When it comes to cybersecurity, prevention is just as important as detection. There are various methods and tools to detect a cyberattack. But, as technology is progressing, so are the ways in which hackers try to infiltrate your systems. They can easily slip through security systems. This has led to an increase in technology that can alert the user when an attack is happening in real-time. This is where indicators of attack (IOAs) come in. But what exactly are they? How do they work? Let’s find out.
What are Indicators of Attack and How do They Work?

Indicators of Attack are patterns that indicate that a system might be currently under attack. IOAs focus on the behaviour of the attacker and what he is trying to accomplish. This is different from Indicators of Compromise (IOCs). IOCs detect specific pieces of malware in the aftermath of the attack.
Indicators of attack try to catch a cyber threat in the early stages of the attack. For example, if an employee’s account starts accessing work information after hours, then it might be a sign that their account has been compromised. Let us take another example. There is an admin account. If multiple failed login attempts occur within seconds, then it might be an indicator of a forced entry attempt.
In short, IOAs are telltale signs that a cyber attack is currently in progress. They help in mitigating any cyber threat as quickly as possible. They are a step up from the traditional methods used to detect cyber attacks. There are several different types of indicators of attack. After all, a secure system can counter any type of cyber threat. So what exactly are the different types of IOAs?
What are the Different Types of Indicators of Attack?
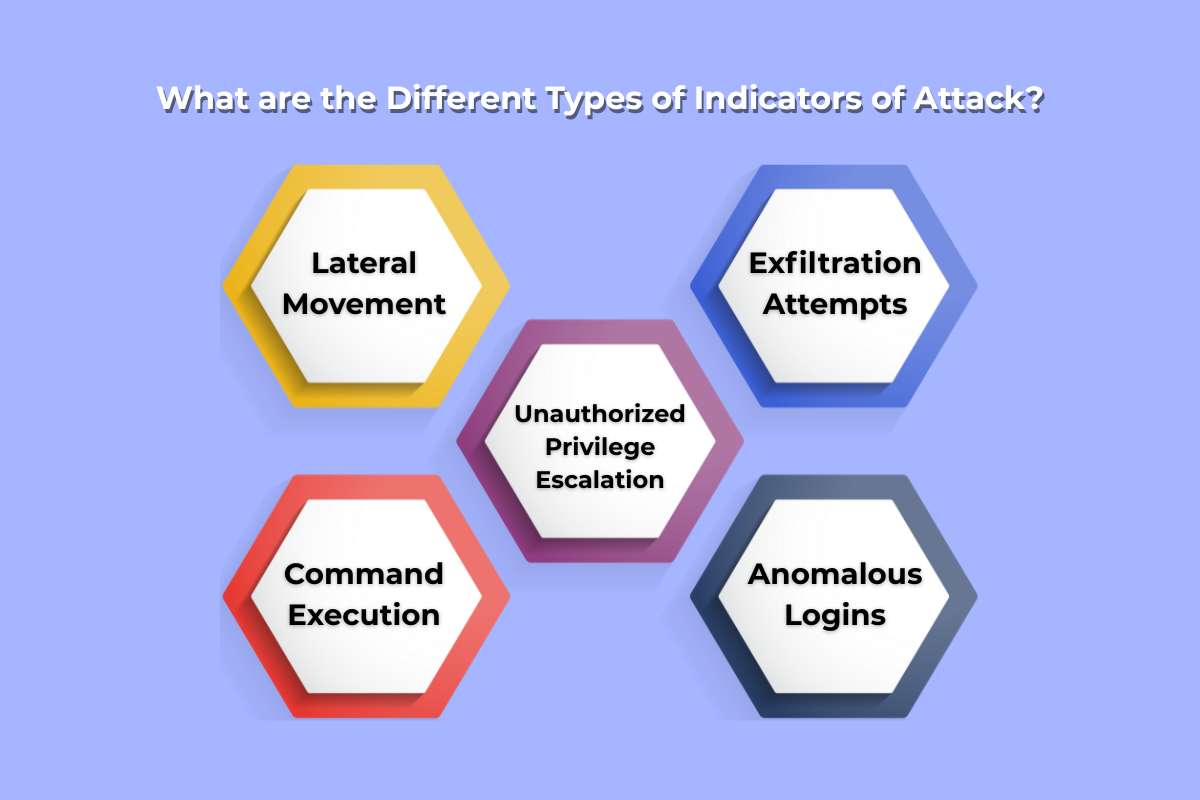
1. Lateral Movement
Lateral movement is the movement of the attacker after they have infiltrated a network. The attacker usually moves from one system to another, searching for sensitive information. This type of movement can often go unnoticed. Hackers progress through the system quietly and stealthily. IOAs include the different suspicious connections within the system. Detecting lateral movement is important as it means that the attacker is expanding their presence in the network.
