Data is often called the new oil of the modern age. It is the fuel behind every innovation and invention. However, just as oil spills can devastate the environment, breaches in digital security—cyber incidents—can destroy businesses and personal lives. We navigate a digital sea jam-packed with both opportunity and hidden threats. Being passive onlookers in this environment isn’t enough for cyber safety. It is time we must equip ourselves with the foresight of a seasoned mariner to steer clear of disaster.
As Cyber Awareness Month draws to a close, it’s crucial to solidify the lessons learned. The awareness of how these incidents happen can turn caution into action. This knowledge acts as an offensive advantage. It is for empowering us to make proactive, smarter decisions that build resilience. It’s the essential compass guiding us through the treacherous waters of cyber incidents.
How Are Cyber Incidents Classified and Why Do They Matter?
The National Cyber Security Center of the UK has categorized cyberattack incidents into six categories.
Here’s the categorization:
| Category | Definition | Responders | Actions |
|---|---|---|---|
| 1 National cyber emergency | A major cyber-attack disrupting essential services or national security, causing severe consequences. | COBR, NCSC, law enforcement | Advise the victim, coordinate with the government, and guide incident response. |
| 2 Highly significant | Serious impact on government, essential services, population, or economy. | NCSC (escalate to COBR if needed), law enforcement | Advise the victim, organize engagement, and support government interactions. |
| 3 Significant | Serious impact on large organizations or risk to government/essential services. | NCSC, law enforcement | Advise the victim, organize engagement, and provide technical guidance. |
| 4 Substantial | Impact on medium organizations or risk to larger organizations/government. | NCSC or law enforcement | Advise the victim, support response, and hold engagement meetings if needed. |
| 5 Moderate | Small organization attack, risk to medium organizations, or preliminary signs against large entities. | Law enforcement, NCA input as needed | Advise the victim, follow-up support if required. |
| 6 Localized | Individual or small/medium organization attack. | Local police, NCA input as needed | Advise the victim. |
Source: https://www.ncsc.gov.uk/information/categorising-uk-cyber-incidents
A report by the Organization for Security and Co-operation in Europe (OSCE) outlines the main incidents of cyberattacks. They categorize cyber incidents into the following categories:
1. Malicious Code:
Incidents involving viruses, worms, Trojans, ransomware, spyware, and other types of malware. These are designed to disrupt, damage, or gain unauthorized access to systems.
2. Intrusion and Unauthorized Access:
Attempts or successful breaches of systems, networks, or accounts by attackers. The goal is to gain unauthorized control or information.
3. Denial of Service (DoS) / Distributed Denial of Service (DDoS):
Attacks aimed at overwhelming systems or networks. These attacks are designed to make services unavailable to legitimate users.
4. Information Content Security:
Incidents affecting the confidentiality, integrity, or availability of data. This includes data breaches, leaks, or unauthorized data modification.
5. Fraud and Identity Theft:
Cyber incidents involving deception for financial or personal gain. It can include attacks such as phishing, social engineering, or identity theft.
6. Vulnerabilities and Exploits:
Discovery or exploitation of weaknesses in software or hardware that could be used for attack or unauthorized access.
7. Cyber Espionage and Cyber Warfare:
Incidents involving state-sponsored actors. These are targeting national security interests, critical infrastructure, or political entities.
8. Operational Technology (OT) / Industrial Control Systems (ICS) Attacks:
Incidents targeting critical infrastructure sectors that rely on operational technology. These are designed to attack infrastructure such as energy, water, and transportation.
9. Supply Chain Attacks:
Cyber attack incidents involving the compromise of suppliers or third-party vendors to infiltrate target organizations indirectly.
10. Insider Threats:
Incidents caused by trusted individuals within an organization who misuse their access or privileges.
Five Times Cyber Incidents Proved Awareness Isn’t Optional
Here are some major cyber-attack incidents in modern history. These incidents show how vulnerable we are, and they remind us to be aware of these attacks. Staying alert is better than being alerted.
