We don’t understand how important keyboards are to our digital lives. Our jobs, our social media use, and our entire digital life depend on our keyboard. Your keyboard has access to everything on your computer and phone, from your credit card number to your passwords and even your private messages.
These passwords, numbers, and messages need to be secure and protected from all types of cyber hacking. But what if your keyboards are hacked? What if a program is tracking every key you press and records it? How safe are you? And most importantly, how can you protect your devices from such programs?
Well, these types of programs are called ‘Keystroke Logging Software.’ In this blog, we will try to understand what they are, how to find them, and how to get rid of this software from your devices.
What is Keystroke Logging Software?
A keylogger is a software that records every key you press on your keyboard. This can include your private data like passwords, card information, and even your private messages and your Google searches.
Keystroke logging software is a form of spyware that is used for both legitimate and malicious purposes. There are two primary types of keyloggers, and they work a bit differently from each other.
So, let’s understand the two keyloggers and how they work.
Types of Keystroke Logging Software

There are two types of keyloggers, i.e., software keyloggers and hardware keyloggers. They work a little differently; here’s how:
1. Software Keyloggers:
This type of keylogger is uploaded to a computer without the user’s knowledge. They can be bundled with other malware, like a Trojan horse, or delivered through phishing emails and malicious websites. Once they are installed, they silently run in the background, recording all your keystrokes by intercepting the signals from your keyboard to the operating system. And then these recorded keystrokes are saved to a secret hidden file accessed by the software’s owner.
2. Hardware Keyloggers:
These are small devices that are plugged between your keyboard cable and the computer’s USB port. They look very similar to a normal adapter, making it really hard to find them. They work the same way as the keystroke logging software, except they save all the captured information in the device’s internal memory and can be retrieved later by the person who installed it.
Now that we know the main types of keyloggers, let’s talk about the
Types of Keyboarding Software:
In software keyloggers, three main types of software can be used to attack your device. Let’s list them one by one, shall we?
1. API-based keyloggers
This is the most common type of keystroke logging software, and it is also one of the hardest to detect. This one hooks onto the device’s API (Application Programming Interface). An API is what allows apps to listen to your keystrokes and interpret them. Getting attached to it helps the keylogger to intercept these keystrokes and send them to the intended application.
2. Form Grabing
These types of keyloggers are designed to steal data from web forms. Instead of recording each stroke, it waits for you to submit the form, i.e., login, checkout, or sign up, and steals the data entered into the form. This is highly effective for stealing login credentials, credit card numbers, and other sensitive information from websites.
3. Kernel-Mode Keyloggers
These are highly advanced keystroke logging software that operate at the deepest levels of your devices. Because they have the highest level of privilege, they are really hard to detect and remove. They can intercept keystrokes before they are even processed by the OS’s normal functions.
4Screen Loggers
While not a traditional keylogger, it is usually bundled with keystroke logging software. As the name suggests, it takes periodic screenshots of your device, especially when you open a new webpage or application. This is especially effective at capturing information entered using a virtual or on-screen keyboard, which is a common method for trying to evade standard keyloggers.
Risks of Keystroke Logging Software

“Along with spyware, keylogging malware was ranked as the highest threat by the 2019 Global Threat Intelligence Report.” A quote by Global Threat Intelligence.
When used with malicious intent, keystroke logging software can be a big blow to your privacy. It is a big threat to individuals and organizations alike. The core danger lies in its ability to silently collect a wealth of sensitive data, which can then be used for a variety of criminal activities.
Here are some of the risks associated with keystroke logging malware:
1. Financial Loss:
This is one of the major reasons behind most of the keylogger attacks. It is used to capture:
- Banking Credentials: Usernames, passwords, and account numbers for online banking, allowing attackers to transfer funds directly from your accounts.
- Credit Card Information: Full credit card numbers, expiration dates, and security codes (CVVs) are entered on e-commerce sites, leading to unauthorized purchases and financial fraud.
