Let’s say you’re running a business, and one day someone quietly sneaks into your network without you knowing. They steal data, damage systems, or spy on your digital activity. Scary, right? What could you have done to stop the theft? You could have used an Intrusion Detection System (IDS). It’s like a vigilant security guard for your network.
An Intrusion Detection System constantly monitors incoming and outgoing traffic, spots suspicious behavior, and alerts you before threats cause real harm. Whether you’re protecting a small website or an entire enterprise system, intrusion detection is now a critical part of digital defense in a world full of evolving cyber threats.
What Is an Intrusion Detection System?
Intrusion Detection System is a tool that monitors network and system activity to detect suspicious or harmful events. It watches traffic and logs for unusual behavior and sends alerts when it spots known attack patterns or abnormal movements.
Modern Intrusion Detection System tools analyze massive amounts of data in real time and support security teams by offering detailed insight into possible breaches. While it doesn’t actively block attacks on its own, it increases your response speed and helps locate hidden threats. It works with other security tools to create a layered defense strategy.
How Does an Intrusion Detection System Work?
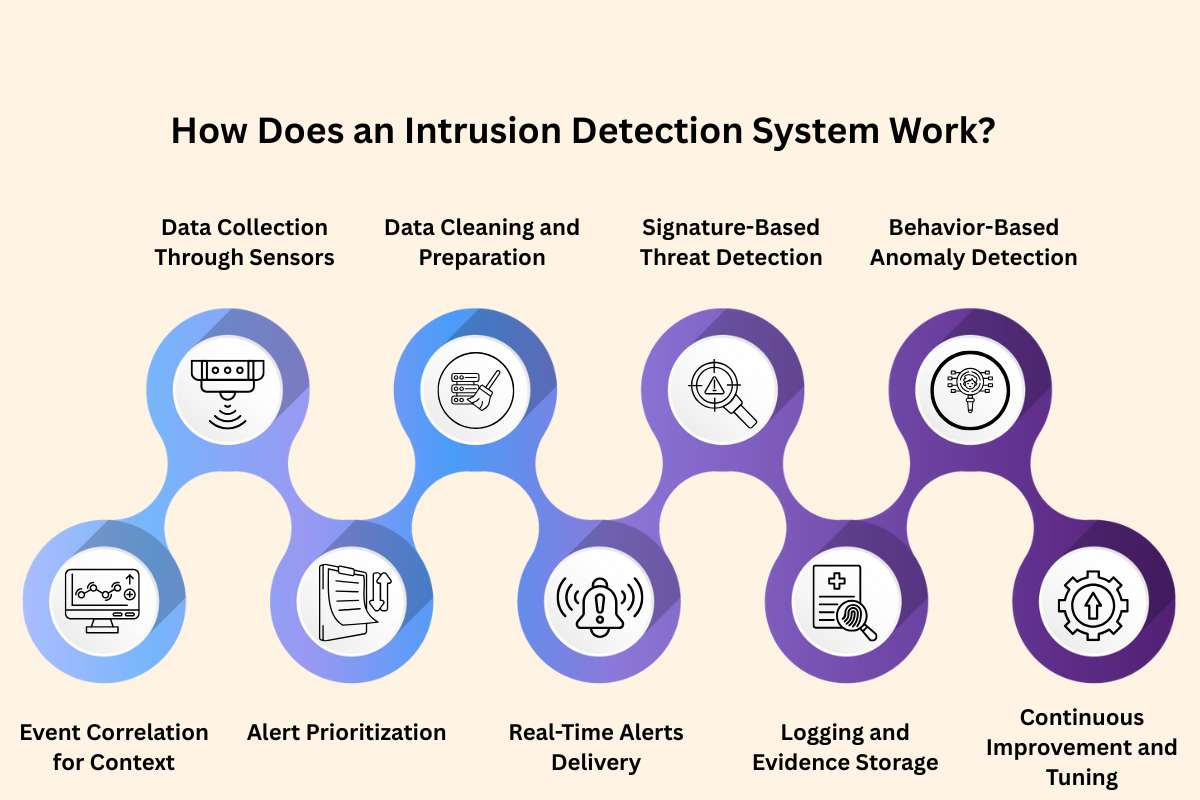
1. Data Collection Through Sensors:
Sensors collect data from devices, networks, or logs. These sensors sit on key network points or systems and watch all incoming and outgoing activity. They collect data such as packets, login logs, and file changes. This raw data forms the starting point for intrusion detection.
