Today, doing almost anything online requires you to have an account. You often need access to these accounts. For a long time, this access was granted to you through a secret arrangement of letters, or, as we all know them, passwords. But, as technology has evolved, so has the w
ay in which people gain access to various online services. This evolution has come in the form of passwordless authentication. But why have passwords fallen out of favour? Why is there a rise in different forms of authentication?
Why Do You Need Passwordless Authentication?

Today, people need a variety of applications and services. These can be for work or for personal use. Regardless, many of these applications require people to give a password to use them. And even though securing your account and personal data is necessary, the problem arises when you need to memorize tons of passwords.
This can lead to people using risky measures to remember all passwords. They might use a single password for multiple accounts. Many such accounts are created on websites that are not very secure. They can also use methods like writing down passwords on sticky notes or using simple and weak passwords. These can leave their information vulnerable to cyber criminals. They can easily take advantage of such weaknesses.
Passwordless Authentication is a way to improve security while reducing the complications of password management. It can also reduce the burden of having to issue, secure, and reset passwords. More and more organizations are moving away from the traditional password creation. This is because other methods help in customer engagement. Many of these are also quicker and more efficient, and can remove the hassle of creating a password. But how exactly do they work?
What is Passwordless Authentication and How Does It Work?
Passwordless Authentication means verifying a user’s identity through means other than a password. It instead uses even more secure authentication factors. The most common factors that this type of authentication relies on include:
1. Knowledge: Knowledge focuses on establishing the fact that you know about something specific. For example, a secret question that only you might know the answer to
2. Possession: This factor focuses on proving you have a particular thing. This can include a security key or a one-time password (OTP).
3. Inherence: Inherence deals with proving that you are who you say you are. This factor is usually verified through facial or biometric scans.
Now you know what passwordless authentication is and how it works. You also know how they can be beneficial in strengthening the security of an application or software. But how many different ways can you exactly implement it? Which is the one that is most beneficial for you?
What are the Types of Passwordless Authentication
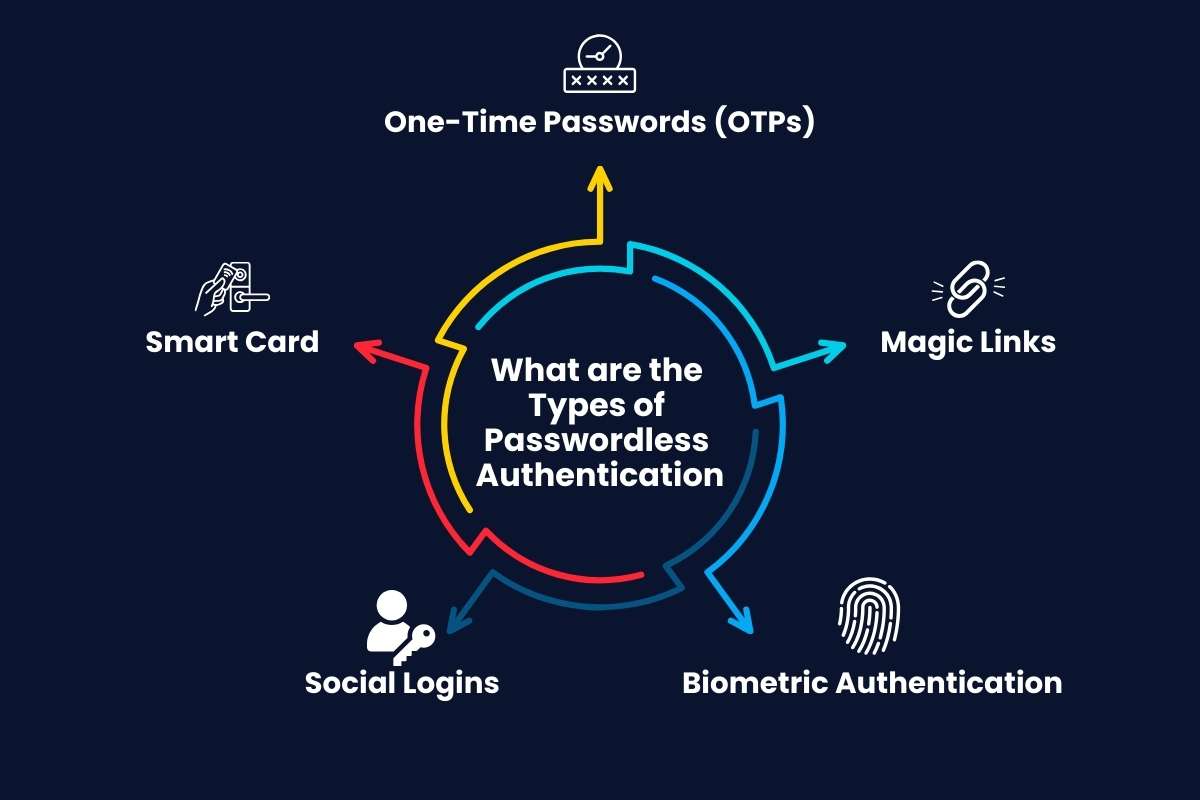
1. One-Time Passwords (OTPs)
This is one of the most common forms of passwordless identity verification. Do not let the ‘password’ in the name mislead you. One-time passwords are a form of randomly generated strings consisting of letters and numbers. A different string is generated every time you attempt to log in. These strings are sent to the user via email or SMS and must be entered correctly for the user to proceed. The key element in an OTP is that, as the name suggests, you can only use a generated password one time.
