Hardware Security Modules (HSMs) are physical devices used to protect and manage encryption keys, ensuring data security. They prevent unauthorized access, offer tamper resistance, and support compliance with standards like PCI DSS and GDPR. HSMs improve performance, reduce insider threats, and are essential for securing sensitive data in today’s digital world.
When I first learned about Hardware Security Modules (HSMs). I was working on a project that involved sensitive customer data. Keeping it safe was a big challenge. That’s why my team introduced me to HSMs. These devices securely store and manage encryption keys, making it nearly impossible for hackers to steal the data. Using HSM gave me confidence that the data was safe, even from advanced cyber threats. I understand why HSMs are essential for protecting sensitive information in today’s digital world. In this blog, we will explore the meaning of HSM, its types, examples, and the key benefits it offers.
What is a Hardware Security Module (HSM)?
A Hardware Security Module (HSM) is a physical device that protects and manages digital keys, encrypts data, and performs secure cryptographic operations. HSMs are security-hardened, intrusion-resistant, and tamper-resistant pieces of hardware that are used to provision cryptographic keys for critical functions such as encryption, decryption, and authentication for the use of applications, identities, and databases. They function as trust anchors for cryptographic operations. The most reliable HSMs are validated and certified with the strongest globally accepted security standards like Federal Information Processing Standardization (FIPS) 140-2 and FIPS 140-3.
Key Features of HSM
1. Encryption and Decryption:
HSMs use strong encryption algorithms to protect data from being read by unauthorized users.
2. Key Management
They generate, store, and manage cryptographic keys securely.
3. Tamper Resistance
HSMs are designed to detect and resist physical and logical attacks.
4. Compliance
They help organizations meet regulatory standards such as PCI DSS, FIPS 140-2, and GDPR.
How Does an HSM Work?
When a system needs to encrypt or decrypt data, it sends a request to the HSM. The HSM then performs the cryptographic operation using the secure keys stored inside it. Since the keys never leave the module, the risk of key exposure or theft is reduced.
Types of Hardware Security Modules
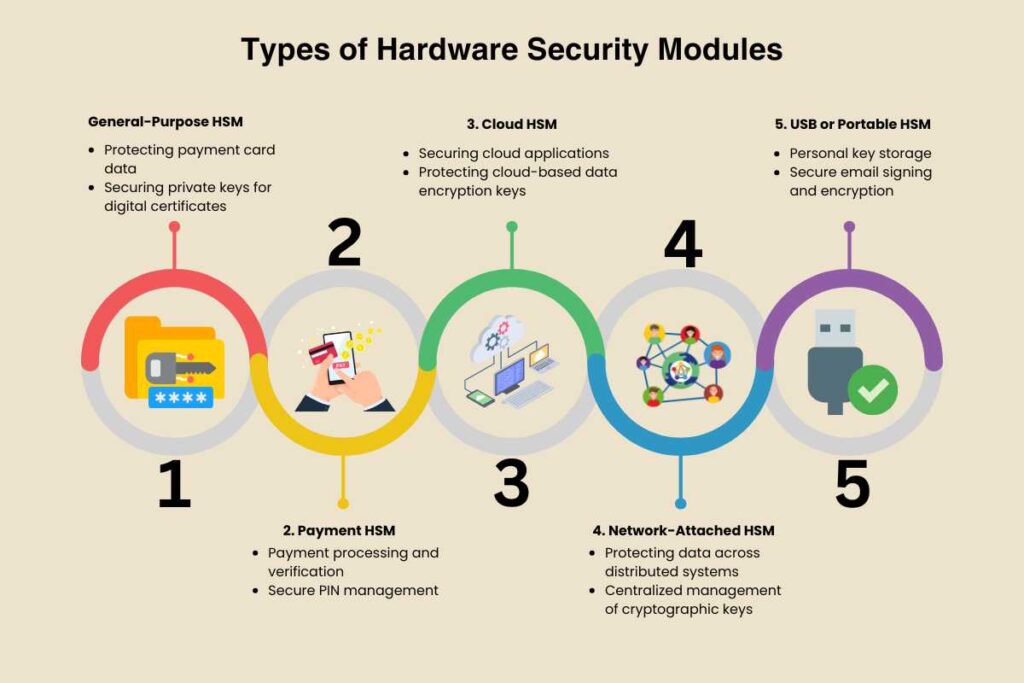
HSMs come in different forms, each designed for specific security needs. Here are the common types of HSMs:
1. General-Purpose HSM

