Communication is the lifeblood of business; it is foundational for any company to stay afloat. But a silent but devastating threat looms over communication: Email Bombing. It can turn your company’s inbox—the central nervous system for operations into a torrential storm. Think of it getting flooded with a deluge of unwanted messages. This is not mere spam; it’s a malicious digital assault on your communication system. It is designed to paralyze your communication channels and hide critical security breaches.
The resulting chaos can be the equivalent of a digital cardiac arrest for an enterprise. Mail bombing can lead to system downtime and operational bottlenecks. It can be a dangerous obfuscation of legitimate security alerts. For any organization relying on communication, the operation and reputation are at risk.
In this blog, we will try to grasp the consequences of Email Bombing that no modern business can afford to face unprepared.
What is Email Bombing? How Does it Differ from Spam? Definition and Types
The Center for Internet Security (MS-ISAC) defines an email bombing as “An email bomb is an attack against an email server designed to inhibit the server’s normal function or render it unresponsive, preventing email communications, degrading network performance, or causing network downtime.”
According to the U.S. Department of Health and Human Services’ Cybersecurity Coordination Center (HHS), an email bomb is “a type of Denial of Service (DoS) attack that allows attackers to bury legitimate transaction and security messages in an unsuspecting inbox by rendering the victim’s mailbox useless.”
The 6 Types of Email Bombing Attacks Your Team Must Understand to Stay Safe

There are six types of Email Bombing Attacks that you must know about. Each attack has a different effect. Here’s how they work and attack you:
| Attack Type | What it does (short) | Primary impact | Quick mitigations |
|---|---|---|---|
| Mass Mailing Attack | Sends a huge volume of duplicate/random emails to one address (often via botnets). | Fills mailbox/server; denial of service. | Spam filters, rate limits, bot detection, blocklists. |
| List Linking / Subscription Bombing | Signs the victim up for many lists, so confirmations/newsletters flood the inbox. | Buries important mail; hard to trace. | CAPTCHA on sign-ups, unsubscribe verification, email throttling, and disposable-address checks |
| Zip Bombing | Sends maliciously crafted compressed files that explode when scanned/unpacked. | Exhausts CPU/memory of mail scanners; service disruption. | Limit archive recursion/size, sandboxing, and scanner timeouts, and block suspicious archives. |
| Attachment Bombing | Sends very large or many attachments to fill storage or overload processing. | Mailbox quota exhaustion; processing delays. | Attachment size limits, quotas, content scanning, and blocking high-volume senders. |
| Email Loops | Triggers misconfigured auto-responders to generate endless replies. | Continuous message loops; inbox/server flooding. | Disable/limit auto-replies, loop-detection headers, and relay checks. |
| Reply-All Bombing | Mass use of “Reply All” on distribution lists to create an avalanche of messages. | Floods distribution lists and inboxes; productivity loss. | Rate limits on list replies, moderator controls, educate users, and list posting rules. |
Causes of Email Bombing? Technical Flaws, Poor Hygiene, and the Malicious Motives
The causes of email bombs are multifaceted. These attacks happen due to various reasons. The reasons include technical vulnerabilities, attacker motivations, and poor cyber hygiene practices.
Here’s a list of all causes of Email Bombing that you must be aware of:
1. Exploiting System Weaknesses:
Attackers take advantage of existing vulnerabilities. A lack of rate limits, poor spam filtering, and misconfigured email servers make it easy for them to flood inboxes.
2. Weak Security:
Bad practices like using weak passwords, not having multi-factor authentication (MFA), and poor account management let attackers hijack email accounts. They then use these compromised accounts for their email bombing campaigns.
3. Missing Security Protocols:
Attackers can easily spoof trusted email addresses to flood inboxes. These attacks happen when sender verification protocols like DKIM and DMARC are not implemented.
4. Insecure User Habits:
Employees without proper cybersecurity training can unknowingly enable email bombing. By clicking on malicious links or opening suspicious attachments, they help the attackers succeed.
5. Using Bots and Automation:

Attackers use scripts, spambots, and botnets to send emails. This allows them to launch and sustain large-scale email floods.
6. Poor Infrastructure Defense:
When organizations lack proper filtering, rate limiting, and anomaly detection, attackers face very little resistance. They specifically target organizations or individuals with these weak defenses.
7. Intended Malicious Motives:
1. Disruption of Operations:
To incapacitate communication channels, causing delays, stress, and operational breakdowns.
2. Obfuscation and Smoke Screening:
Masking more sophisticated or damaging cyber activities. Mail bombing can be used to hide fraud, data theft, or lateral movement within networks.
3. Harassment and Retaliation:
Personal conflicts and cyberbullying attacks by competitors to damage reputation.
4. Financial Gains:
In some cases, attackers use email flooding as a distraction. While you are stuck with email bombs, they may be executing a Business Email Compromise (BEC).
