In 2026, endpoint security spending is expected to continue rising as attacks become increasingly difficult to stop. The global EDR market has reached $ 6.4 billion, driven by a steady increase in zero-day attacks targeting remote laptops, cloud-connected devices, and unmanaged work endpoints. Security teams now deal with threats that move in minutes, not days, while businesses depend on distributed systems more than ever.
Endpoint detection and response addresses this gap by watching activity across every endpoint in real time and reacting when something looks wrong. Unlike traditional antivirus tools that rely on known signatures, it focuses on behavior, context, and intent. This approach helps security teams spot hidden threats, investigate incidents, and act quickly before damage spreads.
EDR platforms also reflect tighter regulations across the US and Europe, as well as growing pressure to demonstrate incident readiness. Endpoint detection and response now includes AI-driven behavioral analytics that reduce noise and support faster decisions. In this article, you will learn how modern EDR works, what has changed since earlier models, and how organizations can evaluate solutions built for today’s regulatory and security demands.
What Is EDR?

Endpoint detection and response, often called EDR, is a security approach that monitors activity on devices such as laptops, servers, and mobile systems. Instead of checking files only when they open, EDR watches how programs run, how users log in, and how data moves across networks. This ongoing view helps security teams catch suspicious behavior as it happens.
EDR collects detailed data from each endpoint and sends it to a central system for analysis. When something unusual occurs, such as a trusted tool running commands it doesn’t usually run, the system raises an alert. Security teams can then see a clear timeline of events, understand how the issue started, and decide what action to take.
What makes EDR different from older tools is its focus on response. Beyond detection, it allows teams to isolate affected devices, stop malicious processes, and investigate related activity across all endpoints. This makes EDR especially useful for handling modern threats that slip past traditional antivirus software and require quick, informed action.
2026 Strategic Risk Assessment
Businesses face a sharp rise in endpoint attacks in 2026. Remote laptops and cloud-connected devices remain prime targets as work stays distributed. Zero-day exploits strike quickly by exploiting unknown weaknesses, often targeting unmanaged endpoints such as personal phones or outdated company tablets. Once inside, threats can move across connected systems within minutes. Ransomware can lock critical files and demand payment within hours, while fileless malware hides in memory to bypass older security checks. Supply chain breaches introduce another risk, enabling attackers to gain access through trusted vendors. Even with average breach dwell time now under ten days, the financial impact still runs into millions for a single incident.
Western companies also operate under tighter regulatory pressure. New US SEC cyber rules and Europe’s DORA framework require breach reporting within 72 hours and clear proof of endpoint monitoring. Hybrid work increases exposure as employees log in from homes, cafés, and public networks. Attackers rely on phishing to quickly steal credentials, while AI-powered malware blends in by mimicking normal user behavior. Nation-state groups target finance and healthcare using PowerShell-based attacks, and office IoT devices running outdated software often become weak entry points. Endpoint incidents rose 25% year over year, pushing firms beyond basic antivirus tools.
Recent incidents show how costly these gaps can be. A major US retailer lost control last quarter after attackers moved from a single endpoint into payment systems. European banks reported repeated intrusions using similar methods from the same groups. SOC teams now process millions of alerts daily, most of them false positives from legitimate software. This slows response and drains staff energy. Traditional firewalls fall short since most attacks begin on devices. Strong endpoint security tools can reduce breach costs by up to 50%, according to recent studies.
