What happens when the network itself becomes the battlefield?
In 2021, a European smart factory experienced a minor glitch; automated forklifts briefly malfunctioned, delaying operations by only 47 minutes. But the root cause? A vulnerability in its newly deployed 5G edge network was exploited by a rogue device. The incident didn’t just cost thousands in lost productivity; it exposed the invisible war playing out across our digital future.
Welcome to the high-stakes world of 5G network security, where milliseconds matter, billions of devices communicate, and trust must be engineered into every connection. Unlike 4G, 5G isn’t just faster; it’s smarter, denser, and deeply integrated into critical systems like healthcare, transportation, and defense. But every leap in innovation also opens new attack surfaces.
In this dive, we explore how 5G network security is being redefined through real-world applications, industry challenges, and strategic solutions that blend zero trust architecture, cloud-native controls, and AI-powered resilience.
What is 5G Network Security?
5G network security refers to the strategies, technologies, and policies that protect 5G infrastructure, data traffic, applications, and users from cyber threats. Because 5G is software-defined and cloud-based, it introduces more flexibility, but also more exposure. Traditional perimeter-based protections used in 4G no longer apply.
Why This Matters: A study from the World Economic Forum predicts that by 2030, over 50 billion devices will be connected to the internet, many over 5G. Each device represents a potential attack vector.
5G security must protect:
- Physical and virtual infrastructure
- User and control plane data
- Edge computing and IoT devices
- Network slices tailored to specific industries or use cases
Security in 5G spans from the hardware level all the way up to the application layer, across hybrid environments and multiple vendors.
What Needs Protection?
A 5G network security involves three critical layers:
1. Infrastructure:
Physical towers, edge devices, and virtual machines.
2. Traffic:
Both user data and signaling information.
3. Endpoints:
Everything from smartphones to IoT sensors.
Each layer requires tailored protection strategies. For example, edge nodes need real-time threat detection with minimal latency, while cloud VMs need zero-trust access policies.
5G vs. 4G: What’s the Difference in Security?
4G networks relied on centralized, hardware-based models with closed interfaces. Security was easier to standardize. In contrast, 5G introduces disaggregation, virtualization, and distributed cloud-native environments, which expand the attack surface.
| Feature | 4G | 5G |
| Architecture | Centralized | Distributed, Cloud-native |
| Core Functions | Hardware-based | Virtualized (VMs & containers) |
| Interfaces | Vendor-locked | Open, interoperable |
| Traffic Flow | Predictable paths | Dynamic & software-defined |
| Threat Exposure | Limited | Increased due to open access & multiple domains |
Top 5G Network Security Risks to Watch
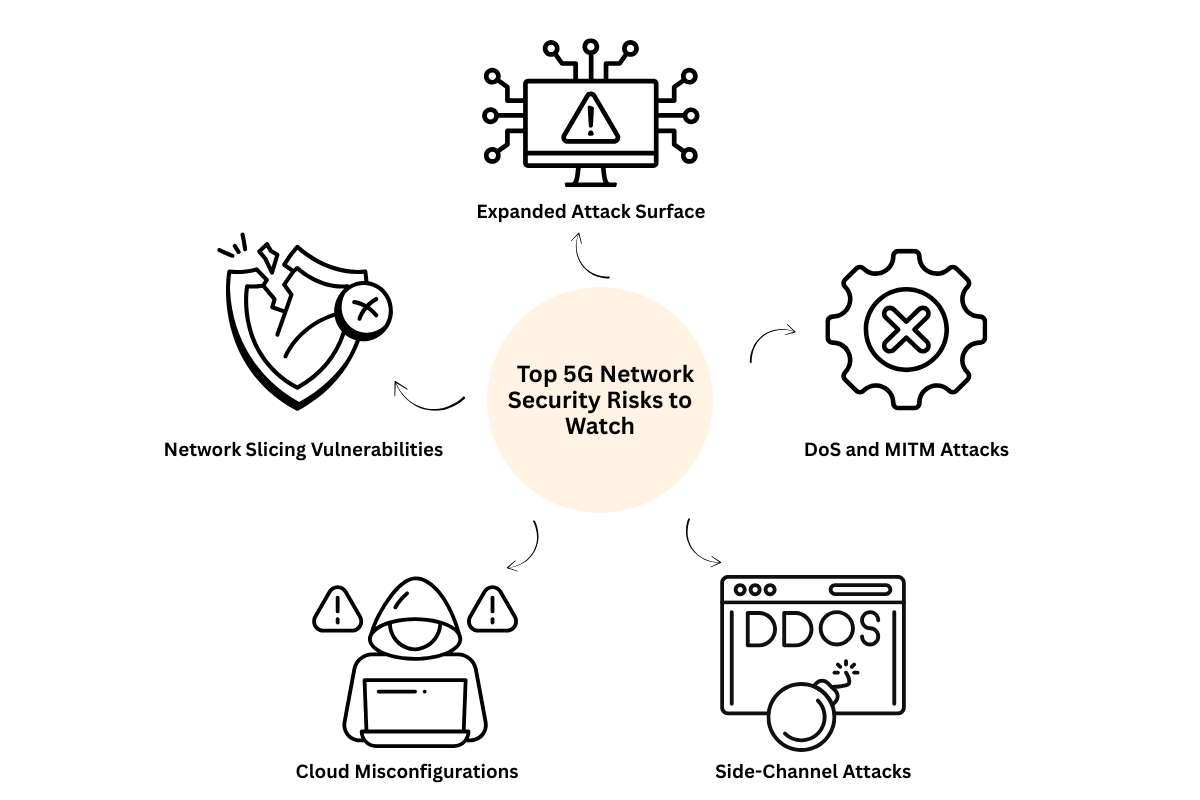
1. Expanded Attack Surface
With millions of devices, virtual functions, and edge deployments, attackers have more opportunities to exploit weak points.
