Did you know that data breaches cost companies $4.88 million on average in 2024? Is this higher than 10% from last year? They hit a record high. With over 8,000 attacks worldwide.
Data breach prevention means stopping hackers from stealing sensitive information. Such as passwords and bank details. It’s vital now for businesses and people everywhere to protect privacy and avoid huge losses.
In this guide, you’ll learn how breaches happen. Along with proven ways to stop them. And easy tips you can use today.
Why Data Breach Prevention Matters?
Data breach prevention saves businesses from big trouble. A breach causes huge money losses, like millions in fixes. Companies face fines from rules like GDPR in Europe or India’s DPDP Act. These laws demand quick alerts about stolen data. Bad news hurts a brand’s name and scares away customers who lose trust.
Worldwide, rules protect data, from the US to Asia. For people, breaches lead to identity theft. Hackers steal your info for fake accounts or loans. This breaks privacy and causes stress for years.
Data breach prevention keeps everyone safe: money, trust, and peace of mind.
How Does a Data Breach Happen?
A data breach is a security incident. This is where sensitive, protected, or confidential data is compromised. It is either copied, transmitted, viewed, or stolen by an individual unauthorized to do so. It compromises the confidentiality of information. It can range from personal health records to corporate trade secrets.
Breaches rarely occur through a single “glitch.” Instead, they follow a deliberate lifecycle:
- Phishing: Tricking employees into revealing credentials via deceptive emails.
- Credential Stuffing: Using lists of leaked passwords. From one site to “stuff” into another.
- Malware: Deploying software like ransomware to exfiltrate data before encrypting it.
- Insider Misuse: A disgruntled or negligent employee abusing their legitimate access.
Real-World Mechanics
Consider a supply chain attack (like the 2024–2025 service desk compromises). Attackers didn’t target the main company first; they breached a third-party vendor’s support system, reset admin passwords, and walked through the “front door” of the target enterprise. This grounded approach shows that data breach prevention must extend beyond your own walls to your entire vendor network, as a breach is often a chain of small human errors leading to a massive digital heist.
Here are Some of the Common Causes of Data Breaches:
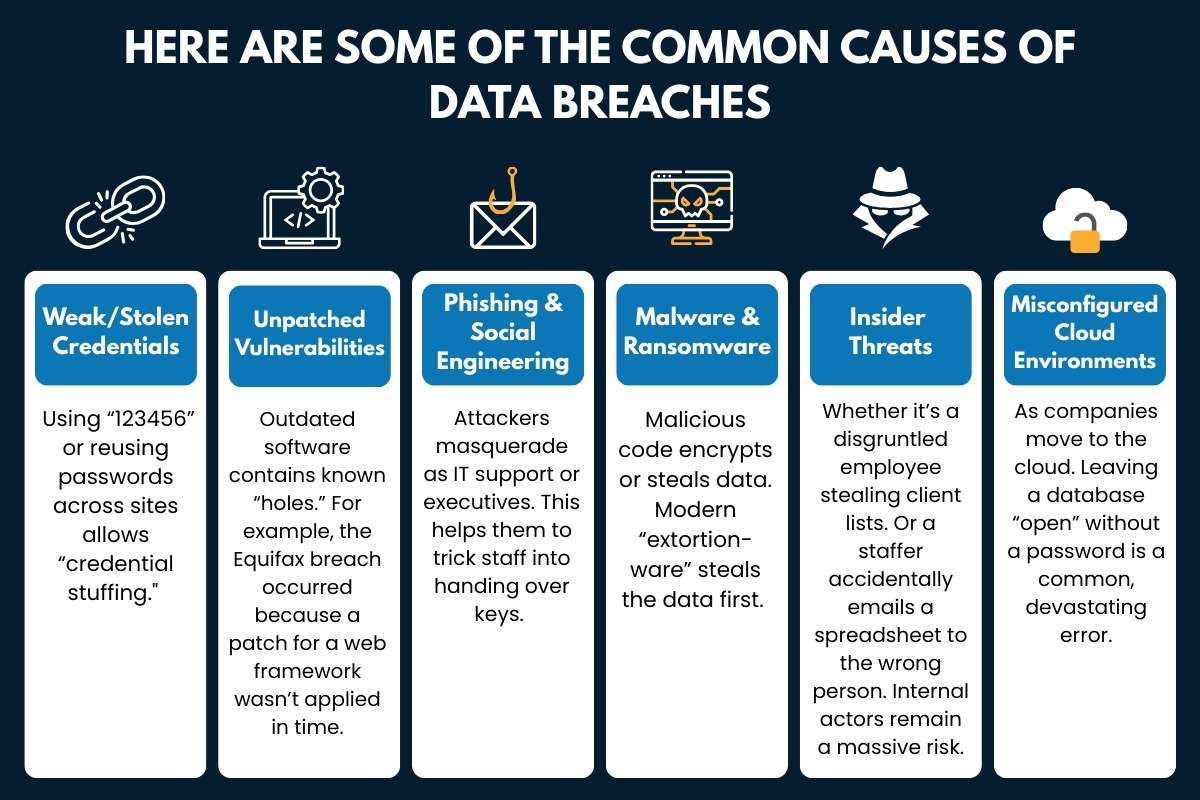
A data breach is the unauthorized access or exfiltration of sensitive information. Hollywood portrays “hacking” as complex code-breaking. Most breaches stem from preventable structural or human failures.