2. Exfiltration Attempts
This involves transferring unauthorized data out of a network or a system. Attackers try to transfer intellectual property and personal information to an external location. The indicators of attacks include the transfer of large data files. They can also include unknown and abnormal patterns of communication. Stopping these types of attacks in the early stages is crucial. This is because exfiltration attempts can often lead to huge data breaches.
3. Unauthorized Privilege Escalation
This occurs when a basic user account, which is intended for base-level operations, gains access to restricted areas of the network. Hackers and attackers exploit vulnerabilities to gain higher access. Such access enables them to disable any remaining security controls and manipulate other systems. These privileges without any access need to be detected and addressed quickly. An attacker with major control over your network is dangerous.
4. Command Execution
This means running unauthorized scripts and commands that are not part of the normal process. Attackers use a customized script to deploy malware into a system. When an unauthorized user starts executing administrative commands, it is an IOA. Recognising if any unauthorized scripts are running is crucial. It should be caught as early as possible. Because if you are too late, then the deployed malware can corrupt your systems.
5. Anomalous Logins
Anomalous Logins refer to login attempts from unknown users or devices. For example, a user who logs in from a specific geographical location suddenly attempts to log in from a different place. Prompt detection and response ensure stronger account security and reduce the risk of fraud
Indicators of attacks have become essential for strong cybersecurity. But they also have their limitations. What are the disadvantages?
Limitations of Indicators of Attack: Where do IOAs Fall Short?

1. Context Dependency:
IOAs often require deep contextual understanding to be meaningful. A suspicious action, such as a script execution or unusual network traffic, may not always signify an attack. It could be a legitimate business activity.
2. Limited Coverage Against Novel Attacks:
IOAs are effective at spotting known behaviors. But highly sophisticated attackers constantly adapt their methods. If adversaries use unique techniques or subtle variations, existing IOAs may fail to identify them.
3. Dependence on Correlation with IOCs:
IOAs work best when correlated with Indicators of Compromise (IOCs). This dependency means IOAs alone cannot provide full visibility into attack campaigns. They require organizations to adopt a multi-layered approach to threat detection and response.
4. High False Positives:
IOAs focus on detecting attacker behavior. Normal user activities can sometimes mimic malicious patterns. This overlap increases the chances of false positives, which can reduce trust in the alerts and waste valuable response time.
5. Resource-Intensive Monitoring:
Implementing IOAs requires continuous monitoring of system activity and user behavior. This process demands advanced tools, skilled analysts, and constant updating of detection rules. Smaller organizations may struggle to allocate resources for such ongoing efforts.
Case Study: 2017 Equifax Data Breach
The 2017 Equifax breach exposed 147 million consumers’ data after hackers exploited an unpatched Apache Struts flaw. Several IOAs could have revealed the attack earlier, but went unnoticed:
- Failed Patch Scans – Repeated scan alerts flagged the vulnerability, but escalation never occurred.
- Expired SSL Certificates – IOAs could have flagged unusual encrypted flows.
- Anomalous Portal Activity – Queries and admin commands in the dispute portal went unchecked.
- Privilege Escalation – Attackers gained higher access levels without detection.
- Ignored Alerts – Existing warnings were lost in the noise; IOAs could have correlated and prioritized them.
With IOA-driven monitoring, Equifax could have spotted attacker behavior earlier. They reduced the six-week dwell time, limiting damage.
Source: Seven Pillars Institute
Conclusion
Indicators of Attack provide the foresight needed to detect malicious activity. Security teams can catch it before it escalates into a full-scale breach. IOAs monitor attacker behaviors, tactics, and anomalies in real time. They enable organizations to shift from a reactive to a proactive defense strategy. As cyber threats continue to evolve, incorporating IOA-based detection into your cybersecurity framework has become a necessity to stay ahead of modern, sophisticated threats.
FAQs
1. What is the main difference between indicators of attack and indicators of compromise?
A. Indicators of attack are used to detect ongoing attacks, and indicators of compromise are forms of evidence of an attack that has already happened.
2. How to reduce false positives while using indicators of attack?
A. To reduce false positives, you must fine-tune security rules and alert thresholds for your specific environment.
3. What are Honeytoken alerts?
A. Honeytokens are digital resources that are purposely designed to be attractive to an attacker. They do not serve any real purpose within your systems. However, when they are used, they trigger an alert of potentially unauthorized access.