- Cryptocurrency Wallet Passwords: Stealing the private keys or passwords to digital wallets results in the theft of valuable cryptocurrencies.
2. Identity Theft:
Keyloggers are like a goldmine for identity thieves. They capture most of your necessary information, such as:
- Social Security Numbers: Often entered on government, financial, or medical websites.
- Full Names, Addresses, and Birthdays: The building blocks for creating fake identities.
- Driver’s License or Passport Numbers: Used to open new lines of credit or loans in your name.
3. Account Compromise:
One habit that we all have is to reuse the same password on various websites. While it makes it easy for you to remember the password, it also helps hackers access all your data by using keyloggers. An attacker who gains access to your email account through a keylogger can then use it to reset the passwords for your social media, cloud storage, and other online services. This can lead to:
- Loss of Personal Data: Access to private emails, photos, and documents.
- Privacy Violations: Spying on private conversations and monitoring your online habits and communications.
- Reputation Damage: Posting malicious content or sending fraudulent emails to your contacts from your compromised accounts.
4. Corporate and Industrial Espionage:
Keyloggers are a serious threat to businesses and can be used for:
- Theft of Trade Secrets: Stealing confidential business plans, customer lists, and intellectual property.
- Unauthorized Network Access: Gaining entry to a company’s internal network by capturing employee login credentials.
- Financial Data Breach: Exposing corporate financial information can lead to significant losses and a destroyed reputation.
5. Malware Delivery:
Keyloggers often do not operate alone. They are frequently bundled with other forms of malware, such as Remote Access Trojans (RATs). A RAT allows the attacker to gain full control of your computer, giving them the ability to not only record your keystrokes but also to:
- Take screenshots of your screen.
- Access your webcam and microphone.
- Download, delete, or modify files.
Case Studies: Keystroke Logging Software in Action: A Costly Business Breach
A small construction company became the victim of a devastating cyber-attack when an employee unknowingly opened a malicious email. Hidden within it was keyboard logging software, a tool cybercriminals use to secretly record keystrokes and steal sensitive information like banking credentials. Using the captured login details, criminals initiated multiple unauthorized ACH transfers, stealing $550,000 from the company’s accounts.
Although the bank managed to recover part of the funds, the company still faced a significant financial hit and legal costs. The lack of a cybersecurity plan and employee awareness delayed their response, amplifying the damage.
This case highlights the serious risks posed by keyloggers, especially to small businesses that often lack robust defenses. It underscores the importance of employee training, multi-layered authentication, transaction alerts, and a well-prepared incident response plan. In today’s digital landscape, understanding and defending against keystroke logging malware is not just a technical necessity; it’s essential for business survival.
Source: National Cybersecurity Alliance Case 2: A Construction Company Gets Hammereed by A Keylogger
How to Detect Keystroke Logging Software

Being a spyware, keystroke logging malware is really hard to detect. However, by being vigilant and knowing what you must do, you can increase your chances of finding and removing a keylogger.
There are several methods to detect keyloggers. Let’s break them down, one by one.
1. Use Reputable Antivirus and Anti-Malware Software
This must be your first line of defense against keystroke logging software. A good antivirus with anti-spyware capabilities, such as Norton 360 and TotalAV, is designed to detect and quarantine or remove keyloggers.
- Run a full system scan: Don’t just rely on real-time protection. A deep, full system scan will thoroughly check all files for known malicious signatures.
- Keep your software updated: New keyloggers are created all the time. Ensure your antivirus definitions are up to date to protect against the latest threats.