There is also a variation of these types of passwords known as a Time-Based One-Time Password or TOTP. These passwords are only active for a certain amount of time. The timeframe is about one to two minutes. If you fail to provide the password within the specified time, then a new one is generated.
2. Magic Links
In this method, users provide their email address or phone number and are provided with a link. This link then takes them to the website or application in question. Magic links are typically used in business settings. They eliminate the need for each and every employee to create and remember their password. The one downside of this is that anyone who has access to credentials for an email will also receive the link.
3. Biometric Authentication
Biometric Authentication uses human features and characteristics for identification. This is one of the major forms of authentication, as it relies on individual traits of a person. Hence, these are also some of the most secure techniques of identification. It is hard for hackers to replicate these aspects, especially due to the newer deepfake and liveness detection technologies.
Also Read: 10 Key Benefits of Biometric Authentication You Should Know
4. Social Logins
Social logins enable access through third-party social platforms like Facebook, Google, and LinkedIn. Authentication is done by validating a user’s identity through their social media. It does this from the existing cookies that are on these sites. This is one of the riskier forms of passwordless authentication, as it relies on third-party apps to confirm a user’s identity, while many of them themselves might not be reliable.

5. Smart Card
Smart cards are cards or readers that enable access to applications. These cards have chips that contain data. They also contain Radio Frequency Identification (RFID) connectivity to manage user access. The major disadvantage of using smart cards is the user experience. These are physical cards that need to be carried around. They need to be inserted into a computer or an authentication device to verify identity. This procedure is expensive to implement. It also requires identity recognition software to be installed on the host computer. Hence, these are used as a high security measure.
These are some of the most popular ways in which passwordless authentication is carried out. But you must be wondering, are these types of methods completely foolproof? There are many advantages as well as disadvantages to such techniques. What are they?
Case Study: How Accenture Has Been on A Passwordless Journey for Years
Accenture first implemented passwordless verification back in 2019. They did this in a partnership with Microsoft. As of 2025, 75% sign-ins occur through passwordless authentication. Accenture has also implemented Microsoft’s authenticator application ‘Nudge’. This resulted in 208k employees being registered on ‘Nudge’.
Accenture’s case is definitely a testament to how implementing this form of authentication can transform a company’s cybersecurity.