EDR Fundamentals
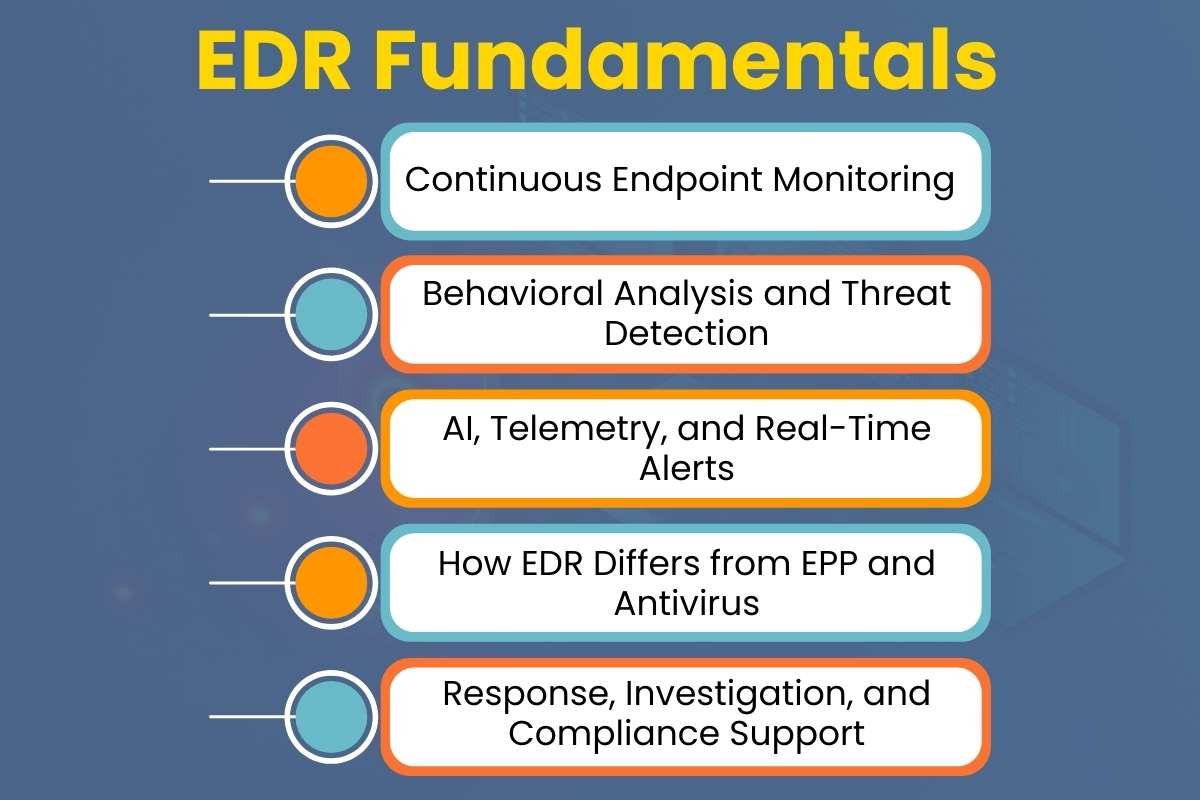
→ Continuous Endpoint Monitoring
Endpoint detection and response begins with nonstop visibility across devices such as laptops, servers, virtual machines, and mobile endpoints. EDR tools log processes, network activity, file changes, and login behavior in real time. This steady flow of data helps security teams detect early warning signs, such as odd data transfers, unauthorized scripts, or programs running outside standard patterns. By watching how endpoints behave over time, EDR builds a reliable activity baseline.
→ Behavioral Analysis and Threat Detection
Instead of relying only on known threat signatures, EDR focuses on how activity unfolds. If a trusted application suddenly contacts an unfamiliar server or runs commands it has never used before, the system raises an alert. This method helps detect zero-day attacks and fileless malware that traditional tools often miss. Security teams also get clear event timelines that show what happened before, during, and after an alert.
→ AI, Telemetry, and Real-Time Alerts
Modern EDR platforms use machine learning to process large volumes of endpoint telemetry. Indicators of compromise and indicators of attack are analyzed together to spot subtle patterns that signal risk. This approach reduces noise and delivers alerts with context, not just warnings, allowing teams to act faster and with more confidence.
→ How EDR Differs from EPP and Antivirus
Antivirus and endpoint protection platforms primarily focus on prevention through scanning and blocking. Endpoint detection and response focuses on investigating and remediating suspicious activity after it is detected. It pulls data from all endpoints into a central view, helping teams trace root causes, stop lateral movement, and contain damage.
→ Response, Investigation, and Compliance Support
EDR agents run lightly on endpoints and send key data to centralized systems for deeper analysis. From a single console, teams can isolate devices, stop malicious processes, and search across thousands of endpoints simultaneously. These capabilities support faster response times and help organizations meet regulatory expectations in the US and EU, where proof of rapid incident handling is required.
Also Read: The Ultimate Guide to Threat Detection Tools
How EDR Operates
Endpoint detection and response tools work through small agents installed on every device. These agents track activities such as running programs, accessing files, making network calls, and performing user actions. They send this data to a central platform, either in the cloud or on company servers. The platform runs checks around the clock to spot problems. For instance, if a process attempts to encrypt files without permission, the system flags it immediately. Teams see alerts with full details, including timelines of what led up to the issue.
