Data breaches and cyberattacks are making daily headlines. Protecting sensitive information has never been more critical. Data tokenization is a smart, secure way to keep personal and financial data safe without losing its usefulness.
This security method replaces sensitive information, like credit card numbers or personal IDs, with random, unique tokens that hold no real value outside a secure system. It allows businesses to store, process, and transfer information safely and reduce the risk of exposure. From online payments to healthcare records, tokenization helps organizations safeguard trust and compliance while maintaining seamless operations.
In this blog, we’ll explore what data tokenization is, how it works, and why it’s becoming one of the most reliable defenses in modern data security.
How Does Data Tokenization Work?
At its core, tokenization changes real information into a random token. The token has no direct link to the original data and cannot be reversed without proper authorization.
For example, a credit card number might become “3894-XXXX-9281.” The actual number is stored separately in a secure database called a token vault, where only approved systems can access it.
Here’s a simple breakdown of how Data Tokenization works:
- A company’s system receives sensitive information, such as a credit card number or ID.
- The tokenization service creates a random token to replace the real value.
- The system stores the token and removes the original data from common databases.
- When necessary, the original data can be retrieved through secure detokenization.
Some organizations use another method known as vaultless tokenization. It depends on algorithms rather than a central storage system. This model improves speed and scales easily for cloud-based operations. Both methods reduce the amount of sensitive information stored in plain form.
What are the Different Types of Data Tokenization?
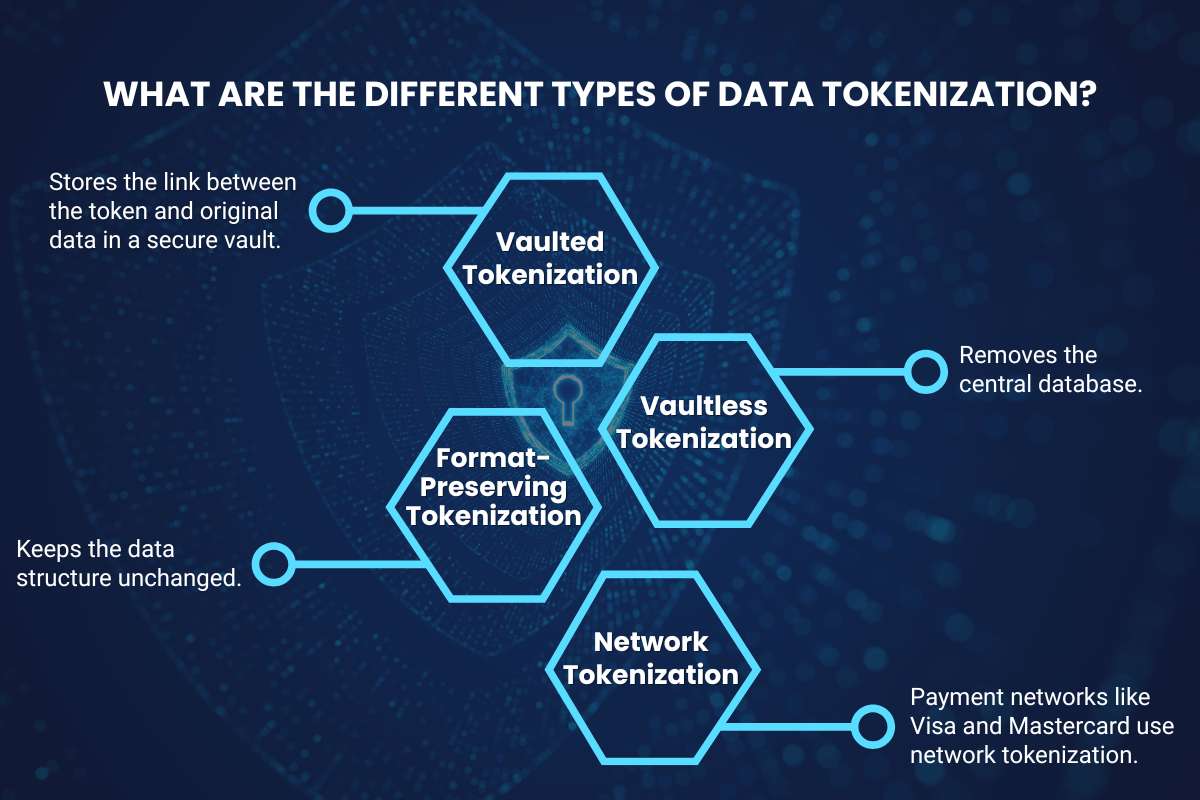
Different industries and systems use different types of Data Tokenization. The choice depends on performance needs, compliance standards, and system design.
1. Vaulted Tokenization
Vaulted tokenization stores the link between the token and original data in a secure vault. Access to this vault is tightly controlled. It’s a reliable option for banks and government systems that prefer centralized oversight. However, it can slow down performance when processing large volumes of transactions.
2. Vaultless Tokenization
Vaultless tokenization removes the central database. Instead, it uses encryption and algorithms to generate and verify tokens. This type is faster, more scalable, and ideal for cloud platforms or real-time applications.
3. Format-Preserving Tokenization
Some systems need data to remain in a specific format. For example, a 16-digit credit card field still needs to show 16 digits, even when tokenized. Format-preserving tokenization keeps the data structure unchanged, making it compatible with older applications.
4. Network Tokenization
Payment networks like Visa and Mastercard use network tokenization. Each payment token is linked to a specific card, device, and merchant. Even if a token is stolen, it cannot be reused elsewhere. This makes mobile wallets and online payments much safer.
The 5 Key Benefits of Data Tokenization

