As we move through 2026, protecting data is the ultimate priority for leaders who want to keep their organizations steady. Modern data security management (DSM) is the heartbeat of a healthy company. It ensures that the foundation of your business is solid, even when the unexpected happens.
Having a dedicated DSM system makes a big difference. Think of it as wearing a seatbelt and building a smarter, safer car that can predict a collision before it occurs.
Integrating DSM into your overall strategy means you can stop reacting to crises and start growing with confidence. By putting people and their privacy at the center of your plan, you turn a complex technical challenge into a human advantage that defines your success.
Why the Shift is Happening Now?
In 2026, the digital world is an interconnected web of simple data storage and complex ecosystems where “identity” is the new perimeter, making data security management essential.
- From “Break-In” to “Log-In”: Attackers now frequently use legitimate credentials rather than technical exploits, making data access control a primary risk factor.
- The Cost of Silence: Approximately $4.45 million USD per breach in the 2025 IBM report. Boards must actively address this financial risk without ignoring or delegating it.
- Regulatory Maturity: Compliance has moved beyond “checking boxes” to requiring explicit proof of risk-based reasoning and data lineage.
So, how do we protect ourselves and our companies? A simple answer is data security management. And this leads to the question, what is DSM, and how does it work? Let’s answer that.
What is Data Security Management and Why Every Organization Needs It

DSM keeps your organization’s information safe, accurate, and available. Instead of a single lock, we use a 360-degree plan to guide your team in managing data from creation to deletion.
At its core, it focuses on three simple goals:
- Privacy: Making sure only the right people can see sensitive information.
- Accuracy: Ensuring the information remains correct and has not been tampered with.
- Access: Ensure your team can actually reach the data they need to do their jobs.
How does it work?
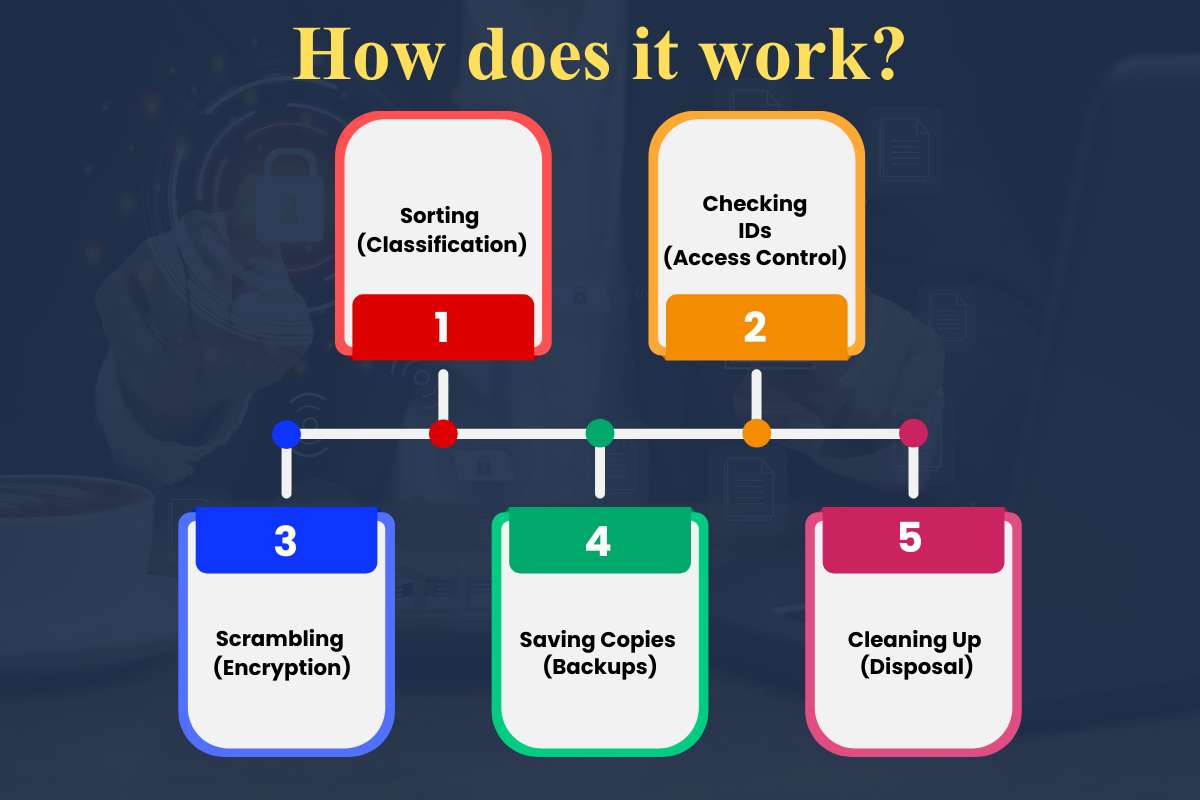
Data security management is a 5-step process. Here’s how it works:
- Sorting (Classification): Labeling data as “Public,” “Internal,” or “Top Secret” so you know what needs the most protection.