2. Check for Suspicious Processes and Applications
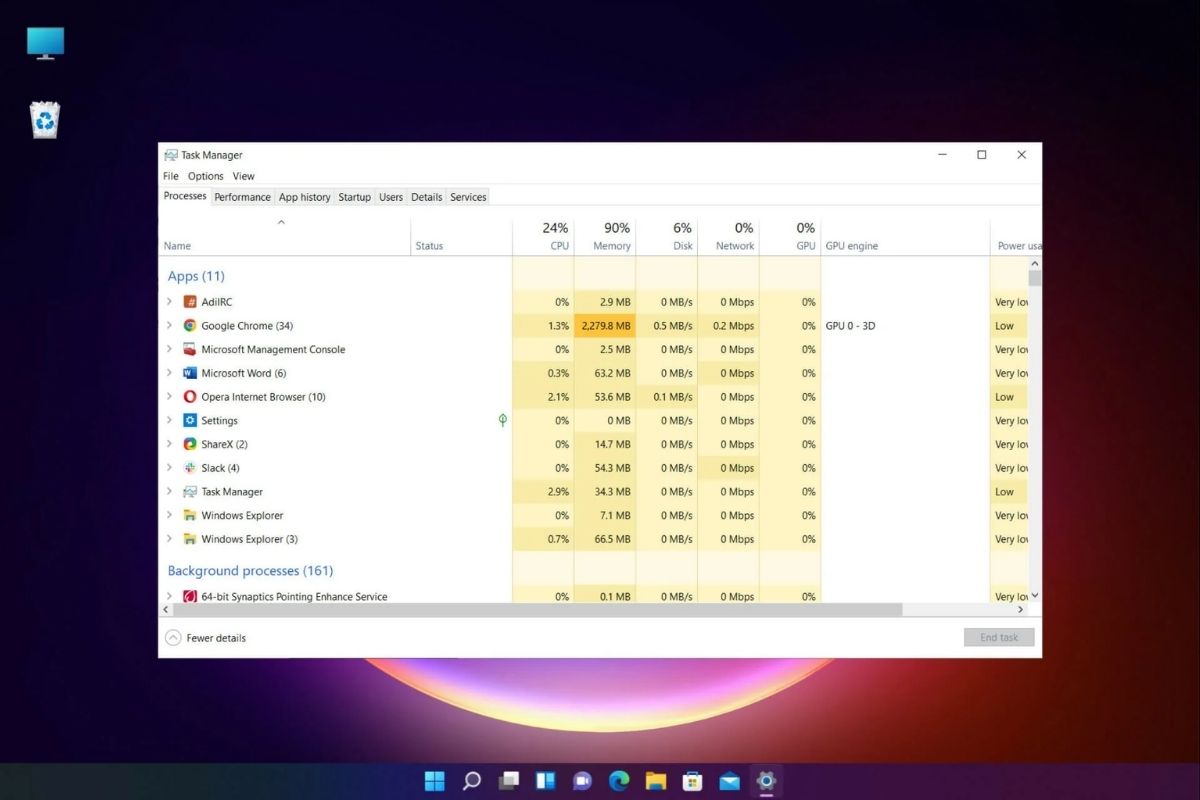
Just like other applications, keyloggers need to run on your systems. So, one of the easiest ways to detect them is by checking your system’s task manager and activity monitors.
Here’s how you can check for keystroke logging malware in your device.
- Task Manager:
Step 1: Open Task Manager. The quickest way is to press Ctrl + Shift + Esc at the same time.
Step 2: Once you open the task manager, you will see a list of running applications under the “Processes” tab. If you want detailed information on the application, such as the Process ID (PID) and the user it’s running under, click on the “Detail” button.
Step 3: This is the most critical part of the process. Be on the lookout for names that are completely foreign to you. While many legitimate processes have cryptic names (e.g., svchost.exe, explorer.exe), a keylogger might have a name like logkeys.exe or winlog.exe (a fake version of the legitimate winlogon.exe).
Also, look for applications that have an unusually high amount of CPU, memory, or network resources when you are not actively using a demanding application.
Step 4: Once you’ve identified a process you think is suspicious, do not immediately end the task. You might accidentally shut down a legitimate and critical system process, which could cause your computer to become unstable or even crash.
