Introduction
Computers and technology are ruling the modern world. With an immense efficiency rate, they play a pivotal role in helping businesses function effortlessly and increase revenue. Wielding this powerful tool has a negative aspect. Well, it is not about the functioning of the technology, but it is more about safeguarding a company from possible breaches.
The world is now aware of the importance of cybersecurity. There are several cybersecurity domains, and an important one is threat modeling. This article delves more into the role threat models play in safeguarding companies from security breaches and the different types.
The role of threat models in preventing security breaches
The Definition of Threat Modeling

The main work of this includes understanding the threats, communicating, and identifying them to protect a particular company’s system or network. The IT team of a company uses threat models to research and assess the vulnerabilities of a system. This provides insight into understanding and predicting the nature of threats.
Companies must have a clear and concise understanding of the possible threats. By taking proper measures, they can protect their sensitive and confidential information from possible security breaches that could impact their profits.
Importance of Threat Modeling: Why is it Necessary?
Undoubtedly, companies around the world have been digitalized. They prefer more cloud-based systems to safeguard confidential information that measures a company’s growth and network systems. Running cloud-based systems increases the risk factor of cyber threats. Companies will become vulnerable with the information available. There is a significant rise in the number of cyber threats. Hackers use various techniques to break into a company’s system. The motive behind it depends, and in some cases, even the employees try to steal and tamper with the data.
Some companies that have just started or are in the initial years of the establishment are more vulnerable to these threats. The aftermath of these cyber threats can cause a major downfall. So, companies must take cybersecurity measures. Threat modeling is one of the effective cybersecurity tools to use against hackers. It helps IT professionals assess the possible risks, understand the company’s core applications, and protect them from malicious threats.
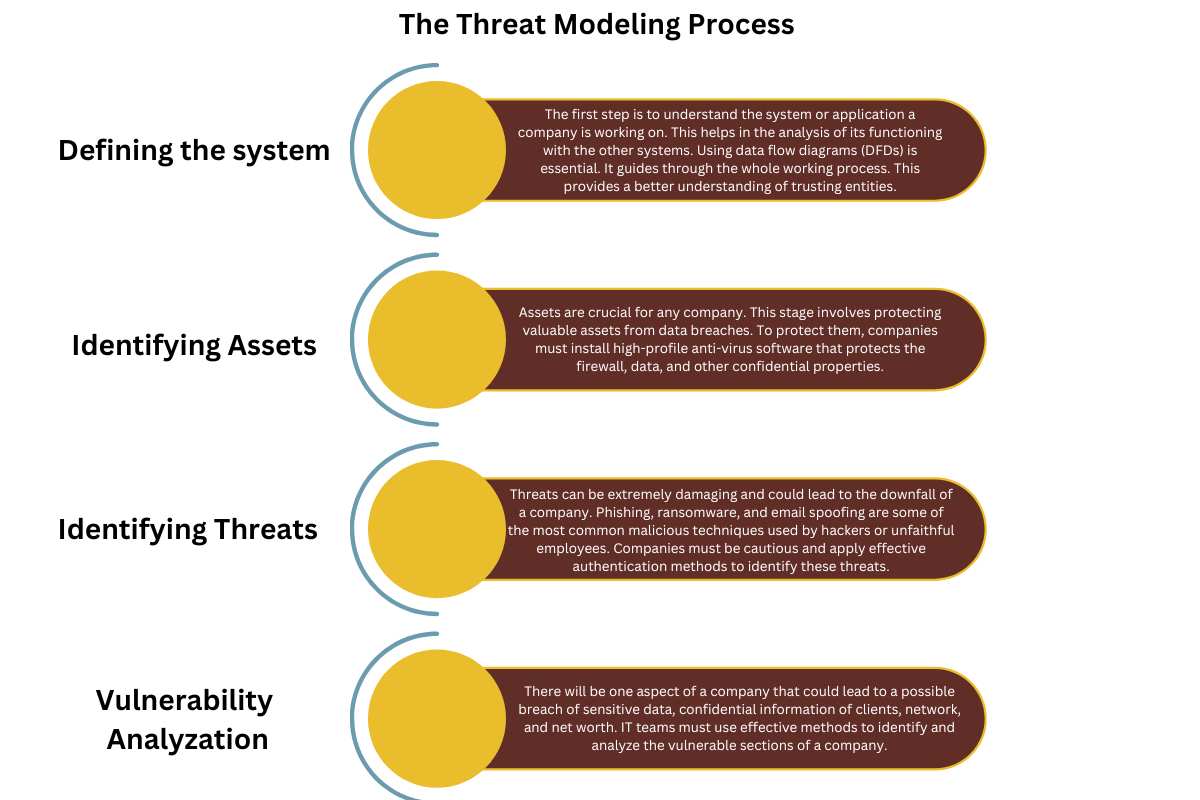
The Threat Modeling Process
To ensure an effective defense mechanism, it is a must to follow a structured threat modeling process.
It includes:
Threat Modeling Frameworks and Methodologies
A threat modeling framework helps a company improve the efficiency of identifying and tackling harmful threats.
Here are the four best methodologies:
1. STRIDE
STRIDE was developed by Microsoft and is one of the oldest framework methods to analyze threats in a system. This is a free tool and produces DFDs to analyze threats based on six common security risks.
STRIDE is designed to tackle seven types of threats and they are:
- Spoofing- When an entity pretends to be from a legitimate source by sending emails to access the confidential information of a company.
- Tampering- When hackers try to tamper with the firewall or the security codes of a system of a company.
- Repudiation- There is a possibility of not having sufficient evidence to prove the malicious activity. Hackers leverage this to escape from the law.
- Information Disclosure- This involves losing sensitive information to malicious sources.
- Denial-of-Service (DoS)- Hackers try to block the legitimate functioning of a company by overloading the system with traffic.
- Elevation of Privilege- Hackers try to gain unauthorized access to a company that would disrupt the whole operation.
2. PASTA

