How do you think hackers exploit tiny gaps in software to take full control of a system? One of the most common ways they do this is through a buffer overflow or buffer overrun. This cybersecurity flaw happens when a program stores more data in a memory space than it’s meant to hold, leading to serious vulnerabilities.
When that happens, attackers can manipulate the extra data to crash programs or even run malicious code. It’s a hidden threat buried deep in computer memory. It is small in size, but it can have a massive impact.
In this article, we’ll break down what a buffer overflow is, how it works, and how you can prevent it from becoming a security nightmare.
What is Buffer Overflow and How Does It Work?
A Buffer Overrun happens when a program tries to put more data into a buffer than it can hold. A buffer is just a small storage area in memory. When too much data is sent to it, the extra data “overflows” into nearby memory spaces. This can overwrite important information and cause the system to behave unpredictably.
Here’s How the Attack Works
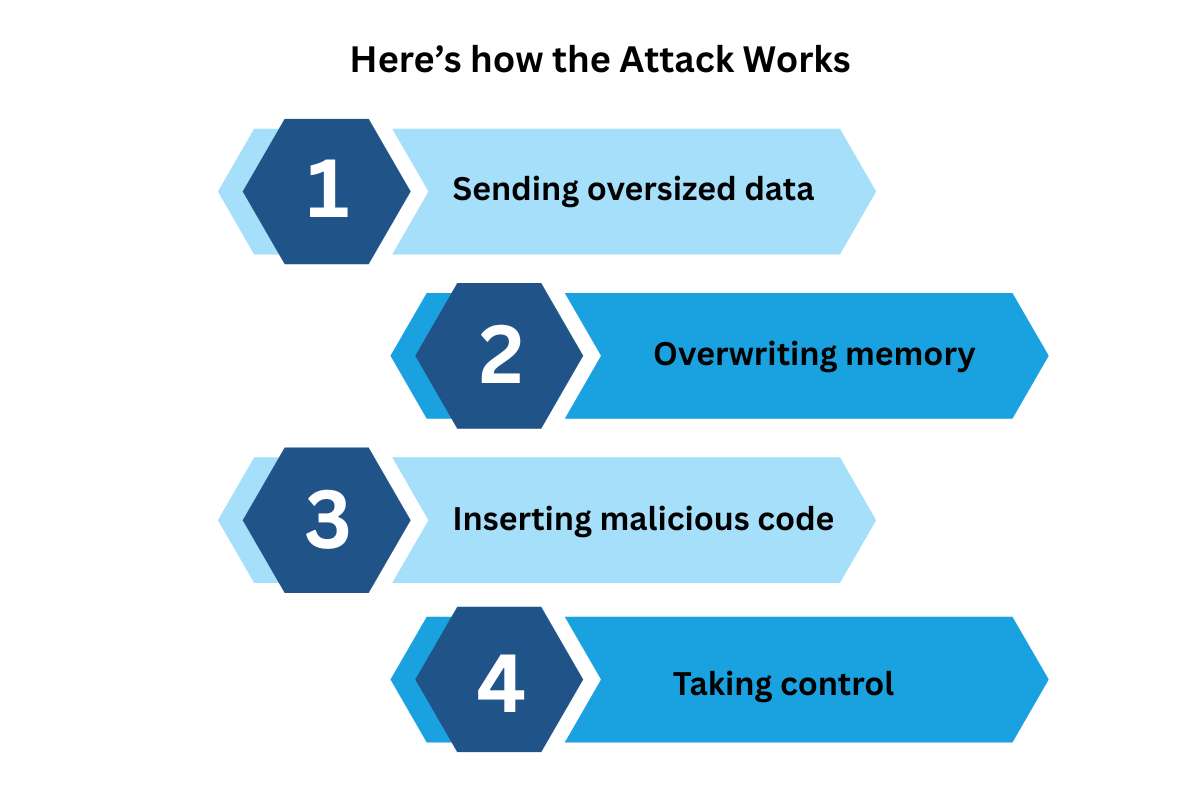
Finding a weak spot: Hackers look for programs that do not check the size of the input they receive.
1. Sending Oversized Data:
They send data that is too large for the program’s buffer.
2. Overwriting Memory:
This extra data spills over into nearby memory locations.
3. Inserting Malicious Code:
Attackers use this overflow to insert and run harmful code.
4. Taking Control:
The malicious code can change how the system behaves or give hackers full control.
Think of a cup meant to hold 200 ml of water. If you pour 400 ml, the cup overflows and spills. The same idea applies to memory in computers when the buffer’s limit is exceeded.
What are the Different Types of Buffer Overflow Attacks?
Buffer Overflow attacks can take many forms, depending on how the memory is misused. Here are some common types:
1. Stack-Based Buffer Overflow
This is the most common type. It targets the stack, where function data like return addresses and variables are stored. When the stack overflows, an attacker can overwrite the return address. This lets them redirect the program’s flow to run their own code.
