might run in the background, modify system files, or disable security software to avoid detection. This ensures it launches automatically every time the computer is turned on. The user may not notice any immediate signs of infection, making Trojan viruses particularly dangerous.
Now you might be wondering what these payloads are. Well, here’s a brief of payloads performed by Trojans.
1. Creating a Backdoor:
Many Trojans install a “backdoor” on the system. This gives the attacker remote, unauthorized access to the computer. It allows them to control the device, steal data, or install more malware.
2. Stealing Data:
Some Trojans are designed to steal sensitive information. They can access your banking credentials, passwords, credit card numbers, and other personal data.
3. Joining a Botnet:
A Trojan can turn the infected computer into a “zombie” that is part of a “botnet.” A botnet is a network of compromised computers controlled by a single attacker. These botnets are often used for large-scale attacks, such as Distributed Denial of Service (DDoS) attacks.
4. Spyware:
They can monitor user activity, including keystrokes (a keylogger), screenshots, and browsing habits.
Four Trojan Attacks That Everyone must be Aware of
There have been numerous Trojan Virus attacks since the conception of the internet. It is extremely important to be aware of these attacks and what they do. It is necessary to know about the four attacks for your digital safety.
Here are four Trojan Virus attacks that everyone must be aware of:
1. Emotet:
Initially a banking Trojan, it evolved into a powerful botnet that delivered other malware, including ransomware.
2. Zeus (Zbot):
A highly successful banking Trojan designed to steal financial credentials by logging keystrokes and intercepting data.
3. Trickbot:
Another banking Trojan that was also used to deliver ransomware, particularly targeting large organizations.
4. FluBot:
A recent and prominent SMS Trojan that targeted Android phones by tricking users into downloading malicious apps via text messages.
How to Detect a Trojan Virus in Your Device?

Detecting a Trojan horse virus can be challenging because they are designed to be stealthy and deceive users. However, there are several signs and methods you can use to determine if your system has been compromised.
1. Behavioral Red Flags (Signs of Infection)
A Trojan infection often manifests through unusual system behavior. Pay close attention to these common symptoms, such as sudden performance issues, unwanted pop-up ads, disrupted internet connection, and unauthorized activities.
Also, check for disabled security software; they are one of the major signs of a Trojan virus attack.
2. Technical Detection Methods
For a more definitive diagnosis, you’ll need to use specific tools and techniques. The most effective way to detect a Trojan Virus is by using reputable and updated antivirus software. These programs are specifically designed to scan for known threats and a wide range of suspicious behaviors.
It’s often recommended to use a different tool than the one you already have. It is very possible the Trojan Virus may have compromised it. But remember, no antivirus solution offers a 100% guarantee. If you suspect your device is compromised, seek professional cybersecurity assistance promptly.
Another option is to open your system’s Task Manager (Ctrl+Alt+Delete on Windows) or Activity Monitor (on macOS). Check for any unfamiliar or suspicious processes running in the background. Look for a process with a strange name or one that is consuming a disproportionate amount of CPU or memory. It could be a sign of a Trojan.
Many Trojan viruses are designed to launch automatically when you start your computer to maintain a persistent presence. Check your system’s startup programs and disable any that you don’t recognize.
Professional cybersecurity practices recommended by established standards, such as the NIST Cybersecurity Framework (CSF), guide effective detection, monitoring, and response to Trojan Virus infections.
The NIST CSF emphasizes continuous monitoring to identify anomalies and indicators of compromise promptly, enabling early detection of threats like Trojans. This includes identifying and protecting critical assets, detecting cybersecurity events quickly, and responding effectively.
By lining up detection and response efforts with frameworks like NIST CSF, organizations and individuals can enhance their ability to spot Trojans early and mitigate their impact more effectively.
How to Prevent Trojan Virus Attack? Precautions to Save Your Data
There are ways to prevent a Trojan Virus attack on your device. If you follow the tips given below, you will be safe from the hazardous virus.
1. Use a strong antivirus:
Keep your security software updated and run regular scans.
2. Be cautious online:
Avoid downloading files from untrusted sources or opening suspicious email attachments.
3. Update your software:
Regularly update your operating system and applications to patch security vulnerabilities.
4. Use a firewall:
A firewall helps block unauthorized connections to your computer.
5. Practice smart habits:
Don’t click on suspicious pop-ups or links, and use strong, unique passwords.
6. Practice safe browsing:
Use multi-factor authentication whenever possible to add extra layers of protection.
A Step-By-Step Guide to Removing Trojan Horse Virus:

Now even with all these precautions, what if, after all this, your computer still gets attacked by a Trojan horse virus? What can you do? How can you remove it?
Here’s a step-by-step guide to removing a Trojan virus from your computer:
Step 1: Disconnect from the Internet
The very first action you should take is to disconnect your computer from the internet. Unplug your Ethernet cable or turn off your Wi-Fi. This prevents the Trojan from communicating with its command-and-control server, stopping it from stealing data or downloading more malware.
Step 2: Boot into Safe Mode
Safe Mode is a diagnostic startup mode that loads only the essential programs and drivers your computer needs to run. This prevents most malware, including Trojans, from launching automatically, making it easier to remove them.
For Windows:
Restart your PC. As it restarts, hold down the Shift key and select Troubleshoot > Advanced options > Startup Settings > Restart.
After the PC restarts, you’ll see a list of options. Choose Safe Mode with Networking to allow your security tools to update.
For Mac:
Restart your Mac and immediately press and hold the Shift key until the login window appears.
Step 3: Run a Full System Scan
Once in Safe Mode, you need to use a powerful anti-malware tool to find and remove the Trojan. It’s often best to use a different scanner than the one you normally use, as the Trojan may have compromised it.
Download a reputable tool:
Download a well-known anti-malware program like Malwarebytes, Norton Power Eraser, or the Kaspersky Virus Removal Tool.
Update the definitions:
Before scanning, ensure the tool’s virus definitions are fully updated. This is why you booted into Safe Mode with Networking.
Run a full scan:
Perform a comprehensive, full-system scan. This will take time, but it is necessary to find all hidden files associated with the Trojan.
Quarantine/Remove all threats:
The scanner will list any detected threats. Follow the prompts to quarantine and then remove them.
Step 4: Manually Check for Leftover Files (Optional but Recommended)
After the scan, there might be some lingering files or settings.
Check Startup Programs:
Open your system’s Task Manager or System Configuration and disable any suspicious programs from launching on startup.
Uninstall Suspicious Programs:
Go to your computer’s Add or Remove Programs list and uninstall any programs that you don’t recognize, especially those that were installed around the time you suspect the infection occurred.
Delete Temporary Files:
Trojans often leave malicious files in temporary folders. Clear your temporary files to ensure all traces are gone. On Windows, you can do this by running %temp% in the Run dialog.
Step 5: Change All Your Passwords
Assume that your passwords have been compromised. Once you are certain the Trojan is gone, change the passwords for all your important accounts, including:
- Banking and financial services
- Social media
- Cloud storage
Use a password manager to create strong, unique passwords for each account.
Step 6: Update Your System and Software
Finally, ensure all your operating system updates and software patches are installed. This closes any vulnerabilities that the Trojan may have exploited to get onto your computer in the first place.
The Danger of Trojan Virus- Real World Incidents of the Threat

According to a report by Kaspersky, banking Trojans increased from 420,000 in 2023 to 1,242,000 in 2024. To put into perspective, the attacks surged by 196% in 2024 compared to 2023.
Another Q2 report by Kaspersky showed a surge of 33% in Trojan virus detection between 2023 and 2024. Globally, there are around 190,000 new malware attacks every second in 2025, with nearly 90% being phishing or social engineering-related, but Trojans remain a significant part of malware threats.
Positive Technologies’ Cyberthreat Report Q4 2024 showed that Trojan accounts for 38% of cyberattacks. This makes the threat of this hidden virus more dangerous.
Difference between Trojan Viruses and other Malwares: What makes Trojan different?
| Malware Type | Description | How It Spreads/Functions | Key Difference from Trojan |
|---|---|---|---|
| Trojan | Disguises itself as a legitimate program to trick users. | Requires user action to install/run; does not self-replicate. | Trojan relies on deception; acts as a delivery mechanism for other malware. |
| Virus | Attaches to legitimate files or programs. | Spreads by infecting other files; requires user action to execute. | Viruses replicate by infecting files; Trojans do not self-replicate. |
| Worm | Standalone malicious program. | Self-replicates and spreads across networks without user action. | Worms spread autonomously; Trojans need user execution. |
| Ransomware | Encrypts files or locks systems and demands ransom. | Often delivered via Trojans or other methods. | Trojan virus is the method of delivery; ransomware is the payload. |
| Spyware | Monitors user activity and collects sensitive data. | Can be installed via Trojans or other malware. | Spyware is a specific function; Trojan is the entry method. |
Conclusion:
The threat of a Trojan virus is a reminder that appearances can be deceiving. As we’ve seen, this insidious form of malware exploits our trust and curiosity. It disguises itself as a harmless application to breach our defenses. Once inside, it can steal your personal data or turn your devices into a part of a larger, malicious network. The most dangerous aspect of a Trojan is its stealthy nature. It can operate undetected in the background of your device. This makes it difficult to spot until the damage has already been done.
Protecting yourself requires a combination of vigilance and the right tools. By recognizing the behavioral red flags and using reliable security software, you can reduce your risk a lot. Understanding the differences between a Trojan and other malware also helps you to better identify the threat and respond. Ultimately, staying safe online means adopting a healthy skepticism for your own safety. And last of all, remember that the most dangerous threats arrive in the most unsuspecting way.
FAQs
Can a Trojan virus infect my phone or Mac?
Yes, Trojans are not limited to Windows computers. They can infect macOS, Android, and iOS devices, as well. They often disguise themselves as fake apps, software updates, or links sent via SMS or email. Mobile Trojans can steal data, send premium SMS messages, or create backdoors for attackers.
What is the difference between a Trojan and a backdoor?
A Trojan is malware disguised as a legitimate program that gets installed when the user executes it. A backdoor is the hidden entry point that a Trojan often installs afterward, allowing attackers remote and unauthorized access to the device.
Can a Trojan virus still be active if I disconnect from the internet?
Yes, a Trojan can still run on your device offline, performing tasks like data theft or system changes. However, it may not be able to communicate with its controller or send stolen data without internet access.
Are Trojans always harmful?
Yes, Trojans are malicious by design. They can steal personal data, install ransomware, turn your device into part of a botnet, or allow attackers to spy on your activities. Their stealthy nature makes them particularly dangerous.
Can Trojans infect networked devices or IoT gadgets?
Yes, Trojans can target devices connected to networks, including Internet of Things (IoT) gadgets, by exploiting security vulnerabilities or weak passwords, allowing attackers to control these devices remotely.