Primary Breach Vectors
- Weak/Stolen Credentials: Using “123456” or reusing passwords across sites allows “credential stuffing.” Where attackers use one leak to unlock dozens of other accounts.
- Unpatched Vulnerabilities: Outdated software contains known “holes.” For example, the Equifax breach occurred because a patch for a web framework wasn’t applied in time.
- Phishing & Social Engineering: Attackers masquerade as IT support or executives. This helps them to trick staff into handing over keys. This exploits human trust rather than digital firewalls.
- Malware & Ransomware: Malicious code encrypts or steals data. Modern “extortion-ware” steals the data first. Then threatening public release if payment isn’t made.
- Insider Threats: Whether it’s a disgruntled employee stealing client lists. Or a staffer accidentally emails a spreadsheet to the wrong person. Internal actors remain a massive risk.
- Misconfigured Cloud Environments: As companies move to the cloud. Leaving a database “open” without a password is a common, devastating error.
These are the Top 8 Strategies for Data Breach Prevention:

To prevent data breaches, organizations must move beyond “set and forget” security. This playbook outlines a multi-layered defense strategy. It is designed to protect assets in a borderless digital world.
1. Know Your Data
You cannot protect what you can’t see. Conduct a comprehensive inventory to classify data based on sensitivity. E.g., PII, Intellectual Property. This allows you to apply the strictest controls only where they are most needed. Optimizing resource allocation.
2. Strong Access Controls & MFA
Implement Least Privilege. Users should only access the data required for their specific role. Mandatory Multi-Factor Authentication (MFA) is the single most effective deterrent against credential-based attacks.
3. Patch & Update Religiously
Automate patch management to close security holes in software. Attackers often exploit vulnerabilities within days of a public disclosure. A systematic update cycle minimizes this window of opportunity.
4. Encryption Everywhere
Encrypt data at rest (on servers/disks) and in transit (moving across networks). Using industry standards like AES-256. If a breach occurs, encryption ensures the stolen data is unreadable and useless to the thief.
5. Defense-in-Depth & Segmentation
Implementing data breach prevention through a defense-in-depth approach is critical. Use firewalls and micro segmentation to divide your network into isolated zones. This prevents “lateral movement.” It ensures that if one workstation is compromised. The attacker cannot easily jump to the core database.
6. Monitoring & Detection
Deploy SIEM (Security Information and Event Management) tools to analyze logs in real-time. Anomaly detection can flag a login from an unusual country. Or a massive data export before the damage is done.
7. Audits & Pentesting
Regularly “attack” your own systems via Penetration Testing. Third-party audits provide an unbiased view of your security posture. They also uncover hidden configuration errors.
8. Incident Response (IR) Planning
Assume a breach will happen. Maintain a living IR plan and conduct tabletop exercises. So that IT, Legal, and PR teams know exactly how to contain a threat. And notify affected parties without panic.
Also Read: Effective Cyber Security Technology Solutions for Modern Challenges
Practical Tips for Data Breach Prevention:

Securing your digital environment doesn’t require an enterprise budget. It starts with fundamental habits that neutralize the most common attack vectors.
- Password Hygiene: Deploy a password manager (e.g., Bitwarden or 1Password). This helps to generate and store unique, high-entropy passwords. This eliminates the “domino effect” where one leaked credential compromises every linked account.
- Continuous Training: Move beyond annual slides. Conduct monthly phishing simulations to sharpen employee “threat intuition.” Turning your staff into a human firewall.
- Secure Remote Work: Mandate encrypted VPNs. Along with Endpoint Detection and Response (EDR) for all off-site hardware. This ensures that home-office vulnerabilities don’t bypass corporate perimeters.
- Immutable Backups: Use the 3-2-1 rule: three copies of data, on two different media. With one copy off-site or in an “immutable” cloud bucket that ransomware cannot modify.
- Vendor Vetting: Audit third-party access regularly. Ensure partners adhere to your security standards through formal Service Level Agreements (SLAs).
Conclusion:
Take action now to stay safe in the modern digital world. Anyone can experience a data breach, but you can prevent them. Start with small steps. Such as enabling additional login security or utilizing a password manager. Your personal information is protected by these easy habits.
The best defense for businesses is to remain vigilant. Update your software and teach your staff how to recognize phony emails. Recall that effective security requires more than just sophisticated equipment. It is about exercising caution daily. You can safeguard your finances, reputation, and peace of mind by adhering to this guide. Start your data breach prevention strategy now. Rather than waiting for an attack to occur!
Also Read: CyberSecurity Awareness Training: Defend, Detect, Prevent
FAQ:
1. What role do employees play in data breach prevention?
Employees are a critical line of defense. Proper training helps them recognize phishing emails. Also, avoid unsafe links, follow password best practices, and handle data responsibly. Organizations with regular security awareness programs experience significantly fewer successful breaches.
2. How effective is multi-factor authentication (MFA) in preventing data breaches?
Multi-factor authentication is one of the most effective security measures. By requiring an additional verification step beyond a password. MFA significantly reduces the risk of unauthorized access. Even if login credentials are compromised.
3. What is the difference between data breach prevention and data breach response?
Data breach prevention focuses on stopping attacks. Before they happen, through security controls and proactive measures. Data breach response involves actions taken after a breach occurs. Such as containment, investigation, and notification. A strong cybersecurity strategy requires both.