2. Heap-Based Buffer Overflow
This one targets the heap, which stores data created during program execution. Attackers overflow the heap to change memory pointers or overwrite data. It’s harder to perform than stack attacks, but it can still be dangerous.
3. Off-by-One Errors
In Off-by-One Error attacks, an extra byte of data is written past the buffer’s end. Though small, this tiny overflow can change a program’s control data, allowing attackers to cause crashes or gain limited access.
4. Format String Vulnerability
Here, attackers insert format specifiers into user inputs. If a program doesn’t handle these correctly, attackers can use them to read memory or inject code.
Each type exploits how memory is managed in a program. For example, the Morris Worm used a stack-based overflow, while Heartbleed was closer to a heap-based issue. Understanding these types helps cybersecurity experts recognize and stop such attacks faster.
What Causes a Buffer Overflow?
Buffer Overflow often occur due to poor programming habits or a lack of safety checks. Let’s look at the main causes in detail:
1. Lack of Boundary Checking
When a program doesn’t check how much data is entering a buffer, it allows more data than expected. This unchecked input is one of the biggest reasons for overflows. Developers must always verify input sizes before storing them in memory.
2. Unsafe Programming Languages
Languages like C and C++ give programmers direct memory access. While powerful, they don’t have built-in safety checks. This makes them prone to buffer issues if the programmer forgets to set limits or validation.
3. Poor Input Validation
Programs often take user input without checking its format or length. If attackers send unexpected input, it can break the program’s logic and cause overflows. Validating all input is key to preventing this.
4. Complex Code and Human Error
Large or messy codebases make it easy for developers to miss vulnerabilities. Even a single missed “size check” or wrong variable declaration can open the door to attacks.
5. Legacy Systems and Old Software
Many old systems were built before modern security standards existed. They often lack the protection methods that newer software includes, leaving them open to classic buffer problems.
How to Prevent and Mitigate Buffer Overflow?
Developers and organizations can take many steps to prevent Buffer Overflow attacks.
1. Use Safe Programming Languages:
Languages like Python, Java, and C# automatically manage memory and perform boundary checks. This makes it harder for overflows to happen, even by mistake.
2. Apply Compiler Protections:
Modern compilers include safety tools like Stack Canaries, which detect unexpected memory changes. These can stop attacks before they take control of a program.
3. Enable Address Space Layout Randomization (ASLR):
ASLR changes where programs and data are stored in memory every time they run. This makes it difficult for attackers to predict where their malicious code will land.
4. Keep Software Updated:
Regular updates patch known security holes that hackers can use. Failing to update can leave systems open to attacks already discovered and shared publicly.
5. Practice Secure Coding:
Developers should follow secure coding practices such as checking input sizes, sanitizing data, and using tested libraries. Reviewing code for safety can prevent many problems before they happen.
6. Use Security Testing Tools:
Automated testing tools like fuzzers or static analyzers can detect buffer issues before deployment. These tools simulate attacks and help identify weaknesses in the code.
These steps are part of a larger cybersecurity education effort. Teaching developers about Buffer Overflow and safe coding builds stronger defenses. Training also helps teams understand how small mistakes can lead to big security risks.
Real-World Case Studies of Buffer Overflow
1. The Morris Worm (1988)
One of the first known large-scale cyberattacks was the Morris Worm. It used a stack-based Buffer Overflow in a UNIX program called “finger.” The worm spread automatically, infecting thousands of systems and slowing networks worldwide. It caused an estimated $100,000–$10 million in damage. This incident showed how a simple programming flaw could lead to massive security failures.
2. The Heartbleed Bug (2014)
The Heartbleed Bug was a heap-based Buffer Overrun found in the OpenSSL library, which is used for encrypting internet traffic. It lets attackers read sensitive data like passwords, keys, and private information from the memory of affected systems. Millions of websites were impacted before patches were released. Heartbleed highlighted how even trusted software can hide serious flaws.
Both these cases show that Buffer Overflow vulnerabilities can affect systems across decades, from early internet tools to modern encryption libraries. They show the need for regular coding, updates, and cybersecurity education.
Conclusion:
Buffer overflow may sound technical, but its effects are anything but small. It can open doors for attackers, corrupt data, and bring entire systems to a halt. Understanding how this flaw works is the first step to stopping it. Coding practices and strong security testing are key layers of protection. Staying alert and updated ensures that what starts as a simple overflow never turns into a full-blown breach.
FAQs
1. How can developers prevent buffer overruns?
Prevention includes using safe programming languages, bounds checking, address space layout randomization (ASLR), and compiler security features that detect or block unsafe memory operations.
2. Why are buffer overruns dangerous?
They’re dangerous because attackers can use them to run unauthorized code, gain admin access, or crash critical systems. This makes them one of the oldest yet most effective hacking techniques.
3. Can operating systems stop buffer overruns automatically?
Modern operating systems include protections like Data Execution Prevention (DEP) and stack canaries, which make buffer overrun attacks harder, but no system is completely immune without secure coding practices.






