Let’s assume you get an urgent email from your CEO, requesting an immediate overseas money transfer. Later, you come to realize that the mail was fraudulent. You have unfortunately fallen prey to a Whaling Attack.
A scenario like this recently occurred at my organization, where a colleague received an email from the “CEO” asking urgently to contact him. We were confused at first, but we soon realised that many people in our company had gotten the same email. Thankfully, the incident was immediately reported. However, it did leave me wondering: How can hackers imitate a high-ranking executive so easily?
Apparently, a CEO phishing fraud is pretty common. This type of attack is also known as ‘Whaling.’ In this article, we are going to take a deep dive into Whaling and see how this type of attack works and how to detect and prevent it.
How does a Whaling Attack Work?
It is a cyber attack targeted at the senior executives of a company. Attackers invest time researching their targets. They gather information about that person from various sources. They can include public profiles, press releases, corporate filings, and even vendor leaks. Background research lets them reproduce tone and signature formats. This can make the message appear legitimate.
The attacker builds a convincing pretext. It is then delivered through email, SMS, or messaging apps. It pressures the recipient to act quickly and bypass normal verification steps. The desired action may be authorizing a wire transfer or sharing sensitive information. So, if you are a high-ranking executive, you must be aware of the messages that you receive.
How to Detect Whaling Attack?

Many scam messages are easy to detect. But Whaling messages can sometimes go undetected, which is why it is important to know the warning signs.
1. Scrutinize the sender’s email address
Whaling emails often use spoofed addresses or look-alike domains. These closely resemble legitimate ones. Carefully check the sender’s full email, including subtle spelling differences. It can help detect fraudulent messages before responding or taking any action.
2. Watch for unusual urgency or secrecy
Messages that pressure executives to act quickly, bypass normal protocols, or maintain secrecy are red flags. Attackers create a sense of emergency to prevent verification. So, any request demanding immediate financial or sensitive actions should be treated with caution.
3. Verify unexpected requests
Always confirm financial transfers or sensitive information requests. This should be done via a separate known communication channel. This helps detect impersonation attempts and ensures the request is legitimate before acting.
4. Look for inconsistencies
Whaling Attack may have subtle differences in writing style, punctuation, signature, or formatting. Noticing these inconsistencies can help identify potentially malicious messages.
5. Monitor unusual account activity
Unfamiliar auto-forwarding rules, logins from unexpected locations, or sudden changes in mailbox settings can indicate a compromised account. Regular monitoring of accounts can reveal early signs of whaling or other targeted attacks.
How to prevent Whaling Attack?
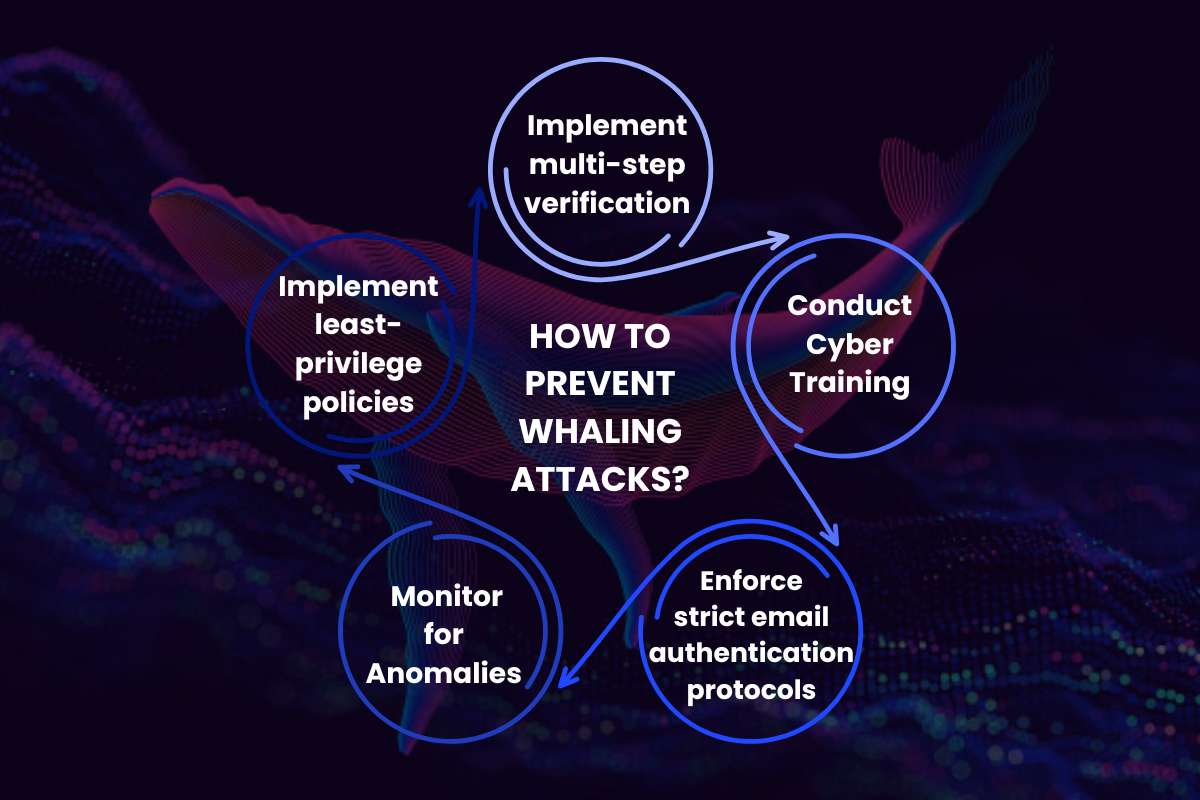
You might be able to detect Whaling attempts effectively, but constant attacks can be draining. So, having a robust security system is a must. It can detect a whaling text and save you the hassle of checking every message.
