Facial recognition programs have become increasingly prevalent in today’s digital landscape, revolutionizing the way we interact with technology and enhancing security measures. These programs utilize advanced algorithms to identify and verify individuals based on unique facial features. From unlocking smartphones to enhancing surveillance systems, facial recognition technology has found widespread applications across various industries. In this article, we delve into the intricacies of facial recognition programs, exploring their functionality, benefits, and concerns.
What are Facial Recognition Programs?
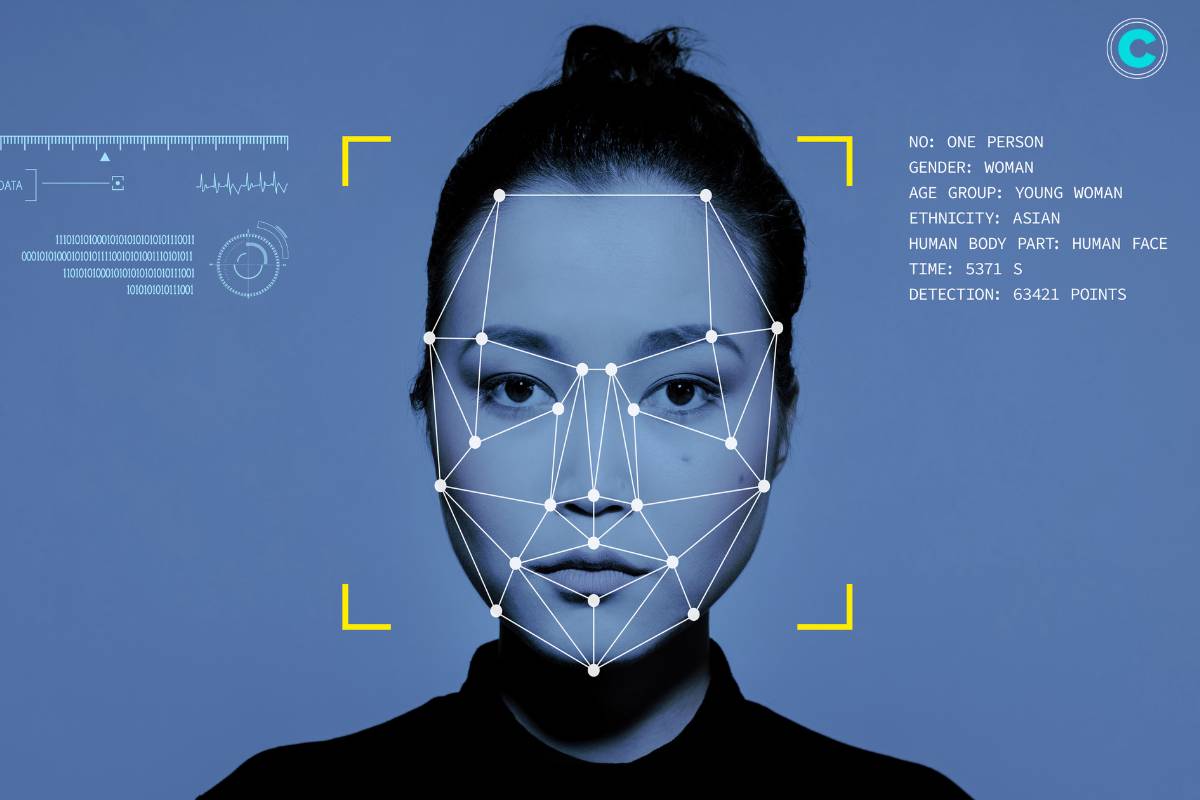
Facial recognition programs are sophisticated software applications designed to analyze and identify human faces from digital images or video frames. These programs employ artificial intelligence and machine learning algorithms to detect facial features such as the size and shape of the eyes, nose, and mouth. By comparing these features against a database of known faces, facial recognition systems can accurately recognize individuals in real-time.
How Do Facial Recognition Programs Work?

