The United States stands at the forefront of global FinTech innovation, with a dynamic ecosystem encompassing everything from challenger banks and digital payment solutions to algorithmic trading platforms and blockchain-based financial services. This rapid evolution, however, has also made US FinTech companies uses best cybersecurity tools for companies & its prime targets for increasingly sophisticated cyber threats. The sheer volume of sensitive financial and personal data handled by these firms, combined with the interconnectedness of modern financial systems, elevates cybersecurity from a mere IT concern to a fundamental business imperative.
US FinTechs face a complex threat landscape, including persistent and evolving risks such as ransomware attacks, phishing and social engineering, data breaches, insider threats, and vulnerabilities in APIs and third-party integrations. Moreover, the with the best cybersecurity tools for companies n the US is multifaceted and stringent.
Key regulations and frameworks influencing FinTech cybersecurity include:

1. Gramm-Leach-Bliley Act (GLBA):
Mandates financial institutions to explain their information-sharing practices to customers and safeguard sensitive data.
2. Sarbanes-Oxley Act (SOX):
While primarily focused on financial reporting, SOX indirectly impacts cybersecurity by requiring robust internal controls, including those related to IT systems and data security for publicly traded companies.
3. New York Department of Financial Services (NYDFS) Cybersecurity Regulation (23 NYCRR Part 500):
A highly influential regulation that applies to any financial institution operating under NYDFS licensure, requiring comprehensive cybersecurity programs, risk assessments, and incident response plans.
4. Securities and Exchange Commission (SEC) Cybersecurity Rules:
Mandates public companies to disclose material cybersecurity incidents within four business days and provides detailed disclosures on cybersecurity risk management and governance.
5. NIST Cybersecurity Framework (CSF):
While voluntary, the NIST CSF provides a widely adopted set of guidelines and best practices for managing cybersecurity risk, particularly for critical infrastructure sectors, including financial services.
6. Payment Card Industry Data Security Standard (PCI DSS):
A mandatory standard for organizations that process, store, or transmit credit card data.
7. State-specific data privacy laws:
Such as the California Consumer Privacy Act (CCPA), which imposes strict requirements on the handling of consumer data.
To navigate this intricate web of threats and regulations, US FinTech companies must deploy a comprehensive arsenal of best cybersecurity tools . This article outlines the best cybersecurity tools essential for building a resilient and secure FinTech operation in the United States.
Best Cybersecurity Tools for Companies
1. Identity and Access Management (IAM)
Effective IAM is the cornerstone of FinTech security, controlling who can access what, when, and how. Given the diverse range of internal users, external partners, and customer interactions, robust IAM is non-negotiable.
> Multi-Factor Authentication (MFA) and Adaptive Authentication:
Beyond simple passwords, MFA requires users to verify their identity through multiple methods (e.g., password + biometric, security token, or mobile app push notification). Adaptive authentication takes this further by dynamically adjusting the level of authentication based on risk factors like user location, device, and behavior. This is crucial for NYDFS compliance, which mandates strong authentication for accessing non-public information.
> Role-Based Access Control (RBAC):
Implementing RBAC ensures that employees only have the minimum necessary access to systems and data required for their job functions (principle of least privilege). This significantly reduces the attack surface and potential damage from compromised accounts.
> Privileged Access Management (PAM):
PAM solutions are designed to secure, manage, and monitor privileged accounts (e.g., administrator accounts) that have elevated access rights. These accounts are prime targets for attackers, and PAM helps prevent misuse and provides detailed audit trails.
> User Behavior Analytics (UBA):
UBA tools leverage AI and machine learning to analyze user activity patterns and identify anomalous behavior that could indicate a compromised account or insider threat.
Key Tools: Okta, SailPoint, CyberArk, Microsoft Azure Active Directory, Ping Identity, Duo Security.
2. Data Loss Prevention (DLP) and Encryption
Protecting sensitive financial data, customer PII (Personally Identifiable Information), and proprietary information is paramount for US FinTechs, particularly due to GLBA and state-specific privacy laws.
> Data Loss Prevention (DLP) Solutions:
DLP tools are designed to monitor, detect, and prevent sensitive data from leaving the organization’s control. They can identify specific types of confidential information (e.g., Social Security numbers, credit card details) and block their unauthorized transmission via email, cloud storage, or removable media. Advanced DLP solutions utilize content inspection, contextual analysis, and machine learning for accurate detection.