Next, the platform uses intelligent analysis to connect the dots. It compares current behavior against standard patterns for that device or user. Machine learning helps identify real threats from everyday noise, such as a software update that appears unusual at first. When trouble shows up, endpoint detection and response can respond on its own. It might pause the bad process, block network access, or lock down the whole machine. Operators get one-click options to take further steps, such as scanning for more signs of attack. This setup keeps responses fast, often in seconds.
Finally, investigation tools give a clear picture of events. Users roll back through hours or days of activity to trace how an attack started. They search across all endpoints for similar issues, like the same bad file on multiple laptops. Reports compile evidence for audits or legal purposes. In 2026, many systems will add live updates from global threat feeds to stay ahead of new tricks. Teams practice with mock attacks to get comfortable. This whole cycle turns raw data into quick fixes, helping businesses limit damage and learn from each close call.
2026 EDR Advancements
1. Smarter Automation and Triage:
By 2026, endpoint detection and response will rely heavily on automation to reduce alert fatigue. Improved AI models filter out false positives and handle routine triage without human input. Analysts now focus on confirmed threats instead of sorting through noise.
2. XDR Integration for Unified Visibility:
Modern EDR tools connect with XDR platforms to combine endpoint, cloud, identity, and network data. This unified view helps teams understand how attacks move across systems rather than seeing isolated events.
3. Predictive Analytics and Threat Intelligence:
Advanced EDR platforms use predictive analytics to highlight high-risk vulnerabilities before they are exploited. By pairing real-time threat intelligence with endpoint behavior, organizations can prioritize fixes based on actual attacker activity rather than guesswork.
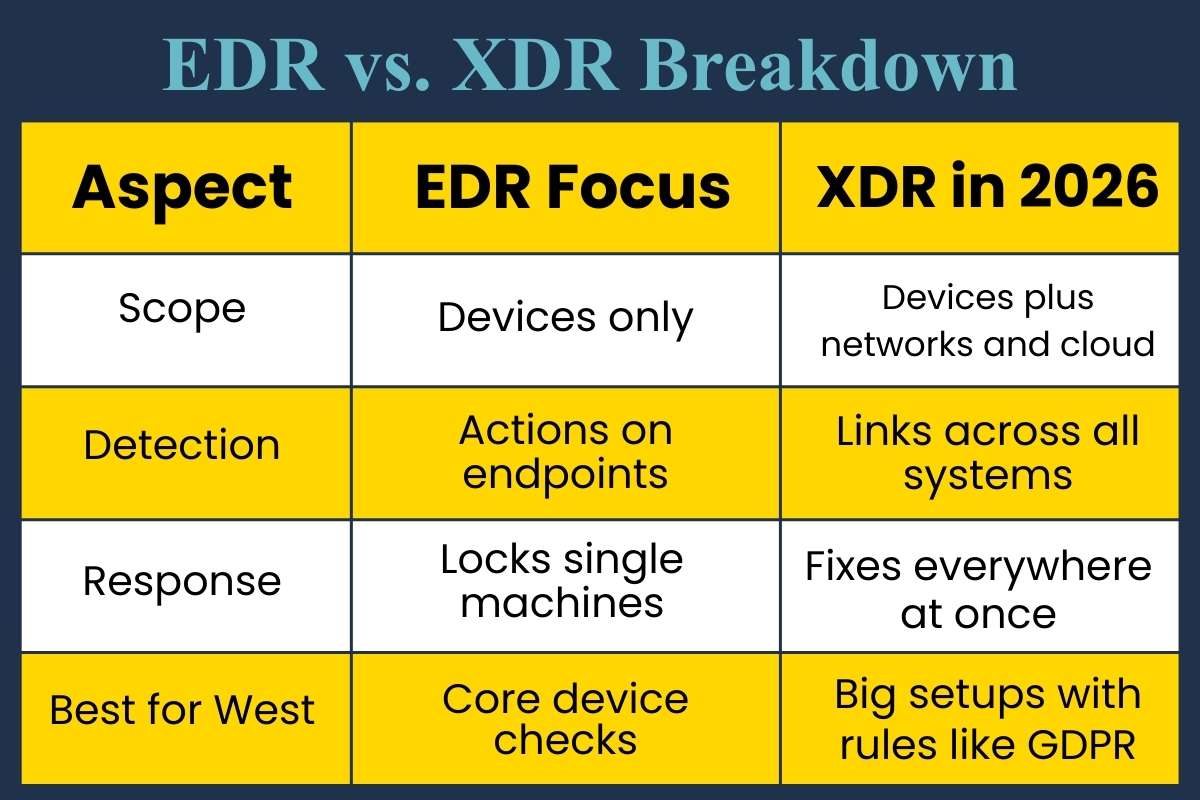
EDR vs. XDR Breakdown
Endpoint detection and response focuses on devices like laptops and servers. It tracks what runs on them and stops trouble before it starts. Extended detection and response builds on that base. It pulls in data from networks, cloud apps, and email, too. Companies get a single view of attacks that cross systems. EDR handles the starting point well. XDR takes over when threats spread out.