Organizations that use tokens gain a wide range of advantages. They can be security, financial, and operational benefits.
1. Strong Data Protection
If attackers access a company’s database, they only find random tokens. Since tokens have no real-world meaning, the stolen data remains useless. This simple layer of defense helps reduce the impact of breaches.
2. Easier Compliance
Tokenization supports compliance with laws such as PCI DSS, GDPR, and CCPA. When sensitive data is replaced with tokens, fewer systems fall under audit requirements. This lowers compliance costs and reduces the time needed for reviews.
3. Improved Customer Confidence
Customers expect their personal information to be safe. When companies use data tokenization, they show a clear commitment to privacy. That trust can lead to stronger customer relationships and loyalty.
4. Safer Data Sharing
Departments, partners, and third-party vendors can work with tokenized data instead of real information. This makes testing, analytics, and reporting safer without disrupting daily operations.
5. Lower Risk and Cost
Breaches are expensive. They cause fines, legal action, and lost revenue. By reducing the amount of sensitive data stored, tokenization limits potential losses and simplifies insurance and recovery efforts.
Also Read: Can Secure Sockets Layer Truly Protect Your Data in 2025?
How is Data Tokenization Used in Different Industries?

Many industries handle sensitive or regulated information. Using tokens has become a standard practice across several such sectors. The majority of them include:
1. Banking and Financial Services
Banks use tokenization to secure account numbers, payment card data, and transaction details. Mobile payment services such as Apple Pay and Google Pay rely on tokenization to protect customer information during every transaction. The financial sector has seen fewer breaches and lower fraud rates since adopting this technology.
2. Retail and E-Commerce
Retailers process thousands of online and in-store transactions daily. Tokenization replaces real card numbers with tokens, reducing the risk of theft. It also allows recurring billing and loyalty programs to operate securely without storing sensitive payment details.
3. Healthcare
Hospitals and clinics manage large amounts of personal and medical information. With data tokenization, they can store, transfer, and analyze data safely. Researchers can access de-identified patient information without exposing real records. This helps organizations stay compliant with privacy laws like HIPAA.
4. Cloud and SaaS Providers
As companies move workloads to the cloud, protecting sensitive data becomes more complex. Vaultless tokenization works well in these environments because it eliminates the need for a central vault. Cloud service providers use it to protect customer data while keeping applications fast and efficient.
5. Government and Public Services
Government systems store critical information such as tax details, social IDs, and official records. Tokenization helps secure this data and limits unauthorized access. It also prevents identity theft in large-scale public databases.
Data Tokenization in Action: Real-World Case Studies

1. Visa: Network Tokens for Global Security
Visa’s Token Service replaces payment credentials with secure tokens. Each token is unique to a device and merchant, protecting recurring and online transactions. Visa reports that tokenized payments experience fewer fraudulent charges than traditional card payments.
2. Albertsons: Tokenization in the Cloud
Retail chain Albertsons used vaultless tokenization to protect customer data during a cloud migration. The solution secured sensitive information while supporting large-scale analytics. This allowed the company to modernize its operations without risking customer privacy.
Steps to Implement Data Tokenization
Adding a tokenization system to your organization involves planning and consistent testing.
1. Identify Sensitive Data:
Find what needs protection, such as financial, health, or identity information.
2. Choose the right model:
Vaulted or vaultless tokenization depends on your system’s needs and performance goals.
3. Set access permissions:
Control who can detokenize and access original data.
4. Combine with encryption:
Tokenization hides data, but encryption protects it while it moves across networks.
5. Test and monitor systems:
Run regular tests to ensure tokens work in analytics, billing, and customer applications.
Common Mistakes to Avoid while Implementing Data Tokenization
Some organizations make simple mistakes that weaken their data protection strategies. Avoid the following pitfalls:
- Leaving token vaults unprotected or poorly monitored.
- Relying on tokenization as the only security measure.
- Ignoring updates to privacy laws in different regions.
- Failing to audit or monitor data flows regularly.
Keeping these issues under control helps maintain long-term data safety.
Conclusion:
Cyber threats are changing every day, and data tokenization stands out as a simple yet powerful tool for protecting sensitive information. Organizations can reduce the impact of data breaches and maintain customer trust by replacing real data with secure tokens. It keeps data safe and supports compliance with global security standards like PCI DSS and GDPR.
In an age where digital trust defines success, adopting tokenization is a smart business move toward a safer digital future.
FAQ
1. What types of data can be tokenized?
Common examples include payment card details, Social Security numbers, personal identification data, and medical records. Essentially, any information that needs privacy protection.
2. How does data tokenization differ from encryption?
Encryption scrambles data using a key that can be reversed, while tokenization replaces data with tokens that cannot be mathematically reversed, making it harder for hackers to retrieve the original information.
3. Can tokenization be combined with other security methods?
Yes, tokenization often works alongside encryption, firewalls, and access control systems to build a stronger, layered defense strategy.
4. Are there any guidelines that I need to follow while implementing tokenization?
Yes, you can follow the Security Standards Council’s Tokenization Guidelines.