Here are some of the major cyber incidents:
1. Yahoo Data Breaches (2013-2014):

This was the largest known data breach in modern history. From 2013 to 2014, Yahoo experienced two major data breaches affecting all 3 billion user accounts. Hackers stole names, emails, phone numbers, birthdates, and passwords. Yahoo’s delayed disclosure until 2016 led to a $350 million reduction in its sale price to Verizon.
Why it happened:
Nation-state actors exploited weak security practices and poor credential management for years, allowing theft of billions of user accounts.
How it could be avoided:
Enforce multi-factor authentication, regularly patch systems, and securely store passwords (e.g., using strong encryption and hashing).
2. Operation Shady RAT (2006-2011):
Operation Shady RAT was a massive, five-year campaign that took place between 2006 and 2011. This attack targeted over 70 organizations across the globe. It attacked governments, defense contractors, and the UN, resulting in the theft of valuable intellectual property and government secrets. The sophisticated attacks. It was widely attributed to a state actor in China.
Why it happened:
Targeted organizations had poor perimeter security and inadequate logging/monitoring to detect the persistent, low-and-slow breaches.
How it could be avoided:
Implement Multi-Factor Authentication (MFA) and robust network traffic logging (SIEM) to detect anomalous activity and prevent initial access/lateral movement.
3. Stuxnet (2010):
Stuxnet was a highly sophisticated computer worm discovered in 2010. It was designed to specifically sabotage Iran’s nuclear program by causing physical damage to centrifuges through infecting Siemens industrial control systems (SCADA). It’s considered a landmark example of cyber-weaponry.
Why it happened:
The air-gapped network was compromised by an infected USB flash drive or a contractor’s laptop, and the Siemens PLC software was unpatched and trusting.
How it could be avoided:
Strictly enforce physical security (no unauthorized external media/devices) and implement network segmentation with strong authentication/validation checks.
4. SolarWinds Supply Chain Attack (2020):

The 2020 SolarWinds attack was a massive cyber incident that damaged thousands of US federal agencies, corporations, and organizations. It was a supply chain compromise where hackers (likely Russian-backed) inserted the SUNBURST malware into updates for SolarWinds’ Orion software. This granted access to networks of up to 18,000 customers.
Why it happened:
Attackers infiltrated SolarWinds’ software build process. They inserted the SUNBURST malware into a digitally signed update for the widely trusted Orion network management platform.
How it could be avoided:
Employ secure software development practices. Use Zero Trust principles to minimize the implicit trust placed in third-party vendor software updates.
5. WannaCry Ransomware (2017):
WannaCry was a devastating ransomware worm that spread globally in May 2017. The attack infected over 200,000 computers. It exploited the EternalBlue vulnerability in unpatched Windows systems. It encrypted data and demanded a Bitcoin ransom to unlock files. The incident exploited NSA-leaked tools and caused billions of dollars in damage.
Why it happened:
The ransomware spread rapidly as a worm by exploiting the EternalBlue vulnerability in unpatched, legacy Windows systems. This patch was available but not widely applied.
How it could be avoided:
Promptly install all security patches (especially for critical vulnerabilities like EternalBlue) and disable the outdated and vulnerable SMBv1 protocol.
Are You Learning From The Cyber Incidents That Shook The World?
Major cyber attack incidents serve as critical lessons. Organizations must apply them by prioritizing comprehensive cybersecurity frameworks, including regular vulnerability assessments, patch management, and stringent access controls like MFA.
Lessons from SolarWinds mandate rigorous third-party/supply chain monitoring. WannaCry and NotPetya stress developing and testing robust incident response plans with reliable backups. Operation Shady RAT highlights the need for continuous threat intelligence and advanced monitoring to build resilient defenses and ensure operational continuity.
