In 1995, IBM Vice President John Patrick coined the term “ethical hacking.” Since then, it has been a tool for safety and precautions. And no, it is nothing like what they show in the movies and shows. An ethical hacker isn’t a gloomy figure sitting in a dark basement; instead, they are an integral part of the cybersecurity system in every company.
So, what is ethical hacking or white hat hacking? That’s what we will try to understand in this blog. We will go through its definitions, use cases, tools, and benefits. So, keep reading to find out!
What is White Hat Hacking? Definitions

White hat is the authorized practice of testing a system’s defenses by simulating real-world cyberattacks. Using the same tools and mindsets as malicious actors, ethical hackers legally probe for vulnerabilities such as software bugs or weak passwords.
Their goal is to identify and fix these security gaps before attackers exploit them. It ensures data stays protected, and digital trust remains intact.
Here’s how some of the top cybersecurity firms define white hat hacking:

- IBM Definition: Ethical hacking involves friendly parties using hacking techniques to uncover, understand, and fix security vulnerabilities in networks or computer systems.
- EC-Council Definition: A cybersecurity professional who simulates real-world cyberattacks with client direction, delivering risk assessments and improvement recommendations.
- Kaspersky Definition: Authorized attempts to breach systems or instigate data breaches to mimic malicious strategies, identifying vulnerabilities for remediation while maintaining confidentiality.
Difference between White Hat Hacking and Black Hat Hacking
| Ethical Hacking (White Hat) | Aspect | Unethical Hacking (Black Hat) |
|---|---|---|
| Identify and fix vulnerabilities to strengthen security | Purpose | Exploit vulnerabilities for theft, disruption, or harm |
| Authorized with permission; fully legal under contracts | Legality | Unauthorized; illegal under laws like the CFAA |
| Explicit consent from system owners | Authorization | No permission; invasive and secretive |
| Reports findings for remediation; improves defenses | Outcome | Causes data breaches, financial loss, or system damage |
| Uses the same tools (e.g., penetration testing) with full disclosure | Techniques | Uses the same tools but in a hidden and destructive manner |
How Ethical Hacking Works? Core Phases
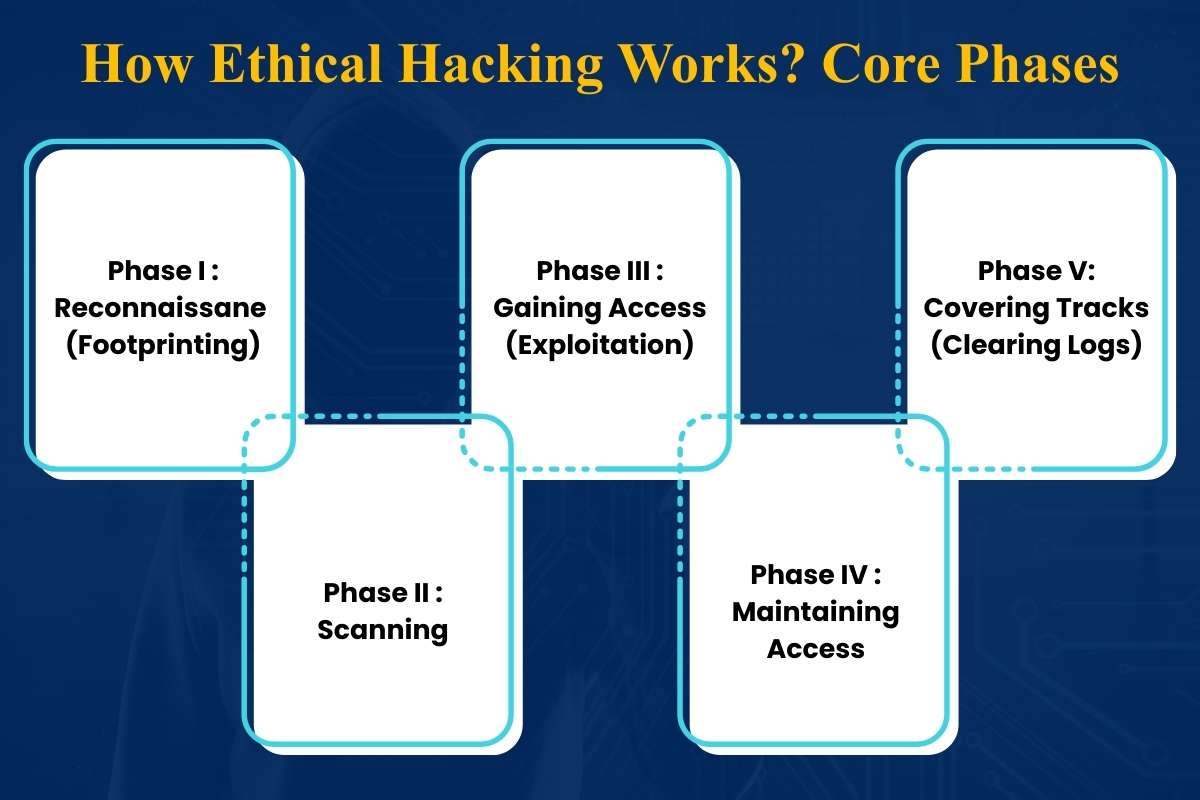
White hat hacking works in five phases. Here’s how they take place:
Phase I: Reconnaissance (Footprinting):
It is the information-gathering phase of the process. Hackers collect data about the target’s infrastructure, employees, and public records.
- Passive Recon: Gathering data without direct interaction (e.g., social media or WHOIS records).
- Active Recon: Interacting directly with the system (e.g., calling the help desk) carries a higher risk of detection.
- Tools: Maltego (link analysis), Shodan (IoT search), theHarvester (email/domain OSINT)
Phase II: Scanning:
Using the information from phase one, the hacker probes the network for specific entry points. They look for live hosts, open ports, and outdated software versions using tools like Nmap or Nessus.
- Tools: Nmap (port discovery), Nessus (vulnerability assessment), ZMap (fast internet-wide scans)
Phase III: Gaining Access (Exploitation):
This is where the actual “break-in” occurs. The hacker exploits vulnerabilities such as weak passwords or software bugs to gain control of a system or application.
- Tools: Metasploit (exploit framework), Burp Suite (web apps), SQLmap (database injection)
Phase IV: Maintaining Access:
Once inside, the goal is to stay there. Ethical hackers simulate how a real attacker would ensure they don’t lose their connection, often by creating “backdoors” or installing persistent scripts that survive a system reboot.
- Tools: Cobalt Strike (adversary simulation), Sliver (C2 framework), NetExec (lateral movement)
Phase V: Covering Tracks (Clearing Logs):
In the final technical step, the hacker tries to erase the digital “fingerprints” of the intrusion. It includes deleting log files, altering timestamps, and removing any tools or scripts used during the process to remain undetected.
- Tools: Meterpreter (in-memory execution), Log-clearing scripts, Proxychains (hiding IP).
But that’s not the end, there is one step left to do.
The Final “Sixth” Step: Reporting:
Unlike malicious hackers, the ethical process always concludes with a detailed report. This document translates technical findings into actionable advice, helping the organization patch the holes and improve its overall security posture.
Also Read: Understanding Hacking Types: A Comprehensive Overview
Essential All-in-One Platforms

