Cyberattacks don’t always start with the main target. Sometimes, they begin somewhere smaller, like a software vendor, supplier, or third-party service.
That’s the danger of supply chain attacks. These attacks exploit the trust between companies and their partners, allowing hackers to sneak malicious code or access into systems long before anyone notices.
As modern businesses rely on complex networks of providers, one weak link can expose thousands. Understanding how these attacks happen is the first step to stopping them.
In this article, we will look at how third-party attacks work and how to detect and prevent them.
What are Supply Chain Attacks and How Do They Work?
These types of supply chain attacks are also known as third-party attacks. They happen when hackers target a company’s trusted suppliers, vendors, or software providers instead of attacking the company directly. The goal is to slip malware or malicious code into systems that the target company already trusts. Once the infected software or service is used, the attacker gains access to the company’s data, systems, or networks.
These attacks work because most organizations depend on third parties for tools, hardware, or cloud services. A single weak link in that chain can open the door for large-scale breaches. In simple terms, Supply Chain Attacks turn trust into a weapon.
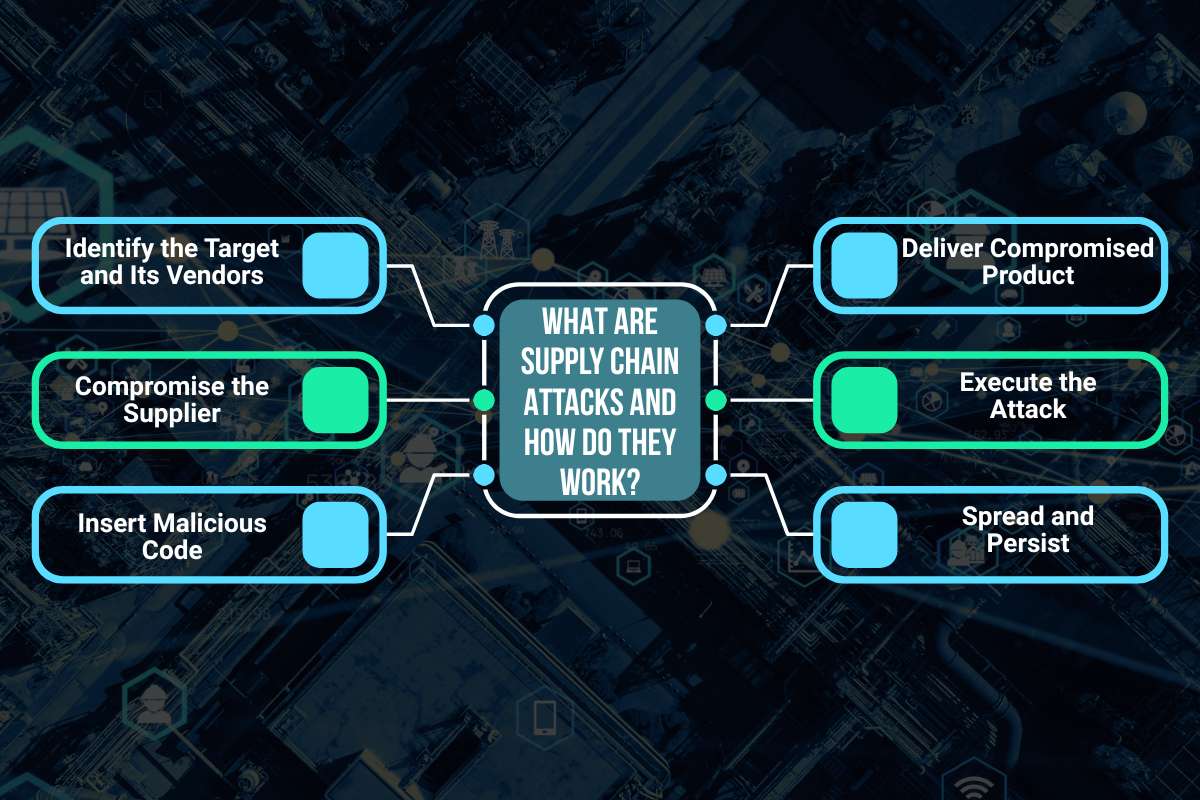
Let’s break down how a Supply Chain Attack works, step by step:
Step 1: Identify the Target and Its Vendors
Attackers start by researching their main target, which is usually a big company, government agency, or tech provider. Then, they look for smaller suppliers or software vendors connected to that target. These vendors often have fewer security measures, making them easier to breach.
Step 2: Compromise the Supplier
Once the attacker identifies a weak supplier, they try to access its systems. They may use phishing emails, stolen credentials, or zero-day vulnerabilities. The aim is to insert malware or modify code without being noticed.
Step 3: Insert Malicious Code
After gaining access, hackers place malicious code inside the vendor’s product, software update, or service. When the product reaches the main target, it carries the infection along. Attackers often hide the payload inside legitimate functions to avoid detection. They may also add checks so the malware only activates in certain environments.
Step 4: Deliver the Compromised Product
The infected product or software update is sent to the target organization. Since the product comes from a trusted vendor, the company installs it without suspicion. Delivery can occur through automatic updates, installers, or pre-installed hardware. Many victims trust the update process and do not scan for hidden changes.
Step 5: Execute the Attack
Once inside the target’s system, the malware activates. It may steal data, monitor activities, or open backdoors for future attacks. The attacker often waits for the best moment to act to blend in with normal traffic. They may create scheduled tasks or stealthy services to keep access long-term.
Step 6: Spread and Persist
Finally, the malware spreads across networks and systems. It can affect partners, clients, and users linked to the same supply chain, creating a ripple effect of compromise. The malware may use stolen credentials to move laterally to high-value systems. It also plants persistence mechanisms, so removing it becomes difficult..
What are the Types of Supply Chain Attacks?