But, even then, here’s a step-by-step guide on implementing a cyber incident response plan:
Your Cyber Incident Survival Blueprint: 6 Steps That Save Businesses
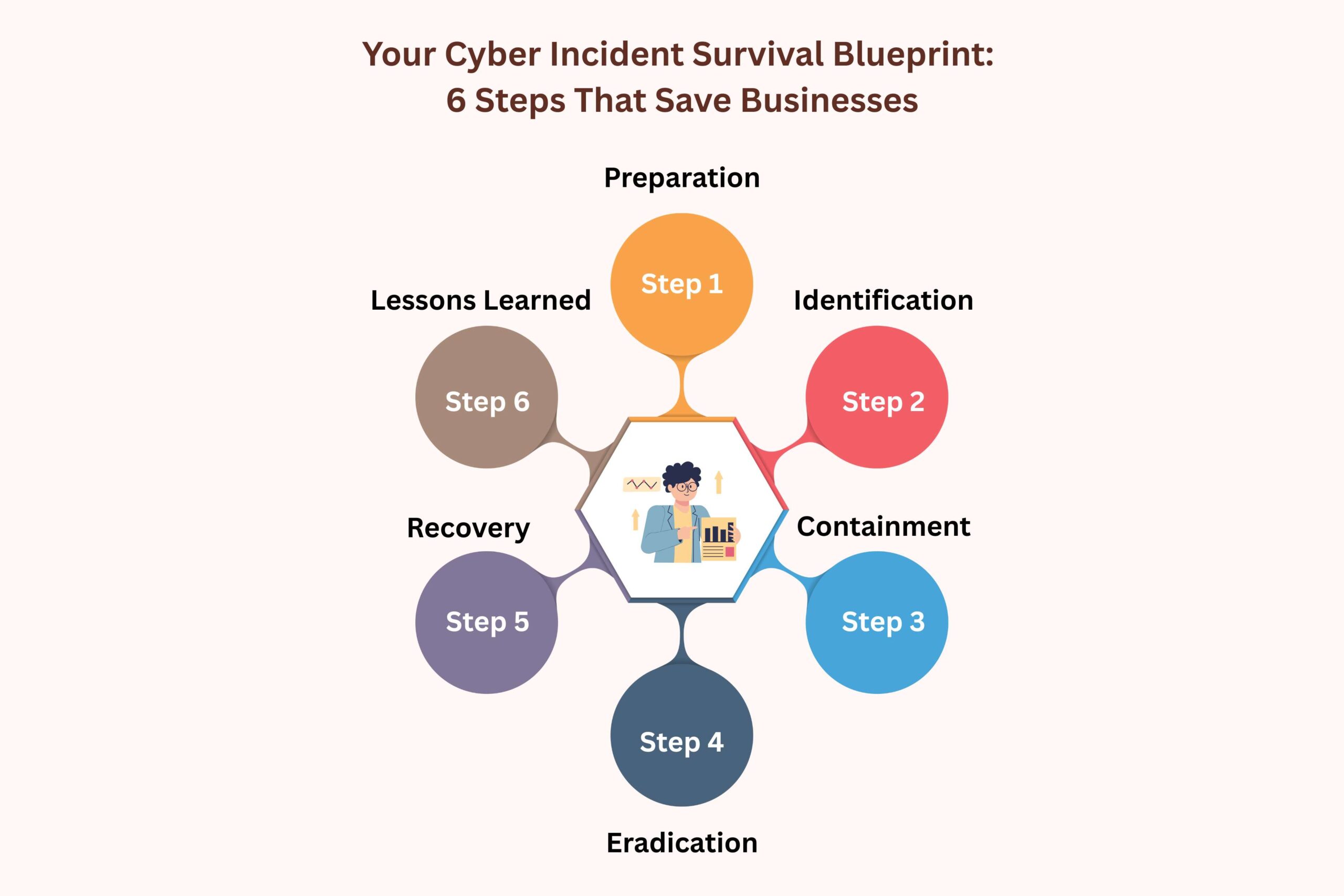
Here are the key steps typically recommended by cybersecurity authorities and reflected in government frameworks:
Step 1: Preparation
The first thing you need to do is establish and train an incident response team. Each team member must have defined roles and responsibilities.