XDR cuts blind spots in complex operations. It correlates alerts from different sources. For example, EDR spots odd file activity on a laptop. XDR checks if that ties to a bad email or cloud login. Response actions chain together, like blocking a user account across tools. Teams save hours on hunts that span departments.
| Aspect | EDR Focus | XDR in 2026 |
| Scope | Devices only | Devices plus networks and cloud |
| Detection | Actions on endpoints | Links across all systems |
| Response | Locks single machines | Fixes everywhere at once |
| Best for West | Core device checks | Big setups with rules like GDPR |
Major firms lean toward XDR for scale. US banks and EU manufacturers face strict reporting requirements. XDR logs match those needs out of the box. Costs run higher upfront, but payoffs come in fewer significant breaches. Pure EDR suits smaller shops with simple setups. Many vendors offer upgrade paths later.
Top 2026 EDR Solutions
1. CrowdStrike Falcon
CrowdStrike Falcon continues to lead endpoint detection and response in 2026 due to its cloud native design and strong behavioral detection. It focuses on how activity behaves rather than relying on file signatures, which helps it stop zero-day attacks without slowing devices. Large banks, retail chains, and technology firms across the US rely on Falcon to manage tens of thousands of endpoints spread across multiple states. The platform continuously updates threat intelligence, often within minutes. Security teams value its clean dashboard that ranks risks by severity and business impact. Pricing typically starts at$60 per endpoint per year, and ransomware rollback remains one of its most trusted features.
2. Microsoft Defender for Endpoint

Microsoft Defender for endpoint detection and response works best for organizations already invested in Microsoft tools. It integrates tightly with Windows, Azure, Office, and Teams, giving security teams centralized visibility across users and devices. Many Western enterprises rely on it to meet SEC and internal audit requirements using built-in reporting and logs. AI-based tuning has significantly reduced alert noise, enabling small teams to manage large environments. Microsoft offers guided trials that help speed up deployment. Pricing usually ranges from $5 per user per month, making it accessible to mid-sized companies.
3. FortiEDR
FortiEDR stands out for its fast response actions based on real-world attack patterns. It can isolate infected machines in seconds and reverse malicious changes before damage spreads. European manufacturers and logistics firms often choose FortiEDR for environments with large numbers of IoT devices and factory systems. Its dashboard combines endpoint and network signals, helping bridge toward XDR use cases. Entry pricing starts around $40 per endpoint, and users report stronger control over false positives than with older tools.
4. Palo Alto Networks Cortex XDR

Palo Alto Networks Cortex XDR completes the top tier with deep support for cloud and enterprise-scale environments. It brings together endpoint data with signals from AWS, Google Cloud, and network tools. Large US retailers depend on Cortex during high-traffic seasons, when attack volumes spike. Its strength lies in correlating activity across systems to show the full path of an attack. Pricing generally starts at $70 per endpoint, aimed at complex enterprise deployments.
Also Read: How Cybersecurity Firms Strengthen Critical Infrastructure Against Digital Threats?
Quick Comparison of Leading Platforms
| Vendor | Key Strength | Western Appeal | Starting Price |
| CrowdStrike Falcon | Behavior hunting | Zero-downtime deploys | $60/endpoint |
| Microsoft Defender | Ecosystem integration | Compliance reports | $5/user |
| FortiEDR | Fast playbooks | IoT coverage | $40/endpoint |
| Palo Alto Cortex | Multicloud links | Enterprise scale | $70/endpoint |
Implementation Roadmap
Step 1: Assess Your Setup
- Make a complete list of all devices on your network.