Not all third-party attacks look the same. Hackers use several methods depending on their goal, the target’s defenses, and the type of supply chain they want to exploit.
1. Software Attacks
In this type, attackers target software updates or development tools. They add malicious code to a legitimate update or library. When users download the update, the malware enters their system. The SolarWinds attack in 2020 is a prime example.
2. Hardware Attacks
Here, attackers tamper with physical hardware before it reaches the buyer. This could include chips, USB drives, or servers. Tiny components may be modified to send data back to the attacker once connected to a network.
3. Firmware Attacks
Firmware sits between hardware and software. Attackers modify firmware to control systems at a deep level. These attacks are hard to detect because traditional antivirus software rarely scans firmware.
4. Open-Source Dependency Attacks
Many companies use open-source code in their products. Hackers exploit this by inserting malicious packages or dependencies into public repositories. When developers unknowingly use these, the malware spreads.
5. Third-Party Service Attacks
Sometimes, hackers target third-party service providers, such as cloud hosting companies or IT contractors. By compromising their access, attackers can reach many clients at once.
How do Supply Chain Attacks Impact Businesses?

The impact of a supply chain attacks scan can be devastating. Because they spread through trusted sources, they often affect thousands of users or organizations at the same time. The damage goes far beyond one company’s data breach.
1. Data Theft and Espionage
Hackers can steal customer data, intellectual property, or government information. Stolen data can be sold or used for spying and competitive advantage.
2. Financial Losses
Recovery costs, legal fees, and compensation can drain company resources. Some victims lose millions in ransom payments or suffer from long-term reputational damage.
3. Operational Disruption
Malware can shut down supply chains, delay production, or interrupt vital services. In industries like healthcare or energy, these disruptions can risk lives.
4. Reputational Damage
Customers lose trust when companies fail to protect their data. Once that trust is gone, it’s hard to rebuild.
5. National Security Threats
When Supply Chain Attacks target government agencies or defense contractors, they can put national security at risk. State-sponsored hackers often use this tactic to spy on or sabotage other nations.
Here are 10 Things You Can Do to Prevent and Mitigate Supply Chain Attacks

Preventing third-party attacks requires strong security at every stage of the chain. Since these attacks rely on trust, companies must verify every connection, update, and vendor they use.
Here is how you can minimize the risk of such supply chain attacks:
1. Conduct Vendor Risk Assessments
Regularly check the security posture of all third-party vendors and suppliers. Require them to follow strong cybersecurity standards and verify their compliance.
2. Use Multi-Factor Authentication (MFA)
Adding an extra layer of authentication prevents attackers from using stolen passwords to access systems.
3. Implement Zero Trust Architecture
Zero Trust means “never trust, always verify.” Every user, device, and application must prove its identity before accessing company systems.
4. Monitor Software Integrity
Use code-signing and hash verification to ensure software updates are genuine. Always verify updates from vendors before installation.
5. Limit Access and Permissions
Only give vendors and employees the minimum access they need. This reduces the impact if someone’s credentials are stolen.
6. Maintain Visibility Across the Supply Chain
Track all digital assets, devices, and connections in the supply chain. Continuous monitoring helps detect unusual activities faster.
7. Use Threat Intelligence
Subscribe to threat intelligence feeds to stay updated about new vulnerabilities or attacks on specific vendors.
8. Train Employees and Developers
Human error often opens the door for Supply Chain Attacks. Regular cybersecurity training helps employees spot phishing and suspicious behavior.
9. Conduct Regular Security Audits
Test your systems and vendors for vulnerabilities. Penetration testing helps uncover weak points before attackers find them.
10. Have an Incident Response Plan
Prepare a detailed plan for responding to a breach. Quick detection and containment reduce damage and recovery time.
Cybersecurity education plays a major role in defending against Supply Chain Attacks. When IT professionals and employees understand how these attacks work, they can react faster and smarter. Building awareness at every level of an organization strengthens the digital defense chain.
Real-World Case Studies of Supply Chain Attacks
1. The SolarWinds Attack (2020)
One of the most famous third-party attacks happened in 2020, when hackers breached SolarWinds, a U.S. software company. Attackers inserted malicious code into the company’s Orion software updates. When thousands of clients, including U.S. government agencies, installed the updates, they unknowingly gave hackers access to sensitive systems. The attack went undetected for months and affected over 18,000 customers worldwide. It showed how one compromised vendor could harm entire industries.
2. The MOVEit Transfer Breach (2023)
In 2023, attackers exploited a zero-day flaw in MOVEit Transfer, a popular file-sharing tool. The Cl0p ransomware group used it to steal data from hundreds of companies and government agencies. Many organizations were affected because they used MOVEit through third-party providers, again proving how Supply Chain Attacks can spread widely.
Conclusion:
Supply chain attacks remind us that cybersecurity is about protecting every connection tied to your network. A single breach in a vendor’s system can ripple across industries, exposing data and disrupting operations worldwide.
Building stronger digital defenses requires constant vigilance, strict security audits, and collaboration between all parties in the chain. When businesses invest in awareness and secure partnerships, they protect themselves as well as strengthen the entire digital ecosystem.
FAQs
1. What industries are most affected by supply chain attacks?
Sectors like finance, healthcare, government, and technology face the highest risk due to their reliance on external vendors and cloud-based infrastructure.
2. Why are these attacks difficult to detect?
Because the attack originates from a trusted source, it often bypasses traditional security checks and remains hidden until significant damage is done.
3. How can companies prevent third-party attacks?
Businesses can reduce risks by vetting vendors, using endpoint monitoring tools, enforcing zero-trust policies, and requiring regular security audits.