If you’ve ever watched a production line slow down without warning or seen strange fluctuations in a control panel, you know how fragile an industrial setup can feel. Even small disruptions can bring entire operations to a halt, and the threat of hidden tampering only adds to that pressure. In environments where every second counts, uncertainty becomes a real risk.
Industrial control systems (ICS) bring structure and clarity to that complexity. It watches each process, tracks every signal, and keeps operations steady from the inside out. When something unusual occurs, it helps you spot the issue before it grows. With the right system in place, you gain a stronger sense of control and a smoother, safer flow across your entire operation.
What are ICS and How do They Work?
An Industrial Control Systems (ICS) helps industries monitor and control physical processes. It reads data from sensors, processes that data inside controllers, and sends commands to machines so as to adjust to any problems.
How do Industrial Control Systems Work?

Step 1: Sensors collect real-world data
Sensors measure temperature, flow, pressure, speed, or other conditions. They send this information to controllers. These values help the system understand what is happening inside a plant or machine.
Step 2: Controllers process the sensor data
Controllers, such as PLCs, read incoming data and compare it with set rules. They decide what needs to happen next. A controller may also alert human operators if it sees unusual values. Industrial Control Systems often run beside these controllers to monitor unsafe behavior on the network.
Step 3: The system sends commands to actuators
Actuators follow the controller’s instructions. They open valves, switch motors, adjust speeds, or turn pumps on and off. These actions keep the process stable and safe.
Step 4: Human operators monitor the system
Workers use screens or HMIs to track everything in real time. They can change settings, stop machines, or override commands.
Industrial Control Systems is designed for industries that rely on machines and constant process control. Power plants, water treatment units, factories, chemical plants, refineries, and large manufacturing sites use ICS to keep operations steady, safe, and efficient.
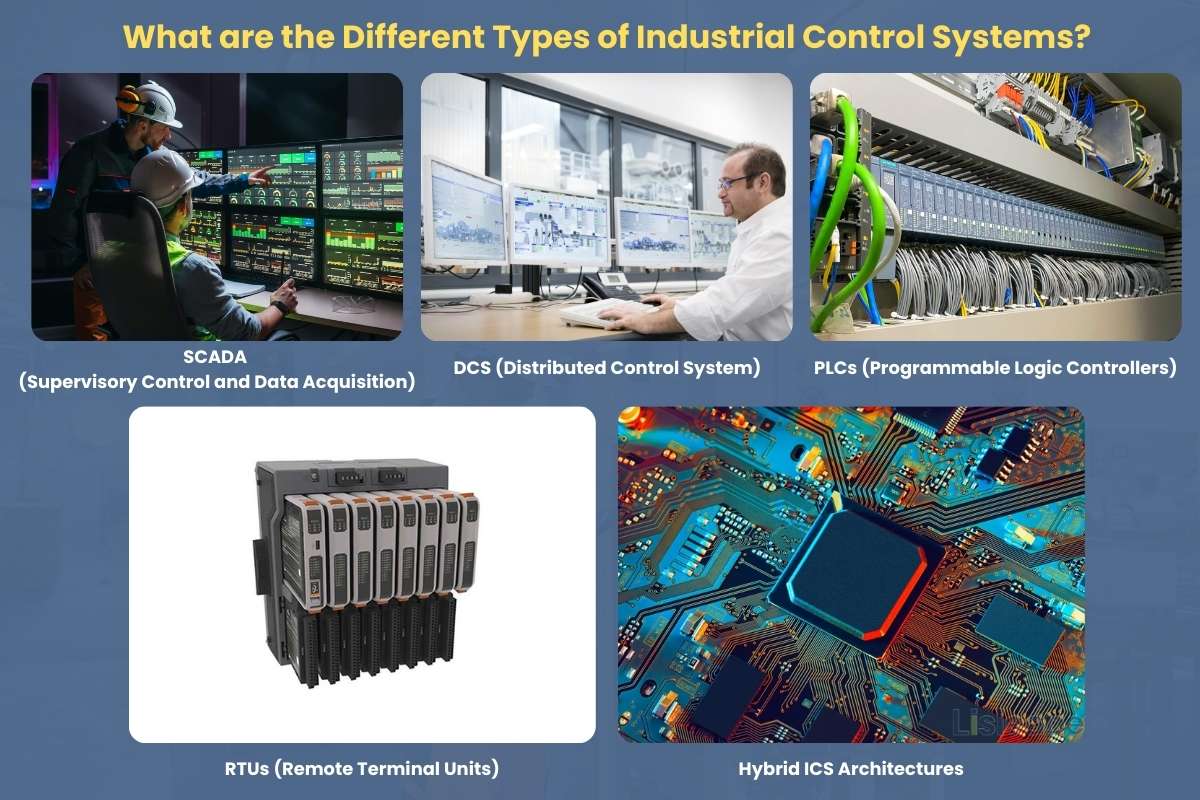
What are the Different Types of Industrial Control Systems?
Industrial sites depend on many moving parts. Systems must run without long breaks, and teams must manage older machines. These limits create real challenges when they try to improve security.
1. SCADA (Supervisory Control and Data Acquisition):
SCADA systems manage large or spread-out operations such as pipelines or electrical grids. They gather data from many remote locations and send it to a central hub. Operators use this hub to control equipment across wide areas. Many SCADA workers use Industrial Control Systems, as remote links can be an easy target for attackers
2. DCS (Distributed Control System):
A DCS works inside a single plant or industrial site. It spreads tasks across many controllers that handle small sections of a larger process. This design reduces the load on one central controller. It also improves reliability.
3. PLCs (Programmable Logic Controllers):
PLCs run automation tasks for machines. They follow instructions based on sensor data, and they make fast decisions. PLCs are common in factories that need quick responses. Teams often monitor PLC networks using industrial control systems to stop unauthorized commands.
4. RTUs (Remote Terminal Units):
RTUs collect data in remote locations and send it to a central SCADA or control center. They are used in water pipelines, energy distribution, and rail systems. Because RTUs operate far from staff, an ICS helps detect strange commands or failed access attempts.
5. Hybrid ICS Architectures:
Some facilities mix SCADA, DCS, PLCs, and RTUs to fit their needs. These setups may be complex but offer flexibility. A hybrid system benefits greatly from an intrusion ICS since data moves across many devices and zones.
What are the Different Threats that Affect Industrial Control Systems?