Source: https://www.accenture.com/us-en/case-studies/about/passwordless-journey
Pros and Cons of Passwordless Authentication
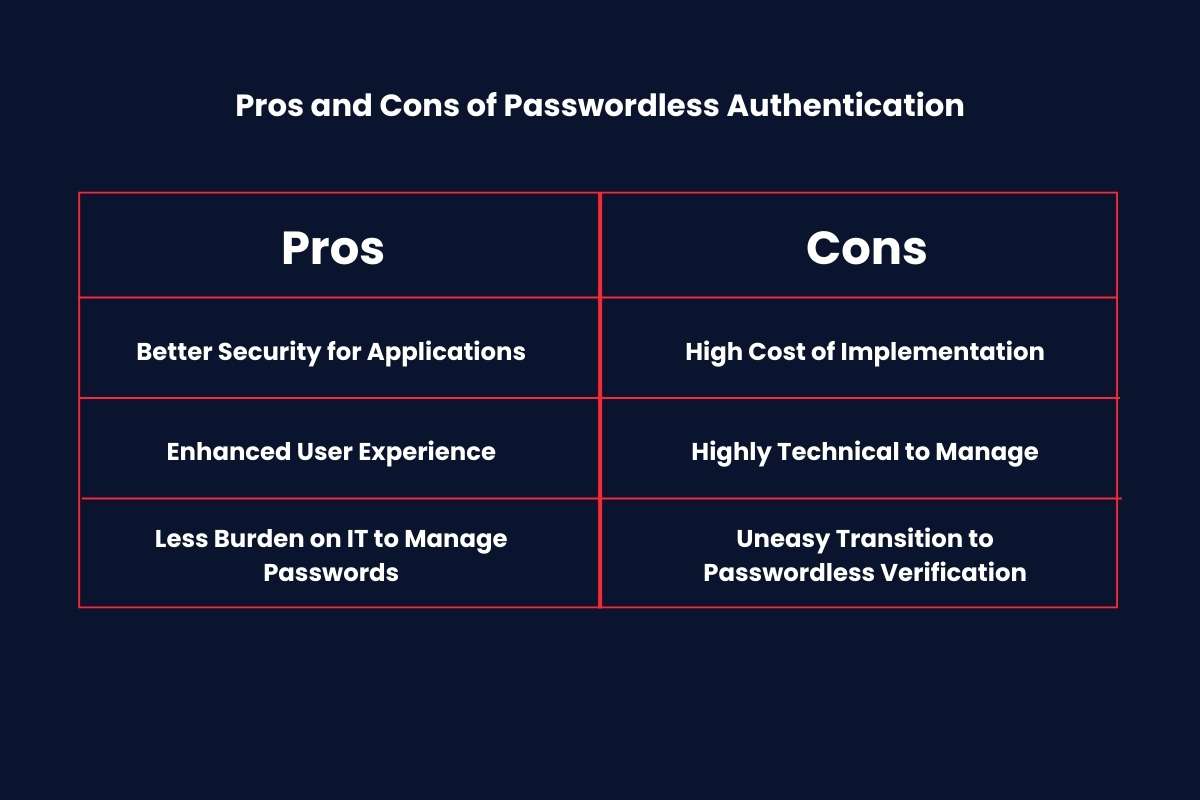
| Pros | Cons |
| Better Security for Applications | High Cost of Implementation |
| Enhanced User Experience | Highly Technical to Manage |
| Less Burden on IT to Manage Passwords | Uneasy Transition to Passwordless Verification |
Pros
1. Better Security:
Passwords are responsible for the majority of cyberattacks. According to Microsoft, there are over 18 million password attacks per year. By implementing alternatives to passwords, your application has better defenses against outside forces.
2. Enhanced User Experience:
People often forget their passwords. Having to constantly reset them can be frustrating. Going passwordless can circumvent the need for passwords and the downside that comes with them.
3. Less Burden of IT:
Using passwordless verification in the workplace can reduce the burden that lies on the IT department. This is because they are the ones responsible for ensuring high levels of security.
Cons
1. Costs:
Many passwordless authentication systems rely on hardware that does not come cheaply. This is true especially for security keys and their management. Many times, upgrades are required for employee devices as well
2. Highly Technical:
Maintaining such systems can be complicated at times. Many IT teams who have experience with password-based systems might find it difficult to manage a passwordless one.
3. Uneasy Transition:
Even if passwords have their shortcomings, most people are used to how passwords work. So, they might not be familiar with passwordless forms of identification. Hence, they might need time to transition to the modern passwordless environment.
Conclusion:
Securing your digital assets is of paramount importance today. But just as the digital landscape has evolved, so have the security measures. Now, you don’t always need a guard at the gate asking for passwords. And even though passwordless authentication has its drawbacks, you cannot deny that it is a step in the right direction. At the end of the day, it is paving the way for higher forms of cybersecurity.