Facial recognition programs operate on intricate algorithms and processes that enable them to accurately identify individuals based on their unique facial features. Let’s delve deeper into the workings of these sophisticated systems:
1. Face Detection:
- Facial recognition programs begin by detecting faces within an image or video frame. This process involves analyzing pixel data to identify regions that resemble human faces.
- Advanced algorithms are employed to recognize patterns such as the arrangement of pixels corresponding to facial features like eyes, nose, and mouth.
2. Feature Extraction:
- Once a face is detected, the program extracts key features from the facial image. These features include the distance between the eyes, the shape of the nose, the contours of the face, and other distinctive characteristics.
- Feature extraction algorithms utilize mathematical techniques to represent facial features in a way that is conducive to comparison and matching.
3. Face Representation:
- The extracted facial features are then converted into a unique mathematical representation known as a face template or face signature.
- Face templates are compact representations of facial characteristics that facilitate efficient comparison and matching across a database of known faces.
4. Database Comparison:
- The generated face template is compared against a database of pre-existing face templates. This database may contain images and corresponding templates of individuals enrolled in the system.
- Comparison algorithms measure the similarity between the extracted face template and the templates stored in the database.
5. Matching and Recognition:
- If a sufficiently close match is found within the database, the facial recognition program identifies the individual associated with the matching face template.
- Matching algorithms employ thresholds to determine the level of similarity required for a successful match, balancing accuracy and efficiency.
6. Real-time Processing:
- Facial recognition systems are optimized for real-time processing, allowing them to quickly analyze and match faces in dynamic environments such as surveillance footage or live video streams.
- High-performance computing hardware and parallel processing techniques enable rapid execution of facial recognition algorithms.
7. Adaptive Learning:
- Some facial recognition programs incorporate machine learning and artificial intelligence to adapt and improve their performance over time.
- Through continuous exposure to new facial data and feedback mechanisms, these systems can refine their algorithms and enhance recognition accuracy.
8. Robustness to Variability:
- Facial recognition programs are designed to account for variations in facial appearance caused by factors such as changes in lighting conditions, facial expressions, hairstyles, and accessories.
- Robust algorithms employ techniques such as normalization and feature normalization to mitigate the effects of variability and ensure reliable recognition.
By combining these elements, facial recognition programs can accurately and efficiently identify individuals across diverse settings and applications. From enhancing security measures to streamlining authentication processes, the capabilities of facial recognition technology continue to advance, shaping the future of digital interaction and identity verification.
Applications of Facial Recognition Programs:

1. Security Systems:
Facial recognition technology is commonly used in security systems to authenticate users and control access to restricted areas. It provides a convenient and secure alternative to traditional authentication methods such as passwords or keycards.
2. Law Enforcement:
Law enforcement agencies utilize facial recognition programs to identify suspects captured in surveillance footage or photographs. This assists in criminal investigations and enhances public safety.
3. Biometric Authentication:
Facial recognition is integrated into smartphones, tablets, and other devices for biometric authentication. Users can unlock their devices or access sensitive information simply by scanning their faces.
4. Attendance Tracking:
In educational institutions and workplaces, facial recognition systems are used to track attendance efficiently. This eliminates the need for manual attendance records and reduces administrative overhead.
5. Marketing and Retail:
Some retailers use facial recognition technology to analyze customer demographics and behavior. This information helps them tailor marketing strategies and improve the overall shopping experience.
Benefits of Facial Recognition Programs:
1. Enhanced Security:
Facial recognition programs offer a higher level of security compared to traditional authentication methods. They are difficult to forge or manipulate, reducing the risk of unauthorized access.
2. Convenience:
Biometric authentication using facial recognition is convenient for users, eliminating the need to remember passwords or carry physical tokens.
3. Efficiency:
Facial recognition systems automate processes such as access control and attendance tracking, saving time and resources for organizations.
4. Accuracy:
Advanced algorithms ensure high accuracy in facial recognition, minimizing false positives and negatives.
5. Versatility:
Facial recognition technology can be deployed in various environments and applications, making it a versatile solution for different industries.
Concerns and Limitations:

Despite its advantages, facial recognition technology raises several concerns:
Privacy:
There are concerns about the collection and storage of biometric data, as well as the potential for misuse or unauthorized access.
Bias and Inaccuracy:
Facial recognition systems may exhibit bias, leading to inaccuracies in identifying individuals from certain demographic groups.
Legal and Ethical Issues:
The use of facial recognition in law enforcement and surveillance raises legal and ethical questions regarding privacy rights and civil liberties.
Security Risks:
Like any technology, facial recognition programs are vulnerable to hacking and cyber attacks, potentially compromising sensitive data.
Reliability:
Facial recognition systems may not be foolproof and can be affected by factors such as changes in lighting conditions or facial expressions.

Deciphering the Deepfakes Dilemma: A Comprehensive Look into Synthetic Media
Deepfakes represent a convergence of cutting-edge technologies, including artificial intelligence (AI), machine learning, and
Conclusion:
Facial recognition programs have emerged as powerful tools with a wide range of applications across various industries. While they offer numerous benefits in terms of security, convenience, and efficiency, it is essential to address the associated concerns and limitations. By implementing robust security measures, ensuring transparency, and adhering to ethical guidelines, facial recognition technology can be effectively utilized to enhance safety and streamline operations in the digital age.