> Data Encryption:
All sensitive data, both at rest (stored on servers, databases, endpoints) and in transit (during transmission over networks, APIs), must be encrypted using strong, industry-standard algorithms (e.g., AES-256 for data at rest, TLS 1.3 for data in transit). So It is a best cybersecurity tools Many compliance frameworks, including NYDFS, explicitly require encryption for non-public information .
Key Tools: Symantec DLP, Forcepoint DLP, McAfee DLP, Digital Guardian, Proofpoint.
3. API Security Solutions
FinTech companies heavily rely on Application Programming Interfaces (APIs) for interoperability, integrating with payment processors, data providers, and other financial services. Unsecured APIs are a significant vulnerability.
> API Gateway and Firewall:
An API gateway acts as a central entry point for all API traffic, enforcing security policies, performing authentication and authorization, and rate limiting requests. An API firewall specifically protects APIs from various attacks, including those listed in the OWASP API Security Top 10.
> API Security Testing (DAST, SAST, IAST):
Integrating security testing into the Secure Software Development Life Cycle (SSDLC) is crucial. Dynamic Application Security Testing (DAST) tests APIs in a running state, identifying runtime vulnerabilities. Static Application Security Testing (SAST) analyzes source code for flaws during development. Interactive Application Security Testing (IAST) combines elements of both.
> Runtime API Protection:
These solutions provide real-time protection by monitoring API traffic for malicious activity and automatically blocking attacks. They often leverage AI and machine learning to detect anomalous behavior and respond proactively.
Key Tools: Akamai API Security, Salt Security, Noname Security, Cequence Security, Cloudflare API Shield.
4. Fraud Detection and Prevention Tools
Given the transactional nature of FinTech, robust fraud detection and prevention mechanisms are essential for protecting both the company and its customers from financial losses and reputational damage.
> AI/ML-powered Fraud Detection:
Artificial Intelligence and Machine Learning algorithms can analyze vast datasets of transaction information, user behavior, and historical patterns in real-time to identify and flag suspicious activities indicative of fraud. These systems continuously learn and adapt to new fraud schemes.
> Behavioral Biometrics:
These technologies analyze unique user behaviors (e.g., typing patterns, mouse movements, device usage) to verify identity and detect anomalies that might signal an account takeover attempt or synthetic identity fraud.
> Transaction Monitoring Systems:
These systems continuously track and analyze financial transactions for signs of fraud, money laundering, or other illicit activities, often incorporating rules-based engines alongside AI/ML capabilities.
> Know Your Customer (KYC) and Anti-Money Laundering (AML) Solutions:
While not solely best cybersecurity tools, robust KYC and AML processes are foundational for fraud prevention and compliance with regulations like the Bank Secrecy Act (BSA). They involve verifying customer identities and monitoring transactions to prevent financial crime.
Key Tools: Feedzai, SEON, LexisNexis Risk Solutions, FICO Falcon Platform, Verafin.
5. Security Information and Event Management (SIEM) & Security Orchestration, Automation, and Response (SOAR)
Centralized visibility, threat intelligence, and rapid incident response are critical for US FinTechs navigating complex regulatory landscapes and sophisticated attacks.
> SIEM:
SIEM solutions collect, aggregate, and analyze security logs and event data from various sources across the IT infrastructure (networks, servers, applications, security devices). They use correlation rules and advanced analytics to identify potential threats, generate alerts, and provide a holistic view of the security posture.
> SOAR:
SOAR platforms automate and orchestrate incident response workflows. They integrate with various security tools, enabling automated actions such as blocking malicious IPs, isolating compromised endpoints, or enriching alerts with threat intelligence. SOAR helps reduce manual effort, improve response times, and ensure consistent incident handling, crucial for SEC and NYDFS incident reporting requirements.
> User and Entity Behavior Analytics (UEBA):
Often integrated with SIEM, UEBA focuses on profiling the normal behavior of users and entities to detect subtle deviations that could indicate insider threats or targeted external attacks.
Key Tools: Splunk Enterprise Security, IBM QRadar, Microsoft Sentinel, Exabeam, Securonix, Palo Alto Networks Cortex XSOAR.
6. Vulnerability Management and Penetration Testing

Proactive identification and remediation of security weaknesses are essential for maintaining a strong security posture and adhering to frameworks like NIST CSF and NYDFS.
> Vulnerability Assessment (VA) Tools:
VA tools scan systems, applications, and networks for known vulnerabilities, providing a prioritized list of weaknesses based on severity and exploitability.