These HSMs are used for standard cryptographic operations, such as data encryption, key management, and digital signatures. They are widely used by financial institutions, governments, and enterprises to protect sensitive information.
Use Cases:
- Protecting payment card data
- Securing private keys for digital certificates
- Encrypting sensitive customer information
2. Payment HSM
A Payment HSM is specifically designed for financial transactions. It protects payment data, such as credit card details, PINs, and transaction keys. These HSMs comply with strict standards like PCI DSS.
Use Cases:
- Payment processing and verification
- Secure PIN management
- Tokenization of payment data
3. Cloud HSM
A Cloud HSM is a cloud-based service that provides the same security functions as traditional HSMs but with the flexibility of cloud infrastructure. It is ideal for organizations that want to secure their keys without investing in physical hardware.
Use Cases:
- Securing cloud applications
- Protecting cloud-based data encryption keys
- Ensuring compliance with data privacy regulations
4. Network-Attached HSM
These HSMs are connected to a network and allow multiple applications to access them remotely. They are used for centralized key management and large-scale cryptographic operations.
Use Cases:
- Protecting data across distributed systems
- Centralized management of cryptographic keys
- Secure communication in large enterprises
5. USB or Portable HSM

These are small, portable devices that offer cryptographic security. They are ideal for individual use or small-scale operations.
Use Cases:
- Personal key storage
- Secure email signing and encryption
- Portable authentication for remote workers
Examples of Hardware Security Modules
HSMs are widely used across different industries for data security. Here are some popular HSMs used by organizations:
1. AWS CloudHSM –
- Type: Cloud HSM
- Description: AWS CloudHSM is a fully managed hardware security module service that allows businesses to generate and manage encryption keys in the cloud.
- Use Case: Protecting sensitive cloud data and meeting compliance requirements.
2. Thales Luna HSM –

- Type: Network-Attached HSM
- Description: Thales Luna HSM is a high-performance security module used for key management, encryption, and authentication.
- Use Case: Used by banks and enterprises for large-scale cryptographic operations.
3. Entrust nShield HSM –
- Type: General-Purpose HSM
- Description: Entrust nShield HSM offers robust data protection and encryption capabilities.
- Use Case: Used in healthcare and government sectors for data security and compliance.
4. Gemalto SafeNet HSM –
- Type: Payment HSM
- Description: Gemalto SafeNet HSM is used for payment processing and protecting sensitive financial data.
- Use Case: Financial institutions use it to encrypt payment data and secure PINs.
5. YubiHSM 2 –

- Type: USB/Portable HSM
- Description: YubiHSM 2 is a small, affordable HSM designed for smaller organizations. It offers cryptographic operations and key management.
- Use Case: Ideal for small businesses looking for an affordable security solution.
Benefits of Hardware Security Modules
HSMs offer several advantages to organizations by providing robust security, compliance, and operational efficiency. Here are some key benefits:
1. Enhanced Data Security –
HSMs encrypt sensitive data using strong cryptographic algorithms, making it difficult for attackers to steal or manipulate the information. They also offer secure key storage, reducing the risk of data breaches.
2. Key Management and Protection –
HSMs generate, store, and manage cryptographic keys securely. The keys never leave the module, preventing unauthorized access. This confirms that sensitive data remains protected.
3. Regulatory Compliance –
Many industries, such as finance, healthcare, and government, require strict security standards. HSMs help organizations meet compliance regulations like:
- PCI DSS for payment security
- GDPR for data privacy
- FIPS 140-2 for cryptographic module security
4. Protection Against Physical and Logical Attacks –
HSMs are tamper-resistant and designed to detect and respond to unauthorized access attempts. If someone tries to tamper with the device, it automatically erases sensitive keys to prevent theft.
5. Improved Performance and Efficiency –
HSMs offload cryptographic operations from regular servers, improving the performance of the system. This makes data encryption and decryption faster and more efficient.
6. Scalability and Flexibility –
Cloud HSMs offer scalable solutions, allowing businesses to expand their security capabilities as they grow. Organizations can integrate HSMs with multiple applications for better security management.
7. Reduced Risk of Insider Threats –
HSMs store keys separately from other systems, reducing the risk of insider threats. Even employees with server access cannot retrieve the cryptographic keys stored inside the HSM.
Conclusion
Hardware Security Modules (HSMs) play an important role in protecting sensitive data and secure cryptographic operations. Whether used for payment processing, data encryption, or key management, HSMs provide a strong layer of security. By understanding the types, examples, and benefits of HSMs, businesses can make proper decisions about implementing them to enhance data protection and meet compliance standards. With the growing need for cybersecurity, HSMs are becoming essential for organizations aiming to protect their data in a digital-first world.