2. Network Slicing Vulnerabilities
Each slice has different configurations and policies. A misconfigured slice can allow lateral movement across services.
3. Cloud Misconfigurations
5G heavily relies on public and hybrid clouds. Misconfigured APIs or containers are easy entry points for hackers.
4. Side-Channel Attacks
Attackers can harvest information using non-traditional channels—like analyzing power usage or timing behaviors in edge devices.
5. DoS and MITM Attacks
Denial-of-service attacks can overload APIs or RAN channels. Meddler-in-the-middle attacks can intercept and manipulate traffic.
“Security in 5G isn’t about building walls; it’s about enabling visibility, policy automation, and zero trust at scale.” — Dan Beaman, Director of 5G Security, Palo Alto Networks
Built-In Security Features of 5G
5G comes with native security mechanisms structured around four main domains:
1. Network Access Security:
Stronger mutual authentication between devices and networks. IMSI is concealed to prevent tracking.
Also read :- Network Security vs. Cybersecurity: Are They the Same?
2. Network Domain Security:
Encryption and integrity protection for virtual functions and service interfaces.
Also Read :- Navigating Cyber Security Earnings: Strategies for Maximizing Income
3. User Domain Security:
Flexible authentication and identity management across devices and third parties.
4. Application Domain Security:
Secure communication between apps, cloud services, and user equipment.
While these features offer a strong baseline, implementation is key; not all features are mandatory or consistently applied.
Benefits of 5G Network Security

Securing a 5G network not only prevents attacks but also enables transformational capabilities:
1. Trusted Smart Cities:
Secure data flows between traffic systems, surveillance, public Wi-Fi, and emergency services.
2. Safe Remote Healthcare:
Ensure medical data and real-time diagnostics are encrypted and authentic.
3. Industrial IoT Integrity:
Prevent manipulation of sensors, robotics, and control systems in smart factories.
4. Reliable Autonomous Systems:
Protect communications in self-driving cars, drones, and critical logistics.
5. Resilience for National Infrastructure:
Secure energy grids, defense systems, and telecommunications.
Real-World Applications of 5G Security
1. Verizon’s 5G Edge for Logistics
Verizon launched its 5G Edge service with Amazon Wavelength, enabling logistics hubs to process data with ultra-low latency. Security mechanisms include container-level access control and encrypted edge-to-core communication.
2. SK Telecom’s 5G + AI Security
SK Telecom integrates AI with 5G security monitoring. It detects anomalies in real-time and adapts policies dynamically across network slices.
3. US DoD’s 5G Smart Warehouse
The U.S. Department of Defense implemented a private 5G network in a warehouse. The network is segmented, encrypted, and monitored continuously through an AI-based SOC.
Who’s Responsible for 5G Security?
Security responsibility is shared:
1. Telecom Providers:
Secure the infrastructure, core, and access networks.
2. Enterprises:
Secure applications, endpoints, and slices they operate.
3. Governments:
Enforce compliance, develop threat models, and define best practices (e.g., NIST, CISA).
4. Vendors:
Build interoperable and secure components.
“The reality is, the cloud changed the game—and 5G pushes it even further. Shared security models now rule.” — Senthil Ramakrishnan, AT&T
Securing Critical Environments

1. Private 5G Networks
Deployed by factories, hospitals, and campuses. Security must include:
- Access control by device type
- Application-aware traffic policies
- Physical and virtual isolation
2. Smart Cities
Require protection across connected transportation, surveillance, and utilities. Threats can ripple across services.
3. Defense and Utilities
Government use of 5G must include identity verification, zero trust policies, and secure slicing.
What’s Next in 5G Security?
- AI-Powered Threat Detection: Real-time adaptive policies based on behavioral insights
- Slice-Aware Policies: More granular controls per network slice and use case
- 5G-Specific SOCs: Operational models built to monitor distributed, latency-sensitive environments
- Global Security Standards: ITU, 3GPP, and other bodies shaping interoperability and trust
Looking ahead, 6G will intensify these trends, and security by design will become more critical than ever.
Conclusion:
Speed alone won’t win the future; security will.
As 5G transforms into the digital nervous system of our modern world, securing it is no longer optional but existential. Whether it’s a drone navigating a dense urban corridor, a surgeon operating remotely, or a utility grid managing national power, 5G network security stands at the core of reliability, safety, and innovation.
We’ve seen how vulnerabilities, from misconfigured cloud interfaces to lateral threats across network slices, can shake systems at scale. But we’ve also seen how enterprises like Verizon, SK Telecom, and the U.S. Department of Defense are pioneering smarter, adaptive security frameworks tailored to 5G’s complexity.
This isn’t just a tech challenge. It’s a leadership opportunity.
The organizations that build security into the DNA of their 5G deployments today will lead the digital economy tomorrow. Because in the age of 5G, you’re not just protecting data, you’re protecting lives, industries, and trust.