- Checking IDs (Access Control): Ensure everyone proves their identity (with a password and a phone code) before they enter digital folders.
- Scrambling (Encryption): Turning your data into a secret code that only someone with a “key” can read, even if it gets stolen.
- Saving Copies (Backups): Keeping extra copies of your work in a safe place so you don’t lose everything if a computer breaks.
- Cleaning Up (Disposal): Completely erasing old information from the digital “trash can.”
Without a management plan, security is just a “patchwork” of fixes. Good management turns these fixes into a consistent routine. It protects your company from expensive mistakes, maintains your customers’ trust, and ensures your compliance with the law.
DSM Types: Frameworks, Controls, and Strategic Approaches

Data security management encompasses various types and approaches. The table given below provides a quick overview of the types.
| Category | Type / Framework | Primary Focus |
|---|---|---|
| Framework-Based | NIST Cybersecurity Framework | Risk-based data protection using Identify, Protect, Detect, Respond, and Recover functions across environments. |
| ISO 27001 / ISO 27002 | Establishes an ISMS with controls for confidentiality, integrity, and availability (CIA) | |
| SOC 2 | Assesses service organizations on security, availability, processing integrity, confidentiality, and privacy | |
| Control-Based | Access Management | Enforces least-privilege access through RBAC, MFA, and zero-trust models |
| Encryption & Masking | Secures data at rest, in transit, and in use using AES encryption, tokenization, and masking | |
| Data Loss Prevention (DLP) | Detects, monitors, and prevents unauthorized data exfiltration across endpoints and networks | |
| Strategy-Based | Cloud Security (CSA CCM) | Provides cloud-specific controls for data governance, identity management, and compliance mapping |
| Risk & Compliance Frameworks | Strengthens governance, audit readiness, and prioritized safeguards against cyber threats |
Confidentiality, Integrity, and Availability: Foundations of Data Security

CIA stands for Confidentiality, Integrity, and Availability. These three are the foundations of any good data security management system.
Confidentiality ensures data access is restricted to authorized users only, using measures like encryption and access controls.
Integrity protects data from unauthorized modification or corruption, maintaining accuracy through hashing and digital signatures.
Availability guarantees timely access to information and systems for authorized users, supported by redundancies and DDoS defenses.
Also Read: How the Importance of Data Security Affects Everyone in 2025?
DSM Toolkit 2026: Protecting, Monitoring, and Managing Your Data Effectively
To build a strong data security management (DSM) program in 2026, you need a toolkit that covers the entire lifecycle of your information. Rather than one “do-it-all” software, most successful organizations use a combination of specialized tools to protect, monitor, and manage their data.