2. Data Cleaning and Preparation:
The system organizes and prepares this data for analysis. It cleans the data, removes extra noise, and formats it in a usable way. This step helps the IDS focus on what matters, like suspicious patterns. Proper structuring speeds detection and reduces errors
3. Signature-Based Threat Detection:
It compares the processed data to known threat patterns. These patterns, or signatures, are saved from past attacks and security research. If activity matches one of these signatures, the IDS flags it as a known threat. This quickly stops old and common attacks.
4. Behavior-Based Anomaly Detection:
It checks for behavior that doesn’t match normal activity. The IDS learns what normal behavior looks like in your network. If traffic or user actions seem strange or out of place, the system alerts your team. This helps catch new or unusual attacks that don’t match old patterns.
5. Event Correlation for Context:
It correlates events from different sources for context. A single failed login may not be harmful. But if it’s followed by file changes and new network connections, it means danger. Correlation helps avoid false alarms and reveals bigger attack stories.
6. Alert Prioritization:
It assigns importance levels to help teams prioritize. Not all alerts are equal. Some may show minor issues, while others reveal serious breaches. The IDS ranks each alert to help teams act quickly.
7. Real-Time Alerts Delivery:
It sends alerts to security dashboards or tools like SIEM. Alerts appear in real time through dashboards, emails, or integrations. Teams can act right away to stop or study the threat. Clear signals help reduce damage.
8. Logging and Evidence Storage:
Logs and related data are stored for later investigation. Every alert and event comes with records like log files and packet captures. These details help teams study how attacks work and support legal actions or audits.
9. Continuous Improvement and Tuning:
Security teams adjust rules and train the system further. Analysts review alerts and mark them as true attacks or mistakes. The IDS learns from this feedback and improves over time. Regular tuning keeps the system sharp and reduces false alarms.
Why is an Intrusion Detection System Important?

An Intrusion Detection System helps you detect cyber threats before they cause serious damage. It finds attacks that firewall tools may miss, giving you an extra layer of security. The system provides deep visibility into network and host activity and helps preserve important evidence for investigations and legal steps. These logs support cybersecurity audits and compliance processes and help prove due diligence in case of breaches. Customers and partners feel safer when they know an Intrusion Detection System is watching over their sensitive data.
How is Intrusion Detection System Classified into Different Types?
Intrusion Detection Systems fall into different types based on where they run and how they detect attacks. Each type offers strengths and weaknesses, and many organizations use more than one.
1. Network-Based IDS (NIDS):
A Network-Based IDS checks all traffic moving through a part of your network. It spots attacks trying to reach many devices at once and monitors for patterns like port scanning or excessive connections. A NIDS sits near important network equipment like routers or gateways. It works best when you also monitor encrypted traffic with decryption policies. It offers a wide view but needs strong processing power for busy networks.
2. Host-Based IDS (HIDS):
A Host-Based IDS runs directly on computers or servers in your network. It watches system logs, files, and user activity and spots things like unauthorized file changes or odd command behavior. HIDS is useful for sensitive systems like databases or financial servers. It can detect insider threats that bypass the network entirely. However, it may fail if malware disables the IDS software, so it needs extra protection.
3. Signature-Based IDS:
A Signature-Based IDS compares network or host data to known attack patterns. It works well against common threats and rarely sends false alerts if updated. The downside is that it may miss new or changed attacks that don’t match a saved pattern. It requires regular updates and strong threat intelligence to stay effective.
4. Anomaly-Based IDS:
An Anomaly-Based IDS learns what normal behavior looks like in your network. It flags activity if it breaks that pattern or falls outside expected limits. These systems can detect new attack types, even if no one has seen them before. The trade-off is that it may classify harmless changes as threats, especially early on. Teams must tune the IDS and review alerts to keep false positives low.
What are the Advantages and Disadvantages of IDS?

Like any cybersecurity tool, an Intrusion Detection System has strengths and limitations. Understanding both helps you decide where it fits within your security strategy.
Advantages:
1. Early threat detection:
An Intrusion Detection System alerts your team quickly when it sees abnormal behavior or active attacks. This allows rapid response and limits damage.
2. Better visibility:
IDS tools show what’s happening on your network and systems in real time. They help find blind spots, tradecraft, and hidden threats that other tools may miss.
3. Supports investigations:
IDS collects key data such as logs and packet captures. This helps during forensic analysis and legal reporting after an incident.
4. Compliance support:
Many industries require monitoring and logging for audits. An IDS helps you meet these standards, especially in finance and healthcare.
5. Layered defense:
IDS works beside firewalls, antivirus tools, and SIEM systems. Together, they create a stronger defense through detection and response.