- Include laptops, servers, phones, and IoT equipment.
- Note operating systems (Windows, macOS, Linux) and count the total endpoints.
- Run a free vendor scan to find weak spots.
- Choose an endpoint detection and response platform based on your size and budget.
Step 2: Deploy Agents
- Roll out in phases: start with a test group of 10-20 devices.
- Install lightweight agents via group policies or MDM tools.
- Test for slowdowns and fix issues before the whole push.
- Link to firewalls, SIEM, or other systems for data sharing.
- Expect 1-2 weeks for company-wide coverage.
Step 3: Train and Test
- Hold sessions for your security team on the dashboard.
- Practice responses: isolate devices, kill processes, review timelines.
- Run simulated attacks to build muscle memory.
- Document procedures for all staff and compliance checks.
- Verify logs meet U.S. SEC or EU standards.
Step 4: Go Live and Monitor
- Launch automated routine fixes, such as IP blocks.
- Watch alerts daily in week one, adjust rules to reduce noise.
- Update threat feeds weekly and agents monthly.
- Track metrics: 100% coverage, response under 60 minutes.
- Quarterly reviews keep performance high.
Quick Wins Table
| Phase | Timeframe | Key Action | Expected Gain |
| Assess | 1 week | Device inventory | Spot 20% gaps |
| Deploy | 2 weeks | Agent rollout | Full visibility |
| Train | 1 week | Mock drills | 50% faster response |
| Monitor | Ongoing | Rule tuning | Cut false alerts by 40% |
Challenges and Fixes

- Too many alerts overwhelm teams: Endpoint detection and response systems flag normal apps as risks, leading to alert fatigue. Fix this by tuning AI rules in the first month to focus on real threats. Teams cut noise by 40% with vendor-guided setups.
- High costs for small businesses: Full endpoint detection and response suites hit budgets hard at $50+ per device. Start with managed services or free trials to test value before buying. Many offer pay-per-use pricing for startups with fewer than 500 endpoints.
- Hard to integrate old systems: Legacy servers clash with modern agents, causing gaps. Use cloud-native options that support Windows XP to the latest versions. Phased rollouts avoid downtime during switches.
- Staff lack investigative skills: Most teams handle basic alerts but struggle with deep hunts. Run free vendor training and mock drills weekly. Pair with SOAR tools for one-click forensics.
- Slow updates miss new attacks: Daily threat feeds lag behind zero-days. Pick platforms that offer real-time global intelligence sharing. Auto-updates keep coverage fresh without manual work.
- Compliance proof takes effort: U.S. SEC and EU rules demand detailed logs. Build in report templates from day one. Automated audits save hours on filings.
Future Outlook
The endpoint detection and response market is projected to grow at 23.8% annually through 2033, reaching $28.6 billion. Cyber insurance rules force companies to adopt strong tools or face higher premiums. Quantum threats push vendors to add encryption that resists new computing power.
Zero-trust models are baked into endpoint detection and response by default. Every device proves itself constantly, cutting insider risks. Autonomous agents handle 80% of responses without human intervention, freeing teams to focus on strategy. Western firms in finance and health are leading this shift to comply with strict data laws.
Expect deeper AI that predicts attacks based on user behavior or global news. Edge computing ties EDR to IoT in real time for factories and smart offices. Open standards let tools from different vendors work together smoothly.
Conclusion
Endpoint threats in 2026 move faster, hide better, and cause more damage than ever before. Remote work, cloud systems, and unmanaged devices have made endpoints the most common entry point for attackers. Traditional tools can no longer keep up with zero-day exploits, fileless malware, and coordinated campaigns that spread in minutes. Endpoint detection and response fills this gap by providing teams with continuous visibility, clear investigation paths, and the ability to act before incidents spiral out of control.
As regulations tighten, EDR has also become a compliance requirement, not just a security measure. The right platform helps reduce alert fatigue, shorten response times, and lower breach costs while supporting audits and reporting. Endpoint detection and response works best when treated as an ongoing process rather than a one-time deployment. Organizations that invest early, train teams, and tune systems continuously are far better prepared for what comes next.