Develop policies, procedures, and communication plans for the response. Focus on acquiring necessary tools and technologies.
And last of all, conduct regular risk assessments and cybersecurity awareness training for all employees.
Step 2: Identification
This step requires alertness from you and your team. Detects potential cyber incidents using monitoring, alerts, and threat intelligence.
Once you detect them, verify and categorize cyber incidents to understand their nature, scope, and impact. Create a list of priorities for each cyber incidents based on severity and business impact.
Step 3: Containment
This step is divided into two parts, i.e., short-term containment and long-term containment.
The goal of short-term containment actions is to prevent further damage, such as isolating affected systems. Meanwhile, long-term containment measures are to stabilize systems during investigation.
But that’s not the end of it. When you do contain the attacks, preserve evidence for forensic analysis. This will be helpful for the future, giving you a roadmap to handle these cyber incidents.
Step 4: Eradication
Identify the root cause of the cyber incidents, find out why it happened, and who did it. Then remove malware, unauthorized access, or compromised components.
Once the removal is completed, patch vulnerabilities and strengthen defenses to prevent recurrence. And with that, you have handled a major cyber incidents. But that’s not the end of the response plan.
Step 5: Recovery
The main goal of any response plan is to recover and restore affected systems and data after a cyber incidents.
To do so, validate system integrity and ensure normal operations resume. But this isn’t a one-time thing; after the cyber incidents occur, you must monitor systems closely for any signs of lingering threats.
Step 6: Lessons Learned
The last step is to conduct a thorough post-incident review involving all stakeholders. Document all the findings, gaps, and response effectiveness. Update cyber incidents response plans, policies, and training based on lessons. Share relevant threat intelligence with industry partners and authorities, if appropriate.
Make Security a Habit, Not a Reaction
We are at the end of Cyber Awareness Month. This is the yearly reminder that online safety is important for everyone. And we live in a time where being digitalized, staying aware is critical for our lives and organizations.
But awareness alone isn’t enough to stop cyber incidents; simple actions make a big difference. Organizations must move from simply knowing about attacks to taking immediate action. This means everyone, from employees to leaders, needs to follow security best practices.
Setting up a strong, unique password and turning on two-factor authentication. By making these small changes now, we can help secure our personal data and keep the digital world safer for all of us. Installing patches, using strong passwords, and having a plan to respond to cyber incidents are essential steps. Constant vigilance and proactive defense build a much stronger security posture.
Conclusion:
The lessons from Cyber Awareness Month are clear: knowledge alone cannot stop a breach. We must take action today to protect our digital future. In this blog, we went through the types, categories, and cyber incidents that took place in modern history, and why. To learn from the past mistakes and to create a safer, more secure cyberspace.
You and your organization must prioritize security patches, strong authentication, and swift cyber incidents response. We are all collectively responsible for moving from passive learning to proactive protection. Make consistent, smart choices online to minimize your exposure to future cyber incidents. And let’s end this Cyber Awareness Month with a little more awareness and a little action.
FAQs
What is the main difference between a virus and a worm?
A virus needs a host program to activate and spread when run. A worm is a standalone, self-replicating piece of malware that spreads across networks without human action.
What is ‘Zero Trust’ and why is it important for protection against cyber incidents?
Zero Trust means never implicitly trusting any user or device inside or outside the network. It requires strict verification for every access attempt, minimizing breach impact.
Where did the name Stuxnet come from?
The name Stuxnet is a combination of two keywords found within the code: “.stub” and “mrxnet.sys”, a driver file used by the sophisticated malware.