In summary, poor cyber hygiene and a lack of proper email protocols increase vulnerability to email bombing. Lack of cyber hygiene makes it an easier attack vector for malicious actors.
Here’s a table of prioritized causes for mail bombing:
| Priority | Cause | Risk Level |
|---|---|---|
| 1 | Weak authentication & security | Very High |
| 2 | Exploitation of system vulnerabilities | Very High |
| 3 | Automation and botnet misuse | High |
| 4 | Lack of proper email security protocols | High |
| 5 | Insufficient infrastructure defenses | Very High |
| 6 | Unsecured or inadequate user practices | Medium |
| 7 | Intended malicious motives | High |
Catastrophic Impacts of Email Bombing Your Company Can’t Afford to Ignore
Email Bombing can have severe effects and impacts on both individuals and organizations. It can disrupt communication and cause wider operational and security consequences.
Here’s the 3 impact areas of email bomb attacks:
1> Immediate Effects
1. Inbox Overload:
Victims’ email inboxes get flooded with massive volumes of emails. This makes it difficult or impossible to access legitimate messages.
2. Denial of Service (DoS):
The influx of emails can overwhelm mail servers and communication infrastructure. This can cause service outages or degradation, impacting productivity.
3. Loss of Important Communications:
Important emails, alerts, or notifications are buried under the flood. This will lead to missed deadlines, security warnings, or critical business communications.
2> Operational and Business Impacts
1. Disruption of Business Operations
Communication breakdowns delay workflows and decision-making, affecting multiple departments and clients.
2. Increased IT and Support Costs
Responding to an email bomb and cleaning up after it is costly. It requires significant resources for technical allocation, investigation, and recovery efforts.
3. Risk of Secondary Attacks
Email bombing often happens right before or alongside other attacks. Attacks like phishing, malware distribution, or social engineering accompany mail bombing.
4. Reputational Damage
Organizations that fail to secure their communications risk losing stakeholder trust. They may also suffer brand damage due to prolonged disruptions or security breaches.
3> Security and Compliance Risks
1. Exposure to Fraud and Unauthorized Access
Real security alerts get lost in the noise. As a result, attackers can exploit these gaps to execute fraud or data breaches unnoticed.
2. Potential Regulatory Non-compliance
Email outages or security incidents can breach data protection laws and regulatory rules. This may result in heavy fines or other sanctions.
Now you know the causes and effects of mail bombing. Let’s talk about how you can detect these attacks. Shall we?
Essential warning signs: Detect an Email Bombing attack instantly

You need to stay on high alert to detect Email Bombings. To detect, look out for the following signs:
- Unusual Spike in Email Traffic: A sudden, massive increase in inbound emails from multiple sources or a single sender over a short period.
- Repetitive or Duplicate Emails: Receiving numerous identical or similar emails exhibiting the same subject, content, or attachments.
- High Volume of Subscription Confirmations: Many opt-in or confirmation emails from various mailing lists.
- Inbox Performance and Server Load Impact: Noticing degraded email server performance, delayed deliveries, or mail queue buildup.
- Auto-Responder or Bounce Back Loops: Repeated auto-replies or bounce-back messages are increasing dramatically.
- Spike in Spam or Unknown Senders: An unusual rise in spam or emails from suspicious or unknown domains can be a red flag.
- Security Alerting Systems: Use email security gateways with anomaly detection and behavioral analytics. You can also use AI-powered tools that can detect irregular inbound email patterns.
- User Reports: Increased user complaints about inbox flooding or missing important emails.
While detecting is a post-attack solution, there are ways to prevent email bombing beforehand. Let’s talk about it.