Disadvantages:
1. False positives:
Some IDS tools flag harmless behavior as a threat, especially when not well-tuned. This wastes time and causes alert fatigue.
2. High resource usage:
To analyze data quickly, an IDS needs processing power and storage. Busy networks may need dedicated hardware.
3. Not a blocker:
Most IDS only detect and alert. They do not block attacks unless paired with an Intrusion Prevention System or firewall rules.
4. Needs expert management:
IDS systems require tuning, rule updates, and human judgment. Without skilled staff, detection quality can drop.
5. Evasion risk:
Advanced threats may disguise activity or move slowly to avoid triggering signatures. Attackers study IDS behavior to slip past it.
Different Types of Intrusion Attacks
1. Denial of Service (DoS) and Distributed DoS (DDoS):
A DoS attack floods a system with fake traffic to slow it down or crash it. A DDoS attack does this from many devices at once, making it harder to stop. An Intrusion Detection System detects sudden traffic spikes or repeated requests to the same service. It sends alerts before the system becomes unusable. Teams can then block the fake traffic and keep services online.
2. Spoofing Attacks:
Spoofing means pretending to be another source online to gain access. Attackers fake an IP address, email address, or identity token. An IDS inspects data and spots mismatched information or strange access paths. It checks if the source and behavior match real users or systems. This helps stop attackers from breaking in under false identities.
3. Brute Force and Credential Stuffing:
A brute force attack tries many passwords until one works. Credential stuffing uses stolen passwords from other breaches to enter accounts. An IDS watches for repeated failed logins, odd patterns, or access from new locations. It alerts teams to lock accounts and improve access control methods like MFA. This prevents attackers from guessing their way in.
4. Malware Delivery and Fileless Malware:
Malware arrives through emails, downloads, or infected websites. Fileless malware runs directly in memory, leaving no trace on disk. Host-based IDS tools spot strange programs or hidden file changes. Network IDS tools detect malicious traffic going in or out. Early detection helps stop the spread and reduce harm.
5. SQL Injection and Cross-Site Scripting (XSS):
SQL injection tricks a website into running bad commands in its database. XSS puts harmful scripts into user-facing pages. An IDS watches for strange patterns in URLs, script tags, and form input. It alerts developers and security teams to block harmful payloads and patch systems. This protects data and keeps users safe.
6. Man-in-the-Middle (MITM):
MITM attacks happen when a hacker intercepts or changes data moving between two systems. This might occur on unsafe public Wi-Fi or unsecured channels. An IDS spots unexpected routing changes or untrusted certificates. It alerts teams to switch users to safe channels like encrypted connections. Fast action stops private data from being stolen.
7. Insider Threats:
Insider threats come from users within your network. These may be employees, contractors, or partners misusing their access. A host-based IDS watches for odd file changes, movement, or access levels. It spots unusual behavior even if it looks normal on the surface. This helps teams act before data is stolen or damaged.
Also Read: What is Social Engineering? Here’s Everything You Need to Know to Protect Yourself
Case Study: Real-World SCADA Power Grid IDS
In a real‑world demonstration, researchers at Twente University deployed a process‑aware Intrusion Detection System across two live SCADA environments in the electricity grid: one medium‑voltage substation and one rural low‑voltage feeder.
The IDS used models of the physical grid processes (like sensor behavior and power flow) rather than relying solely on network signatures, and it successfully detected attacks such as false‑data injection and man‑in‑the‑middle manipulations.
By tailoring its thresholds to real operational data, the system struck a balance between alerting on actual risks and minimizing false positives. This case study shows how an IDS built for smart grid infrastructure can protect critical energy systems in practice, not just in simulation.
Conclusion:
Businesses need stronger and stronger systems to keep up with the advanced cyber threats. An Intrusion Detection System offers a powerful way to spot and stop threats before they cause damage. By constantly monitoring your network for unusual activity, an Intrusion Detection System gives you peace of mind and better control over your security.
Whether it’s detecting unauthorized access or alerting you to harmful patterns, intrusion detection has become an important part of a strong cybersecurity system.
FAQs
1. Does an Intrusion Detection System stop attacks?
No, most IDS tools only detect and alert. However, Intrusion Prevention Systems (IPS) can prevent attacks by blocking harmful traffic in real-time.
2. Who needs an Intrusion Detection System?
Any individual or organization that wants to protect sensitive data and maintain secure network operations should consider using an IDS, especially if they face cyber threats or handle user information.
3. How is an Intrusion Detection System different from a firewall?
A firewall blocks unauthorized access based on rules, while an Intrusion Detection System detects and alerts about suspicious or malicious activity that may bypass the firewall.