> Penetration Testing (Pentest) Services:
Penetration testing simulates real-world cyberattacks to identify exploitable vulnerabilities and assess the effectiveness of existing security controls. Regular, independent penetration testing for web applications, mobile applications, cloud infrastructure, and APIs is crucial for FinTechs. Many reputable firms specialize in these services for the US market.
> Attack Surface Management (ASM):
ASM tools continuously discover and monitor an organization’s digital assets (both known and unknown) to identify and manage external attack surfaces and potential entry points for attackers.
> Secure Software Development Life Cycle (SSDLC) Tools:
Integrating security into every stage of software development, from design to deployment, helps build secure applications from the ground up. This includes using tools for secure code analysis (SAST, DAST, IAST) and software composition analysis (SCA) to identify vulnerabilities in open-source components.
Key Tools: Tenable Nessus, Qualys, Rapid7 InsightVM (for VA), HackerOne, Bugcrowd (for bug bounty programs and pentesting services), Synopsys, Checkmarx (for SSDLC).
7. Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platforms (CWPP)
Given the prevalent adoption of cloud services (AWS, Azure, GCP) by US FinTechs, dedicated cloud security tools are non-negotiable.
> CSPM:
CSPM solutions continuously monitor cloud environments to identify misconfigurations, compliance violations (e.g., against CIS Benchmarks or custom policies), and security risks across various cloud services. They help ensure adherence to regulatory requirements and best practices.
> CWPP:
CWPPs protect workloads (virtual machines, containers, serverless functions) running in the cloud. They provide threat detection, vulnerability management, and runtime protection for cloud-native applications, regardless of their underlying infrastructure.
> Cloud Access Security Brokers (CASB):
CASBs act as a security policy enforcement point between cloud service users and cloud service providers, extending security controls to SaaS applications. They help enforce data security, compliance, and threat protection for cloud-based data.
Key Tools: Palo Alto Networks Prisma Cloud, CrowdStrike Falcon Cloud Security, Wiz, Orca Security, Zscaler (for CASB).
8. Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR)
Endpoints (laptops, desktops, mobile devices) remain frequent entry points for cyberattacks. EDR and XDR solutions provide advanced threat detection and response capabilities for these devices and beyond.
> EDR:
EDR tools monitor endpoint activity for suspicious behaviors that might indicate malware, ransomware, fileless attacks, or other advanced threats. They offer visibility into endpoint events and enable automated response actions like threat containment and device isolation.
> XDR:
XDR takes EDR a step further by integrating security data from multiple sources across the IT stack (endpoints, networks, cloud, email, identity) to provide a more holistic view of threats and enable correlated detection and response. This is particularly valuable for complex, multi-stage attacks.
Key Tools: CrowdStrike Falcon, SentinelOne, Microsoft Defender for Endpoint, Trend Micro Apex One, Cortex XDR (Palo Alto Networks).
9. Web Application Firewall (WAF)
Web applications are often the primary interface for FinTech services and are frequently targeted by attackers. A robust WAF is essential.
> WAF:
A WAF protects web applications from various attacks, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and other OWASP Top 10 vulnerabilities. It inspects HTTP traffic and filters out malicious requests before they reach the application.
Key Tools: Cloudflare WAF, Akamai Kona Site Defender, F5 Advanced WAF, Imperva, AWS WAF.
10. Cyber Insurance
While not a direct cybersecurity tool, cyber insurance is a crucial risk management strategy for FinTech companies in the US, providing a financial safety net in the event of a cyber incident.
> Financial Coverage:
Cyber insurance policies can cover various costs associated with a cyberattack, including legal expenses, regulatory fines, data breach notification costs, forensic investigation fees, business interruption losses, and even ransomware payments.
> Incident Response Support:
Many policies offer access to pre-approved incident response services, including cybersecurity legal counsel, forensic investigators, and public relations specialists, which can be invaluable during a crisis.
Key Providers in the US: Chubb, AIG, Travelers, Beazley, Coalition, At-Bay.