Instead, right-click on the suspicious process and select “Search online.”
Step 5: Once you are sure, do not directly stop the task as it may have a “watchdog” process that will immediately restart it. First of all, disconnect the internet; this will prevent the malware from sending your data to the attackers.
Run a full system scan with a reputable and up-to-date antivirus and anti-malware program. These tools are designed to end the malicious process but also to delete all related files and registry entries to prevent it from coming back.
If the antivirus cannot remove it, you may need to boot your computer into Safe Mode with Networking or use a bootable antivirus rescue disk to clean the system before the malware has a chance to run.
Step 6: Once the malware is deleted, change your passwords from a trusted device.
Pro-tip: If you want to protect your device, enable Two-Factor Authentication (2FA) and passkeys with a trusted device, which are cryptographic logins that don’t require you to type a password at all.
Best Anti-Virus for Protection against Keyloggers
Here is a list of antivirus programs that you can install to protect your device from keyloggers.
1. Norton 360:
Norton 360 is one of the best antivirus programs in the market right now. Norton 360 uses AI for malware detection, which means it can consistently achieve 100% detection score for keyloggers. It also features a full password manager (to prevent manual entry) and a secure browser, both of which help against keystroke logging.
- Price: $49.99/year (5 devices; renews $119.99)
2. Total AV Total Security:
Total AV is known for its thorough device checkup, which has scored 99% in malware and keylogger-specific tests. It features a web safety extension that can block keylogger-infected sites and anti-phishing technology. And most importantly, this antivirus offers you all the advanced antivirus features at a very affordable price.
- Price: $49.00/year (8 devices; renews $149)
3. Bitdefender Total Security:
Bitdefender boasts of 100% malware (including keyloggers) detection in independent tests and being the top-rated antivirus software by multiple labs. Its special “Safepay” secure browser with a virtual keyboard prevents any keystroke interception, hence protecting your device from all types of keystroke logging software.
- Price: $19.99–$70/year (5 devices, varies by promo; renews up to $100+)
4. McAfee Total Protection:
McAfee is one of the most popular antivirus software program that you can find and for a good reason. It has perfect scores against keyloggers, and most advanced malware in head-to-head reviews. McAfee blocks new, zero-day variants and highlights suspicious websites that could be hosting logging scripts.
- Price: $49.99/year (Unlimited devices with auto-renewal; renews at $120)
Conclusion:
In a digital world, the threat of keystroke logging malware is a silent danger. These malicious programs can steal your financial details, personal messages, and even your identity. Keyloggers can be software or physical devices, and the risks they pose are serious—from financial theft to identity fraud.
The good news is you can protect yourself. Being aware is the first step. Take a proactive approach to cybersecurity: use and regularly update quality antivirus software. Learn to spot unusual activity and be cautious with every link you click and file you download. If you suspect a keylogger, act immediately: run an offline scan and change all your passwords using a secure device.
Your cybersecurity is a continuous responsibility. By using the right tools and smart habits, your keyboard remains a tool for creation and connection—not a gateway for compromise..
FAQs
1. How do anti-keyloggers work beyond simple signature detection?
Advanced anti-keyloggers use behavioral analysis. They monitor for suspicious actions, like a program trying to hook into your keyboard’s input stream, to detect and block even unknown keyloggers.
2. Can a keylogger be built into a mechanical keyboard’s firmware?
Yes, though it’s extremely rare. A keylogger could be embedded in a keyboard’s firmware to capture keystrokes at the hardware level, making it invisible to standard antivirus software.
3. Does using an on-screen keyboard make me immune to keyloggers?
No. While it can defeat traditional keyloggers, many modern keyloggers are also screen loggers. They take periodic screenshots to capture what you type on the virtual keyboard.
Also Read: Can People See Everything You Type? Here is What You Should Know About Keystroke Logging.