Many companies want better control and safety. But they also fear downtime, slow upgrades, and strong resistance from older equipment. These issues shape how they plan their Industrial Control Systems.
1. Malware and Ransomware:
Malware can enter ICS networks through infected USB drives, unsafe emails, or weak passwords. Once inside, it can lock systems, erase data, or change machine behavior. Ransomware may stop production until a payment is made.
2. Insider Threats:
Employees or contractors may misuse their access. Some do it by accident, while others may do it on purpose. Because insiders already have valid credentials, attacks may stay hidden for a long time.
3. Weak Industrial Protocols:
Older ICS protocols were never designed with security in mind. They lack encryption and authentication. Attackers can intercept or alter messages as they travel between devices. When protocols are weak, even small gaps allow unauthorized commands to slip through.
4. Phishing and Credential Theft:
Workers may receive fake emails that ask them to log in or share passwords. Attackers then use stolen accounts to enter ICS networks. This attack style is common because ICS staff often work long shifts and face many alerts.
5. Network Disruption and DoS Attacks:
Attackers may flood a controller or network with fake traffic. This slows or blocks real commands. In ICS, even a short delay can harm machines or create unsafe conditions.
6. Supply-Chain Attacks:
Hackers may target the vendors that supply software or hardware updates. They insert harmful code into updates, which later reach ICS equipment. This bypasses normal security checks. These supply chain attacks are hard to spot without deep network monitoring.
Challenges in Implementing Industrial Control Systems

Industrial sites depend on many moving parts. Systems must run without long breaks, and teams must manage older machines. These limits create real challenges when they try to improve security.
1. Legacy Hardware and Software:
Many plants rely on old equipment that cannot handle modern security features. Updating these systems risks stopping production. Because uptime matters, companies avoid upgrades, which leaves systems exposed.
2. Balancing Uptime and Security:
Industrial sites run every hour of the day. Shutting down systems for maintenance or patches affects output. Teams must choose between safety and production schedules. This creates delays in applying important security fixes.
3. Lack of Skilled Professionals:
ICS requires both engineering and cybersecurity knowledge. Many teams understand machinery but not digital threats. Training takes time, and hiring experts can be expensive. This gap makes the network more vulnerable to attacks.
4. Weak Network Segmentation:
Some facilities still mix IT and OT networks. If attackers break into the office network, they can move into ICS systems easily. A well-planned design should separate networks and use an intrusion detection system to monitor movement between zones.
5. Unsecured Protocols and Devices:
Many devices do not support encryption or modern security. Communication flows openly across the network. Attackers can watch or change messages. Fixing this often requires replacing hardware, which costs time and money.
Case Study: The Stuxnet Attack that Affected ICS
Stuxnet Attack:
Stuxnet is one of the most well-known Industrial Control Systems attacks in history. It targeted PLCs that controlled nuclear centrifuges used for uranium enrichment. The malware entered the network through infected USB drives and stayed hidden for a long time. Once active, it changed the speed of the centrifuges in short bursts. This caused physical stress and damage while the monitoring screens showed normal values. The most dangerous part was how Stuxnet tricked both operators and machines. It created fake sensor readings and delayed alarms. This made detection extremely hard without industrial control systems watching deeper network patterns. The attack proved that malware can damage real-world equipment, not just digital systems.
Future Outlook of ICS
Research done by Coherent Market Insights predicts the ICS market will grow at a 7.55% CAGR from 2023 to 2030. As industries expand automation, the need for security will rise. Most facilities will rely more on AI-based monitoring, built-in device security, and wide deployment of intrusion detection system technology. Growth in IoT and IIoT devices will also increase network traffic and create more entry points for attackers. Companies will need stronger controls, smarter monitoring, and better-trained staff to protect Industrial Control Systems networks.
Conclusion:
Keeping large operations running smoothly is never simple, and small issues can quickly grow when you cannot see what is happening behind the scenes. Industrial control systems give you the visibility, stability, and confidence needed to manage complex processes with fewer surprises.
These systems help you respond faster, reduce downtime, and maintain consistent performance across every stage of production. When you understand how they work and where they fit, you can build stronger, safer, and more reliable operations for the long run.
FAQs
1. Are industrial control systems expensive to maintain?
Costs vary by size and complexity, but good maintenance often saves money by preventing downtime and reducing major failures.
2. What is the difference between SCADA and DCS?
SCADA oversees wide, spread-out operations, while DCS manages processes within a single location or facility.
3. How do industrial control systems improve safety?
They track real-time data, flag abnormal activity, and help operators react quickly before a small issue becomes a safety threat.