Building a Resilient FinTech Security Posture of Best Cybersecurity Tools
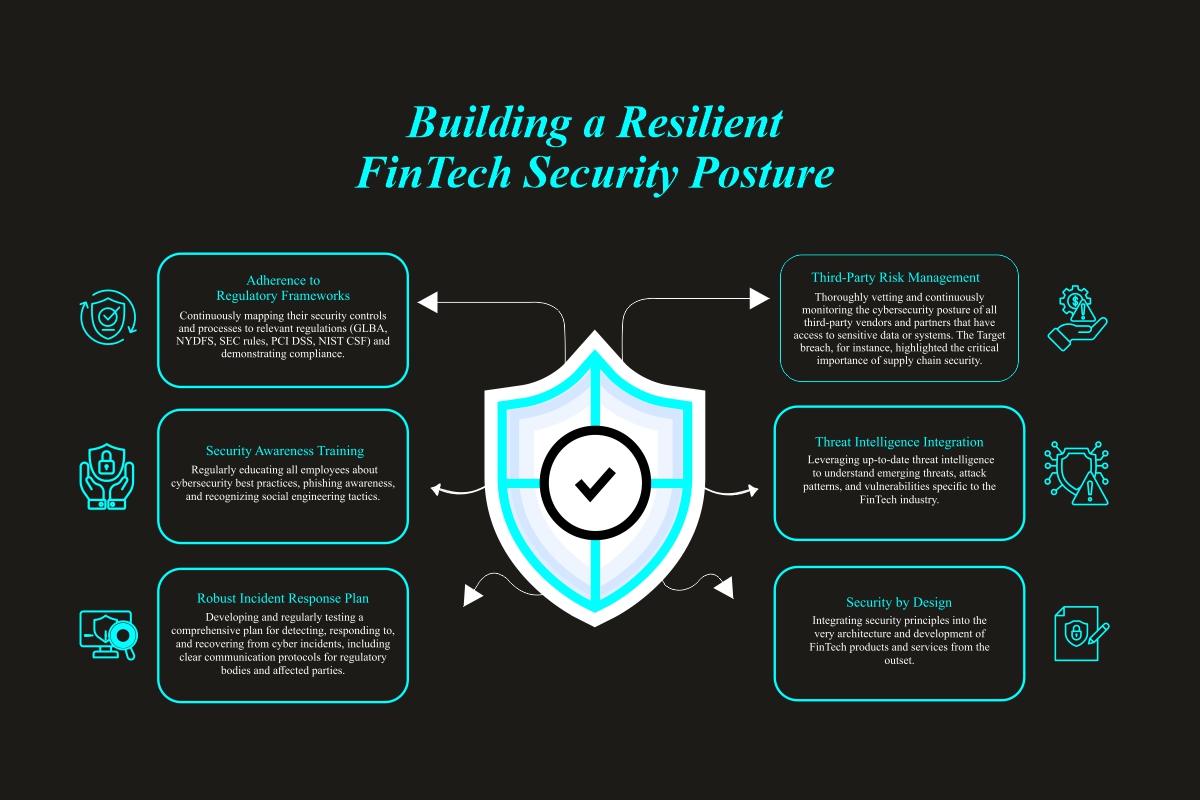
Selecting the right and best cybersecurity tools is merely one component of a robust security strategy. US FinTech companies must also prioritize:
1. Adherence to Regulatory Frameworks:
Continuously mapping their security controls and processes to relevant regulations (GLBA, NYDFS, SEC rules, PCI DSS, NIST CSF) and demonstrating compliance.
2. Security Awareness Training:
Regularly educating all employees about cybersecurity best practices, phishing awareness, and recognizing social engineering tactics.
3. Robust Incident Response Plan:
Developing and regularly testing a comprehensive plan for detecting, responding to, and recovering from cyber incidents, including clear communication protocols for regulatory bodies and affected parties.
4. Third-Party Risk Management:
Thoroughly vetting and continuously monitoring the cybersecurity posture of all third-party vendors and partners that have access to sensitive data or systems. The Target breach, for instance, highlighted the critical importance of supply chain security.
5. Threat Intelligence Integration:
Leveraging up-to-date threat intelligence to understand emerging threats, attack patterns, and vulnerabilities specific to the FinTech industry.
6. Security by Design:
Integrating security principles into the very architecture and development of FinTech products and services from the outset for best cybersecurity tools.
The US FinTech landscape is characterized by its innovation and rapid evolution. However, this dynamism must be underpinned by an unwavering commitment to cybersecurity. By strategically implementing a layered defense using the best cybersecurity tools and fostering a strong security culture, FinTech companies in the USA can effectively mitigate risks, protect sensitive data, maintain customer trust, and ensure their continued growth and success in the digital economy.