Here are four types of tools you need to use:
1. Discovery and Sorting (Classification)
Before you can protect data, you have to locate it. These tools scan your entire network, including emails, cloud storage, and databases, to identify where sensitive information, such as credit card numbers or internal strategy documents, is hiding.
Examples:
- Varonis: A powerful platform that finds sensitive data and automatically points out who has access to it.
- Spirion: Specifically designed to hunt for “personal” data (like IDs or health records) across all your devices to help you stay compliant with privacy laws.
2. Digital Keys and Entry (Access Management)
These tools act as the “security guards” for your digital office. They cross-verify everyone, even if someone has a password.
Examples:
- Okta: Manages user identities and makes sure employees can only get into the specific apps they need for their job.
- Keeper Security: A secure “vault” for company passwords and secret keys, preventing employees from using weak passwords or writing them down.
3. Making Data Unreadable (Encryption)
If a hacker does manage to steal a file, encryption ensures they can’t actually read it.
Examples:
- AxCrypt: A simple tool for encrypting individual files or folders, perfect for teams that share sensitive documents frequently.
- HashiCorp Vault: A more technical tool used by developers to manage secret “keys” and keep data scrambled across large, complex systems.
4. Watching for Red Flags (Monitoring)
These tools act like security cameras. They watch out for unusual behavior, like an employee suddenly downloading thousands of files in the middle of the night.
Examples:
- CrowdStrike Falcon: Watches your computers (endpoints) for signs of a break-in or a virus before it can spread.
- Splunk: Collects “logs” (digital footprints) from all your systems and uses them to create a dashboard that shows your overall security health.
Case Study: Smart Steps for Strong Data Security
The case study from the National e-Governance Division focuses on how data and systems must be kept safe when using AI in government work. It shows that unprotected data can be a target for attacks. The study highlights risks such as bad data being added on purpose and attackers trying to fool AI systems to get access to private information.
It explains that governments need clear steps to check and protect data at every stage of an AI project. The study also says that learning from experts and following strong security practices helps keep data safe and builds trust in digital services.
10 Essential Data Security Management Tips for 2026
Here are 10 tips for good Cybersecurity management that you need to keep in mind:
- Scan your network regularly to find and label every piece of sensitive data.
- Require a second form of ID (MFA) for every single employee login.
- Grant employees access only to the specific files they need for their roles.
- Keep your software and systems updated to close known security gaps.
- Encrypt all sensitive files both while they are stored and while they are sent.
- Automate your data backups and test them to ensure they actually work.
- Teach your team how to spot and report suspicious emails or links.
- Permanently delete old information that your business no longer requires.
- Watch for unusual activity, like large file downloads at odd hours.
- Create a simple, clear plan for what to do if a security breach occurs.
Also Read: Safeguard Your Digital Assets: Comprehensive Cyber Security Services Explained
Conclusion:
In 2026, data security management is no longer a technical chore; it is the cornerstone of a resilient and respected business. By focusing on the human side of security and balancing between privacy, accuracy, and access, you protect more than just files; you protect your people and your future. As the digital world becomes complex, a clear and proactive strategy ensures your organization thrives. Secure your data today to build the lasting trust your enterprise needs to lead tomorrow.
FAQs
1. How does data security management differ from traditional IT security?
Traditional IT security focuses on protecting the “pipes” and hardware, like routers and servers. DSM focuses specifically on the “water” inside, the actual information. It ensures that the data itself is encrypted, accurately maintained, and accessible only to authorized users.
2. How often should we update our security policies?
You should review your policies at least annually or whenever you adopt new technology. Digital threats evolve rapidly, and regular updates ensure your rules reflect current risks. Constant refinement helps your team stay prepared and keeps your security measures aligned with modern standards.
3. Can we automate our data security management?
Yes, automation is essential for modern businesses. You can use tools to automatically find sensitive files, manage user permissions, and alert you to suspicious behavior. This reduces human error and allows your team to focus on growth rather than manually checking every file.