For most professionals, the best way to access these tools is through a specialized operating system.
- Kali Linux: The industry standard. It comes pre-installed with over 600 tools for penetration testing, forensics, and reverse engineering.
- Burp Suite (Pro): If you are focusing on web applications or APIs, this is the most critical tool for intercepting and testing traffic in 2026.
- OWASP ZAP: A powerful, free open-source alternative to Burp Suite, perfect for teams looking to automate security in their development pipeline.
Why Ethical Hacking is Vital in 2026? The Benefits You Need to Know

In 2026, threats move faster than traditional software can patch. Ethical hackers provide a “human” layer of intuition that catches logic flaws automated tools often miss. Modern customers choose brands they can trust. Publicly investing in offensive security measures proves a company is serious about protecting personal data.
It shifts the conversation from “Are we safe?” to “Where are we vulnerable?” This allows leaders to spend their security budgets on the areas that actually matter. With stricter global data laws, simply having a firewall isn’t enough. Regular testing ensures you meet legal standards while actually staying secure.
Conclusion:
In 2026, cybersecurity is no longer a luxury; it is a survival skill. As digital threats grow more sophisticated, organizations must move beyond reactive defense. Ethical hacking provides the proactive insight needed to stay ahead of attackers, turning hidden vulnerabilities into fortified strengths.
It bridges the gap between technical security and human trust, ensuring that a brand’s reputation is as resilient as its network. By integrating white hat hacking into their core strategy, hackers do more than protect data; they build a risk-aware culture prepared for whatever the next digital frontier brings.
Also Read: Best Cybersecurity Tools for Companies in the USA
FAQs
1. Is ethical hacking legal?
Yes, it is entirely legal because it is performed with explicit, written permission from the system owner. Ethical hackers sign contracts and follow strict rules to ensure they stay within legal boundaries while helping organizations find and fix security flaws.
2. How does it differ from “regular” hacking?
The main difference lies in intent and authorization. Ethical hackers use their skills to protect systems and keep data safe. Malicious hackers, however, break into systems without permission to steal information, cause damage, or demand ransom for personal gain.
3. Why is it essential for businesses in 2026?
In 2026, cyber threats are faster and more complex. Ethical hacking provides a proactive “human” perspective that automated software often misses. It helps companies identify real-world risks, build customer trust, and ensure their security measures actually work before an attack happens.