PASTA (Process for Attack Simulation and Threat Analysis) is a framework that combines a business objective with technical requirements. This framework slides in the inputs from the stakeholders and not just only from the IT department.
The PASTA framework involves seven steps, and they are:
- Definition of objectives
- Defining the technical assets
- Threat analysis
- Analysis of vulnerabilities
- Decomposition
- Attack modeling
- Risk management
3. VAST
VAST refers to visual, agile, and simple threat modeling methods developed by ThreatModeler. Major companies implement the VAST model across their infrastructure to maintain an efficient and reliable process to tackle cyber threats. It also uses the principles of the DevOps Lifecycle.
There are two types of VAST threat models:
- Application threat model: It involves the usage of process-flow diagrams to represent the constructive aspect of the threat.
- Operation threat model: This model uses data-flow diagrams to understand and predict the threats.
4. Attack Trees
This is one of the most used modeling methods to fight against cyber threats. The IT team assesses the possible vulnerabilities of a company using graphic representations of the system. It is designed in such a way that the trunk of the attack tree represents the assets, while the branches and roots represent the entry points and threats.
Best Threat Modeling Tools and Software
Here are the top three tools and software to improve the efficiency:
- Microsoft Threat Modeling Tool
- OWASP Threat Dragon
- IBM Security AppScan Source
- CAIRIS
- ThreatModeler

Conclusion
It is clearly understood that the present world is highly influenced by the power of technology and computers. Certainly, it is a great progress, but there also comes a crucial task of protecting it from the people who try to access it with a negative intention.
To tackle all these issues, companies or enterprises must install effective cybersecurity measures, and threat modeling is one of the best methods to deal with cyber threats. It helps in understanding the nature of the threat and communicating it to protect the system or network of a company. It is a must that an IT team of a company follows the process of threat modeling and uses the correct methodologies to build rigid firewall systems.