1. Implement multi-step verification
Ensure that all financial transactions and vendor payments require verification through various channels. For example, confirm the request via a phone call to a known contact or in-person approval. This additional step ensures that even convincing emails cannot bypass organizational controls. It creates an audit trail and reduces the risk of fraud.
2. Conduct Cyber Training
Targeted cybersecurity training for executives and senior staff is essential. Sessions should focus on recognizing whaling tactics. Teaching executives to pause, verify, and report suspicious emails equips them to avoid falling victim to such whaling attack. It enhances the security of an organization and reduces financial loss.
3. Enforce strict email authentication protocols
Deploy strict policies to prevent email spoofing and unauthorized domain use. These protocols verify that emails originate from legitimate sources. This blocks messages from fraudulent sources before they reach inboxes. Regular monitoring of email traffic reduces whaling attempts by neutralizing them early.
4. Implement least-privilege policies
Critical actions should require authorizations from at least two authorized personnel. This should be coupled with least-privilege access. This ensures no single individual can execute high-risk transactions. Such controls limit the potential impact of whaling attack. It also ensures accountability.
5. Monitor for Anomalies
Proactively monitor executive and finance accounts. Look for unusual activity. Unexpected mailbox rules, logins from unusual locations, or abnormal access patterns are the key signs to watch for. Early detection of these anomalies allows rapid investigation and intervention.
What is the Difference Between Whaling, Phishing, and Spear phishing Attacks?

Whaling might sound similar to a phishing attack or a spear phishing attack. But there are some key differences between them.
1. Target Audience
The first key difference lies in who the attacker targets. Phishing attacks usually aim at a broad audience. The messages sent are generic. The key is to send it to hundreds and thousands of people to maximize the chance of success.
Spear phishing, in contrast, focuses on specific individuals or small groups. They are often within a particular organization. Whaling attack go even further and target CEOs and CFOs.
2. Personalization
Another difference is the level of personalization in the attack. Phishing messages are typically generic and do not include personal details. Spear phishing emails are highly personalized. They often include the recipient’s name, position, or references to organizational information. Whaling is extremely tailored. They are carefully crafted to reference company matters, financial transactions, or executive responsibilities.
3. Objective and Impact
The final key difference is in the attacker’s goal and potential impact. Phishing attacks generally aim to steal login credentials. Spearphishing targets more sensitive data like proprietary information or access credentials. Whaling focuses on accessing confidential corporate information, manipulating financial transactions, or causing significant operational disruption.
Case Study: How Snapchat fell victim to a Whaling Attack in 2016
In February 2016, Snapchat suffered a Whaling scam. An HR employee was tricked into handing over the payroll data of employees. The attack involved an email impersonating CEO Evan Spiegel. Snapchat confirmed that no user data was compromised. They responded within 4 hours and reported the case to the FBI.
Case Study: Ubiquiti suffers financial loss due to Whaling
On June 5, 2015, Ubiquiti Networks discovered that it had been victimized by a whaling attack. A business email had targeted its financial department. The attackers impersonated executives and made fraudulent requests to transfer funds. This cost Ubiquiti over $46.7 million.
Conclusion:
Whaling attack are among the most dangerous forms of cybercrime. They exploit human trust at the highest levels of an organization. It is very important to be aware of the emails and messages you receive. Look for any abnormalities. In my colleague’s case, an email from the CEO was out of character. This made us very suspicious.
FAQ
1. What industries are most at risk of whaling attack?
A. Industries handling large financial transactions, sensitive intellectual property, or regulatory data are most at risk. This includes finance, healthcare, legal, government, and technology sectors.
2. What should you do if you suspect a whaling email?
A. If you suspect a whaling email, do not click on links, download attachments, or reply directly. Instead, report it immediately to your IT or security team.
3. How often do whaling attack occur?
A. Whaling scams are increasingly common. This is because executives have access to sensitive financial and strategic information