Critical steps to stop Email Bombs before they cripple your business
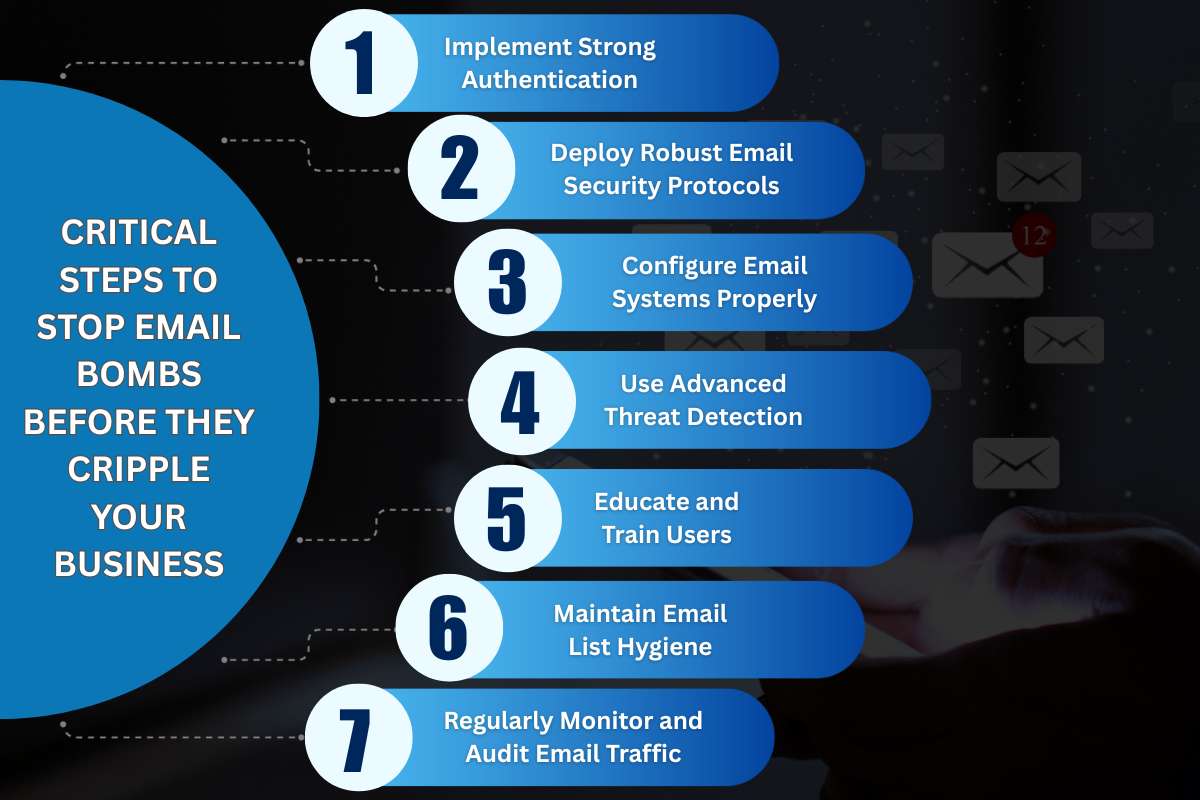
Maintaining strong cyber hygiene is critical for email systems. They make sure there is uninterrupted communication.
Here are seven ways to prevent email bomb attacks:
1. Implement Strong Authentication:
Use complex passwords combined with multi-factor authentication (MFA). This helps to prevent unauthorized access and account hijacking.
2. Deploy Robust Email Security Protocols:
Enforce sender verification through SPF, DKIM, and DMARC. This reduces spoofing and phishing-based email floods.
3. Configure Email Systems Properly:
Keep mail servers and spam filters updated. Apply rate limiting to emails, configure automatic replies to avoid loops, and restrict attachment sizes.
4. Use Advanced Threat Detection:
Employ anomaly detection, botnet pattern recognition, and behavioral analytics. Use them to spot flooding attempts early and mitigate damage.
5. Educate and Train Users:
Conduct regular cybersecurity awareness training for employees. Teach them to recognize phishing, suspicious emails, and avoid actions that enable email bomb attacks.
6. Maintain Email List Hygiene:
Use double opt-in for subscriptions and regularly cleanse mailing lists. Restrict who can send to distribution groups to minimize risks of subscription bombing.
7. Regularly Monitor and Audit Email Traffic:
Analyze email logs to identify irregular surges or suspicious activity promptly for rapid response.
Real-life incidents of Email Bombing: What do the two major attacks tell us about Email security gaps?
In February 2025, Darktrace detected a single user who was hit with over 150 emails from 107 unique domains. And all that within under five minutes. The attacker used the victim’s email to trigger numerous registration confirmation emails. This “subscription bombing” created a swarm effect that overwhelmed the inbox. This ended up revealing the challenges of detecting such attacks with conventional tools.
In another study, 24 mail bombing waves targeted 17 individuals across six organizations with close to 47,000 emails delivered. Attacks lasted about 1-2 hours each. Some of the attacks delivered thousands of emails rapidly to individual targets. These emails were mainly directed to non-technical employees.
Conclusion:
Email bombing is a significant cyber threat that demands proactive attention. It’s more than a nuisance; it’s a calculated attack. It is used to cause disruption, mask serious security breaches, and paralyze communication.
By understanding and implementing strong defenses, companies can reduce the risk. Ignoring this threat leaves the door open to catastrophic operational and reputational damage. Prioritizing robust email security is no longer optional; it is essential against the impact of email bombing.
FAQs
1. How long does an email bomb last?
Email bomb attacks are typically short and aggressive. They often last around one to two hours. However, the residual flood of unwanted emails can persist for days or longer.
2. What is Email Flooding?
Email flooding (or mail bombing) is a type of Denial of Service (DoS) attack. It happens when an attacker attacks an email server by sending a massive, rapid volume of emails.
3. What is the difference between spam mail and mail bombing?
The key difference lies in intent and volume. Spam is unwanted, unsolicited bulk commercial email. Mail bombing is a high-volume, malicious denial-of-service attack. Email bombing is designed to crash or overwhelm an inbox/server.
Also Read :- What You Don’t Know about Email Security Protocols Could Cost You Millions?






